










Now Is Not the Time to Upgrade Your iPhone The imminent arrival of Apple’s iPhone 16 in September warrants careful consideration before committing to an iPhone...



In an age where artificial intelligence is rapidly becoming the centerpiece of technological advancements, it’s easy to become jaded by the constant barrage of AI integrations...



The World Health Organization has declared MPox a global health emergency, as two more virulent and lethal variants, Clade 1 and Clade 2, continue to circulate...
Security experts have recently uncovered critical vulnerabilities within Amazon Web Services (AWS) that could expose sensitive data and compromise cloud infrastructure. These flaws, identified in AWS’s...



Microsoft has recently issued a critical warning regarding a significant vulnerability in Microsoft Office that remains unpatched. This flaw, identified in Office’s handling of certain documents,...
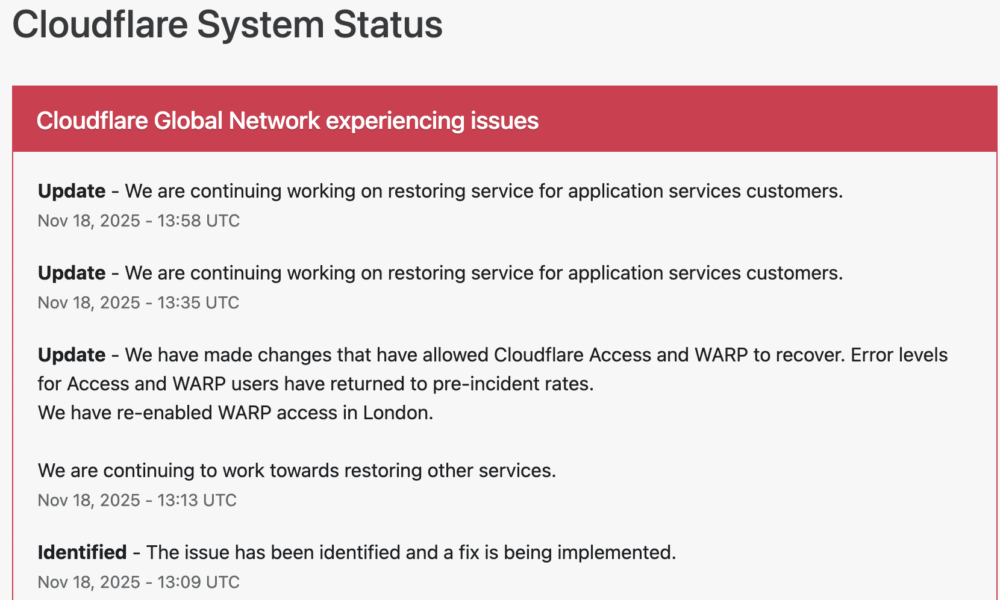
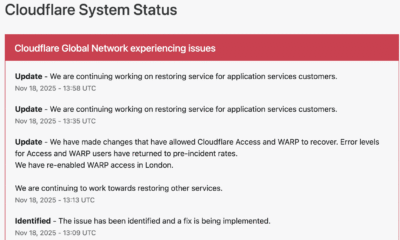

SAN FRANCISCO, CA — A widespread disruption across major internet services, including AI platform ChatGPT and social media giant X (formerly Twitter), has drawn critical attention...
Rabat — October 2025Inside Morocco’s Parliament, tension and reflection filled the air just hours after His Majesty King Mohammed VI delivered his opening-session speech. What was...

Dassault Systèmes patches severe vulnerability in Apriso manufacturing software that could let attackers bypass authentication and compromise factories worldwide. A newly disclosed flaw, tracked as CVE-2025-5086,...



CERT-FR and Apple warn of sophisticated spyware targeting iCloud-linked devices via zero-click exploits; high-profile individuals at risk. Apple and France’s CERT-FR have issued a fourth spyware...



Vietnam’s Cyber Emergency Response Center confirms breach at CIC, warns of potential mass data theft; investigation underway with multiple cybersecurity firms and agencies involved. Vietnam’s National...



Attackers deploy GPU-aware malware that evades sandboxes and steals sensitive data Hackers are abusing Google search ads to trick developers into downloading fake GitHub tools packed...

Hackers exploited an external system linked to Chess.com, compromising personal information; the Utah-based company notified victims nearly three months later. Chess.com confirmed a major security incident...



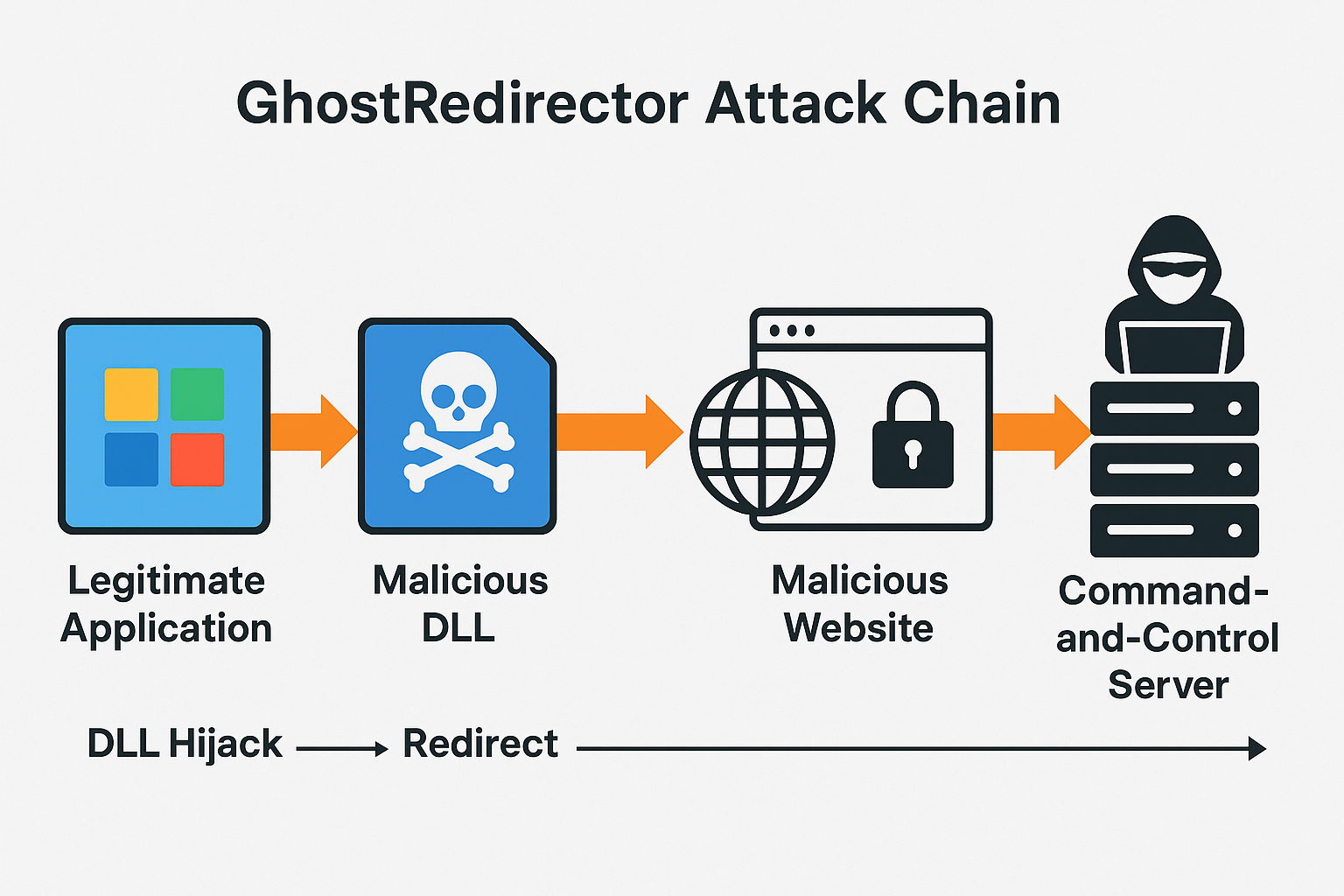
Cybercriminals abuse trusted Windows executables to redirect users, spread malware, and harvest sensitive data. A new malware campaign dubbed GhostRedirector has compromised more than 65 legitimate...



Wiz Research finds an exposed ClickHouse database with 1M+ log lines, including chat histories and secrets—spotlighting human error, weak access controls, and the need for DLP....



Tata Motors’ luxury brand shuts global IT systems amid suspected ransomware attack; no customer data reported compromised. Jaguar Land Rover has shut down production and retail...