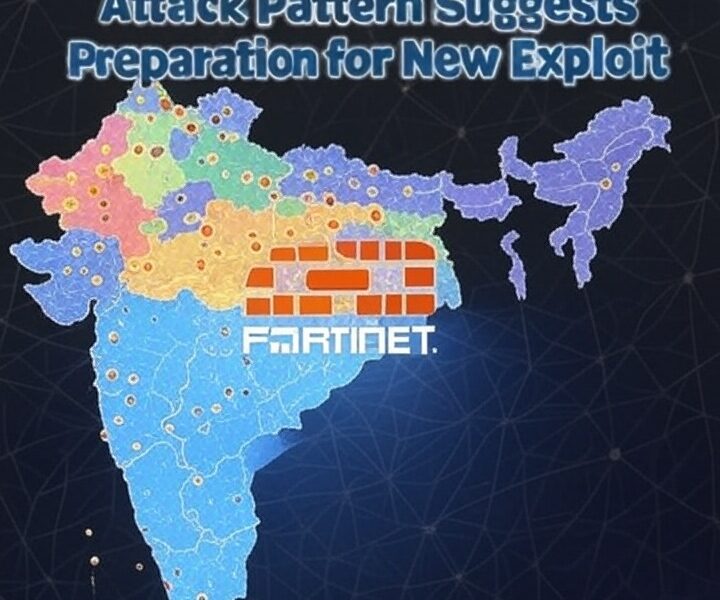

Cyber threat actors orchestrated a massive, two-wave brute-force assault on Fortinet SSL VPNs, shifting mid-campaign to FortiManager—raising alarm as such patterns often precede critical CVE disclosures....



Morocco’s Directorate General of Information Systems Security (DGSSI) issues a dire warning: a zero-day vulnerability in WinRAR is being actively exploited, putting countless users at risk...



In a precision cyber strike, Kyiv’s defense intelligence infiltrated a top-tier private ISP serving Russian security agencies—raising stakes far beyond the digital realm. When the hum...



Fresh vulnerabilities in the TETRA standard allow attackers to replay calls, brute-force encryption, and inject fake voice/data—even on “secure” networks. No universal fixes exist, leaving critical...


A zero-day flaw (CVE-2025-8088) is under active attack by Russian-linked groups Paper Werewolf and RomCom. Booby-trapped archives can plant malware in Windows startup folders—silently hijacking your...



The unauthorized access was first identified on Saturday, August 9, 2025, through UWA’s security monitoring systems, which flagged suspicious activity targeting the university’s authentication infrastructure. This...



Strategic Project to Boost Trade and Land Connectivity Across West Africa with Chinese Financing Ouagadougou – From Our International CorrespondentIn what is being hailed as a...
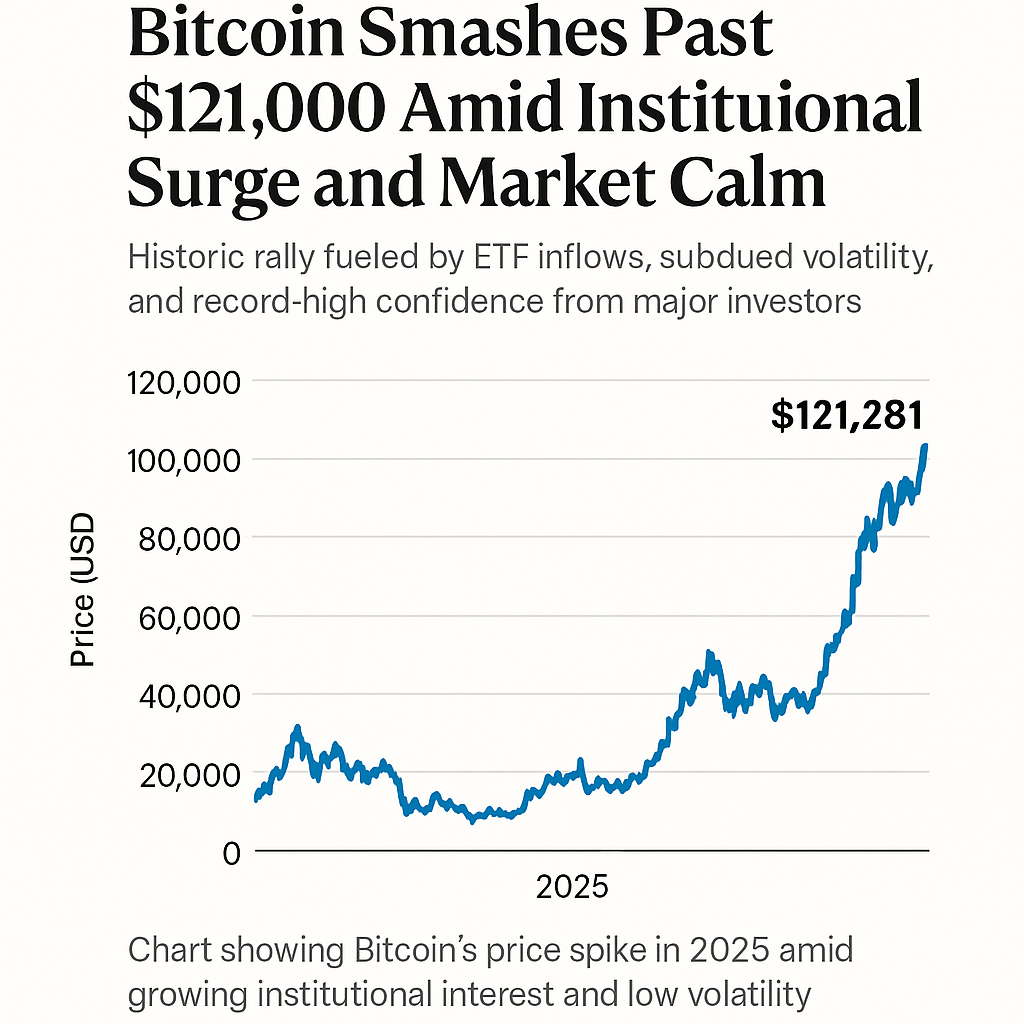


Historic rally fueled by ETF inflows, subdued volatility, and record-high confidence from major investors. In a landmark moment for the cryptocurrency market, Bitcoin has shattered the...



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...



A declassified French intelligence telegram reveals covert cooperation between Algiers and Madrid in the tense months following Algerian independence—raising new questions about Cold War geopolitics in...