


New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...


Malicious apps disguised as utility tools rake in hidden subscription fees, spam users relentlessly, and harvest personal data—millions of installs and growing exposes a broader mobile...



Cybercrime syndicate UNC6040 used spoofed IT helpdesk calls and legitimate remote access tools to infiltrate corporate environments—Google TAG reveals ongoing threat to global organizations. SEO-Optimized Excerpt:Google’s...



Milford Management, owner of high-end Battery Park City properties, was duped by a single phishing email—triggering a $19 million transfer to scammers posing as the Battery...


System and Qualcomm GPU vulnerabilities allowed silent device compromise. Google’s patch blocks zero-day exploits affecting millions of Android users. Mountain View / Global – August 5,...



Despite national reforms and global ambitions, many Moroccan businesses still reject bank card payments — undermining efforts toward financial inclusion and digital readiness. Experts call for...


In a televised statement, Panama’s Foreign Minister calls Morocco’s 2007 autonomy initiative the “only credible and applicable solution” for the Sahara conflict — reinforcing growing international...
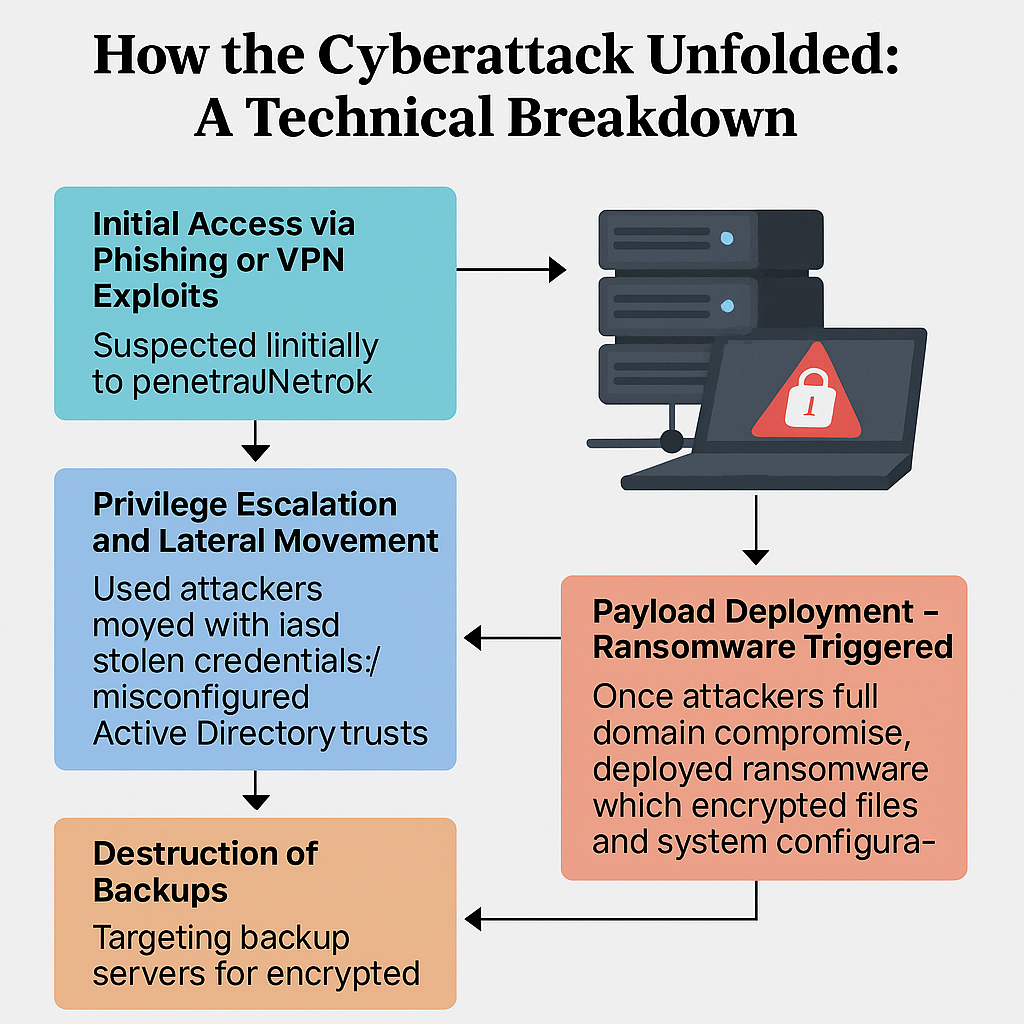


Cybercriminals cripple tax and court systems in Curaçao, Aruba, and Sint Maarten using sophisticated multi-vector ransomware; experts say outdated defenses made critical systems vulnerable. A wave...



Health officials scramble to contain a rapidly escalating mosquito-borne virus as China battles its largest Chikungunya outbreak in years. By El Mostafa Ouchen | MAG212NEWS Beijing,...



Multiple high-severity vulnerabilities in NVIDIA’s Triton Inference Server could allow unauthenticated attackers to execute remote code, compromise AI models, and disrupt production environments. NVIDIA Triton AI...