International
EU to Impose First Sanctions on Iran Over Missile Transfers to Russia: A New Phase of Diplomatic Strains

In a significant move, the European Union is set to impose its first-ever sanctions on Iran in response to the transfer of missiles to Russia. This decision marks a turning point in the relationship between Iran and the EU, adding new layers of complexity to an already tense geopolitical landscape shaped by the ongoing war in Ukraine.
What Happened?
According to a report by Reuters, the EU’s decision stems from confirmed intelligence that Iran has been supplying Russia with missiles. These weapons are believed to have been used by Russian forces in Ukraine, intensifying an already devastating conflict that has drawn in various international powers.
For months, Western officials have raised concerns about the close military cooperation between Tehran and Moscow, particularly after reports of Iranian-made drones being used by Russian forces surfaced earlier this year. However, the missile transfers mark a more direct and alarming escalation in this military alliance, prompting the EU to act.
Why Is This Important?
The sanctions represent a significant shift in how the EU approaches Iran. While sanctions have previously targeted Iran’s nuclear program and human rights issues, this marks the first time the EU is penalizing Iran specifically for its military support of Russia. The implications of this are profound, as it directly links Iran to the conflict in Ukraine and aligns EU policy more closely with that of the U.S., which has already imposed heavy sanctions on Iran for similar reasons.
From a geopolitical standpoint, the sanctions could have far-reaching consequences. They not only signal the EU’s firm stance against external support for Russia in its war against Ukraine but also indicate that Iran’s involvement in the conflict will no longer be tolerated without significant repercussions.
What Are the Sanctions?
While the full scope of the sanctions is yet to be detailed, they are expected to target both individuals and entities involved in the missile transfers. This could include high-ranking Iranian officials, military leaders, and companies responsible for producing and exporting the missiles. The sanctions are likely to involve asset freezes, travel bans, and restrictions on doing business with these individuals or organizations within EU borders.
It’s also possible that the sanctions could extend to broader economic sectors, impacting Iran’s defense industry and further isolating Tehran on the world stage. Iran, already under heavy sanctions from both the U.S. and the UN over its nuclear program, faces increasing economic and diplomatic pressure from this latest move.
What’s at Stake?
The EU’s decision is not without risks. Iran has already denied involvement in the missile transfers, dismissing the claims as politically motivated. Tehran could retaliate by withdrawing from diplomatic talks or by ramping up its missile development program, which would further escalate tensions with the West.
There’s also the potential for increased instability in the Middle East. As Iran faces sanctions, it may turn to other military partners, such as China or North Korea, to strengthen its defense capabilities. This could further complicate global security, especially as these countries have already been criticized for their own military actions and support for authoritarian regimes.
For the EU, these sanctions come at a critical time. With the war in Ukraine showing no signs of abating, European leaders are keen to cut off any external support that could prolong the conflict. By imposing sanctions on Iran, the EU sends a clear message that it will not tolerate the flow of arms into Russia from any country, especially when those weapons are being used in a war that has brought immense suffering to the Ukrainian people.
The Impact on Iran-Russia Relations
For Iran, these sanctions may have little immediate impact on its alliance with Russia, which has only grown stronger in recent months. Both countries have found themselves isolated from much of the international community, with Russia facing sweeping sanctions over its invasion of Ukraine and Iran grappling with economic isolation over its nuclear ambitions. The two nations have found common ground in their shared opposition to Western policies, and this partnership has extended into military cooperation.
The sanctions could, however, strain the relationship if they begin to hurt Iran’s economy or limit its ability to engage with global markets. While Iran has largely weathered years of economic sanctions, additional pressure from the EU could make it more difficult for Tehran to maintain its military partnerships and may prompt it to rethink its role in the Ukraine conflict.
What’s Next?
As the EU finalizes its sanctions, global leaders are watching closely to see how Iran and Russia will respond. If Iran continues to supply Russia with military support, further sanctions could be on the horizon, potentially leading to greater economic isolation for Tehran. Meanwhile, the situation in Ukraine remains dire, with no end to the conflict in sight.
For the EU, this is a bold step that reinforces its commitment to supporting Ukraine and opposing external involvement in the conflict. It’s a signal that the bloc is willing to go beyond traditional diplomatic measures to hold those who support Russia accountable for their actions.
As the conflict unfolds, the global balance of power continues to shift, and the EU’s sanctions on Iran may prove to be a pivotal moment in the broader international response to the Ukraine war.
Conclusion
The EU’s decision to impose sanctions on Iran over missile transfers to Russia adds another layer of complexity to the already volatile situation in Ukraine and the Middle East. With geopolitical tensions running high, this move underscores the EU’s resolve to curb any external military support that might prolong the conflict. However, the fallout from this decision remains uncertain, with potential consequences for Iran’s economy, its relationship with Russia, and the broader global security landscape.
International
New X Feature Reveals Where Users Really Are — And It’s Already Causing Chaos
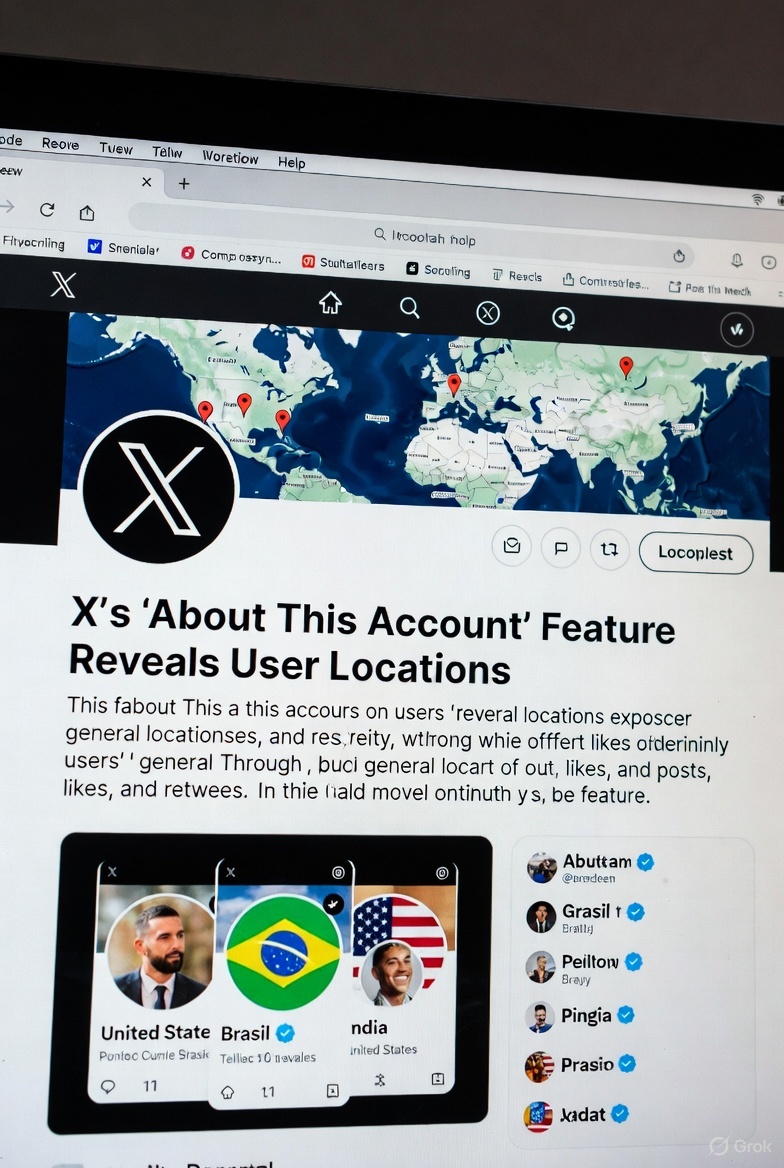
November 25, 2025 – In a move to enhance transparency and curb the spread of bots and foreign influence on its platform, X (formerly Twitter) has launched a new “About This Account” feature that displays the country or region associated with user profiles. The tool, which rolled out widely in recent weeks, allows anyone to quickly check the origin of an account by tapping or hovering over the “Joined” date on a profile page. This comes amid growing concerns over online authenticity, especially in politically charged discussions.The feature pulls data from where the account was created or where it’s primarily active, providing a simple label like “United States” or “Europe.” X owner Elon Musk has touted it as a key step toward building trust, stating on the platform that it helps “expose fake accounts and foreign agitators.” Early adopters have praised it for its role in “instant bot detection,” with users reporting discoveries of profiles masquerading as locals but originating from distant regions.
Rollout and Initial Impact
The “About This Account” section was first tested on X employee profiles in October before a full launch in mid-November. However, the rollout wasn’t without hiccups—X briefly pulled the feature just hours after debut due to immediate backlash over privacy concerns, only to reinstate it shortly after. Since then, it has become a permanent fixture, also revealing additional details such as username change history and any connections to X’s premium services.The tool has already sparked heated debates. Proponents argue it reduces misinformation by highlighting potential foreign meddling; for instance, several accounts promoting political narratives, including pro-Palestinian voices and MAGA supporters, have been exposed as operating from countries like Pakistan, Bangladesh, Israel, or even Gaza—contradicting their portrayed identities. One viral thread highlighted “Gaza journalists” based overseas, fueling discussions about propaganda and influence operations.Critics, however, raise alarms about privacy and potential misuse. Some users worry it could lead to doxxing or harassment, especially for those in sensitive regions. Others note that savvy users might evade detection using VPNs, though X claims it’s refining its algorithms to improve accuracy. In response to feedback, the platform allows users to opt for a broader regional display (e.g., “Asia” instead of a specific country) to balance transparency with privacy.
Broader Implications for Social Media
This feature aligns with X’s ongoing efforts under Musk to prioritize free speech while tackling spam and inauthenticity. It arrives at a time when social platforms face scrutiny from regulators worldwide, including the EU’s Digital Services Act, which demands greater accountability for content moderation. Analysts suggest it could influence competitors like Meta’s Threads or Bluesky to adopt similar tools, potentially reshaping how users verify online identities.As global events like elections and conflicts amplify the role of social media, features like this could play a pivotal role in distinguishing genuine discourse from orchestrated campaigns. “It’s a double-edged sword,” says digital ethics expert Dr. Lena Vasquez in a recent interview. “While it promotes accountability, it also risks oversimplifying complex user behaviors in a borderless internet.”How to Use the “About This Account” FeatureAccessing and utilizing this tool is straightforward, making it accessible for everyday users to verify profiles. Here’s a step-by-step guide:
- View a Profile’s Location:
- Navigate to any user’s profile on X via the web, mobile app (iOS or Android), or desktop.
- Look for the “Joined [Date]” line below the user’s bio and profile picture.
- Tap (on mobile) or hover your cursor (on desktop) over the “Joined” date. A pop-up or expanded section titled “About This Account” will appear, showing the associated country or region.
- Check Additional Details:
- In the same pop-up, you’ll see username history (if changed) and any links to X services, like premium subscriptions.
- This is useful for spotting suspicious accounts—if a profile claims to be from one place but shows another, it might warrant further scrutiny.
- Customize Your Own Display (for Privacy):
- Go to your account settings on X.
- Under “Privacy and Safety,” find the “Account Information” or “Transparency” section (exact labeling may vary by update).
- Toggle the option to show a broader region instead of your specific country. Note: This doesn’t hide the data entirely but generalizes it (e.g., “North America” vs. “Canada”).
- Tips for Effective Use:
- Combine with other verification methods: Check for blue checkmarks (indicating verified status), post history, and engagement patterns.
- Report suspicious accounts via X’s built-in tools if you suspect bots or misinformation.
- Be mindful of privacy—avoid using this to harass others, as X’s policies prohibit doxxing.
While not foolproof, this feature empowers users to make more informed decisions about who they engage with online. As X continues to evolve, expect potential expansions, such as integrating AI-driven authenticity checks. For the latest updates, keep an eye on X’s official announcements or Musk’s posts.
business
Verizon Slashes Jobs in Record-Breaking Layoff — Here’s What We Know

Verizon announced a sweeping workforce reduction that will affect “more than” 13,000 employees — roughly 13% of its global headcount — in what CEO Dan Schulman calls the company’s largest-ever layoff. In an internal memo, Schulman says the move is intended to “simplify our operations to address the complexity and friction that slow us down and frustrate our customers.” The company also plans to cut outsourced and outside labor costs significantly. U.S.-based staff will begin receiving notifications today; employees outside the U.S. will be informed in the “coming weeks,” the Wall Street Journal reports
What Verizon says
- Reason: operational simplification and removing friction that hurts customer experience.
- Scale: “more than” 13,000 roles, about 13% of the workforce.
- Outsourcing: a significant reduction in outsourced and outside labor spending is part of the plan.
- Timing: U.S. notifications begin immediately; international notifications will follow.
Immediate impact
- Employees: tens of thousands will be affected directly or indirectly. U.S. notifications beginning today means many workers will learn their status immediately.
- Operations: Verizon says the goal is to reduce complexity and improve service — but short-term disruption to teams and projects is possible as roles are consolidated.
- Customers: Verizon frames the change as a way to speed decision-making and improve customer experience, though execution risk exists during the transition.
- Outsourced partners: vendors and contract workers can expect renegotiation or reductions.
What affected employees should do now
- Check official communications from HR and your manager for next steps and severance details.
- Ask about outplacement support (resume help, job counseling) and whether the company offers extended healthcare, COBRA assistance, or phased transitions.
- Document your work (accomplishments, repos, access) and secure personal copies of non-sensitive materials.
- File for unemployment as soon as possible where eligible and update LinkedIn and your network.
- Use company resources (employee assistance programs, career centers) and local talent services.
What managers and the company should prioritize
- Clear, compassionate communications and FAQs for affected employees.
- Fast, transparent explanation of severance, benefits continuation, and outplacement services.
- Careful workload redistribution and project continuity plans to avoid customer impact.
- A public-facing message to reassure customers and investors about service continuity and long-term strategy.
Market and strategic context (what this implies)
- Verizon is attempting aggressive cost reduction while refocusing on product and service quality (e.g., 5G, fixed wireless, enterprise services).
- Cutting outsourced labor and internal layers can reduce costs but carries execution risk: lost institutional knowledge, lowered morale, and short-term productivity dips.
- Investors may welcome lower operating expenses; customers and regulators will watch for service degradation.
data breaches
Cloudflare Outage Disrupts Global Internet — Company Restores Services After Major Traffic Spike

November 18, 2025 — MAG212NEWS
A significant outage at Cloudflare, one of the world’s leading internet infrastructure providers, caused widespread disruptions across major websites and online services on Tuesday. The incident, which began mid-morning GMT, temporarily affected access to platforms including ChatGPT, X (formerly Twitter), and numerous business, government, and educational services that rely on Cloudflare’s network.
According to Cloudflare, the outage was triggered by a sudden spike in “unusual traffic” flowing into one of its core services. The surge caused internal components to return 500-series error messages, leaving users unable to access services across regions in Europe, the Middle East, Asia, and North America.
Impact Across the Web
Because Cloudflare provides DNS, CDN, DDoS mitigation, and security services for millions of domains — powering an estimated 20% of global web traffic — the outage had swift and wide-reaching effects.
Users reported:
- Website loading failures
- “Internal Server Error” and “Bad Gateway” messages
- Slowdowns on major social platforms
- Inaccessibility of online tools, APIs, and third-party authentication services
The outage also briefly disrupted Cloudflare’s own customer-support portal, highlighting the interconnected nature of the company’s service ecosystem.
Cloudflare’s Response and Restoration
Cloudflare responded within minutes, publishing updates on its official status page and confirming that engineering teams were investigating the anomaly.
The company took the following steps to restore operations:
1. Rapid Detection and Acknowledgement
Cloudflare engineers identified elevated error rates tied to an internal service degradation. Public communications were issued to confirm the outage and reassure customers.
2. Isolating the Affected Systems
To contain the disruption, Cloudflare temporarily disabled or modified specific services in impacted regions. Notably, the company deactivated its WARP secure-connection service for users in London to stabilize network behavior while the fix was deployed.
3. Implementing Targeted Fixes
Technical teams rolled out configuration changes to Cloudflare Access and WARP, which successfully reduced error rates and restored normal traffic flow. Services were gradually re-enabled once systems were verified stable.
4. Ongoing Root-Cause Investigation
While the unusual-traffic spike remains the confirmed trigger, Cloudflare stated that a full internal analysis is underway to determine the exact source and prevent a recurrence.
By early afternoon UTC, Cloudflare confirmed that systems had returned to pre-incident performance levels, and affected services worldwide began functioning normally.
Why This Matters
Tuesday’s outage underscores a critical truth about modern internet architecture: a handful of infrastructure companies underpin a massive portion of global online activity. When one of them experiences instability — even briefly — the ripple effects are immediate and worldwide.
For businesses, schools, governments, and content creators, the incident is a reminder of the importance of:
- Redundant DNS/CDN providers
- Disaster-recovery and failover plans
- Clear communication protocols during service outages
- Vendor-dependency risk assessments
Cloudflare emphasized that no evidence currently points to a cyberattack, though the nature of the traffic spike remains under investigation.
Looking Ahead
As Cloudflare completes its post-incident review, the company is expected to provide a detailed breakdown of the technical root cause and outline steps to harden its infrastructure. Given Cloudflare’s central role in global internet stability, analysts say the findings will be watched closely by governments, cybersecurity professionals, and enterprise clients.
For now, services are restored — but the outage serves as a powerful reminder of how interconnected and vulnerable the global web can be.







