

November 25, 2025 – In a move to enhance transparency and curb the spread of bots and foreign influence on its platform, X (formerly Twitter) has...


Verizon announced a sweeping workforce reduction that will affect “more than” 13,000 employees — roughly 13% of its global headcount — in what CEO Dan Schulman...


November 18, 2025 — MAG212NEWS A significant outage at Cloudflare, one of the world’s leading internet infrastructure providers, caused widespread disruptions across major websites and online...
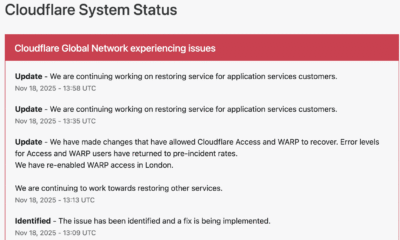

SAN FRANCISCO, CA — A widespread disruption across major internet services, including AI platform ChatGPT and social media giant X (formerly Twitter), has drawn critical attention...
Rabat — October 2025Inside Morocco’s Parliament, tension and reflection filled the air just hours after His Majesty King Mohammed VI delivered his opening-session speech. What was...


Wiz Research finds an exposed ClickHouse database with 1M+ log lines, including chat histories and secrets—spotlighting human error, weak access controls, and the need for DLP....


Tata Motors’ luxury brand shuts global IT systems amid suspected ransomware attack; no customer data reported compromised. Jaguar Land Rover has shut down production and retail...
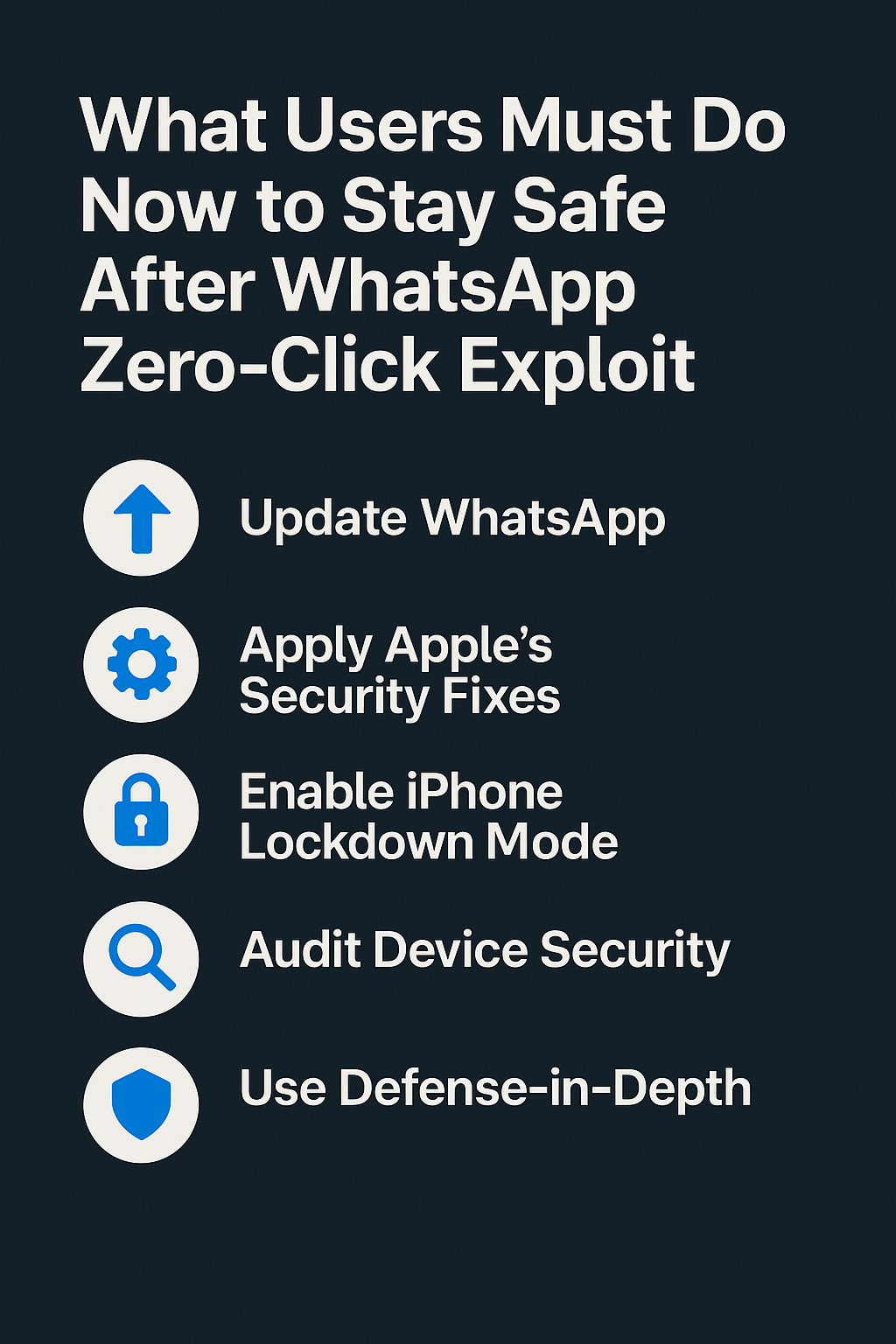

Update Immediately to Block CVE-2025-55177 WhatsApp has released patched versions for iOS and macOS (2.25.21.73 and later for iOS, 2.25.21.78 for Mac). Users should update immediately...


Meta fixes actively exploited flaw chained with recent Apple bug; high-risk users urged to update immediately Meta has shipped an emergency WhatsApp update to fix CVE-2025-55177,...
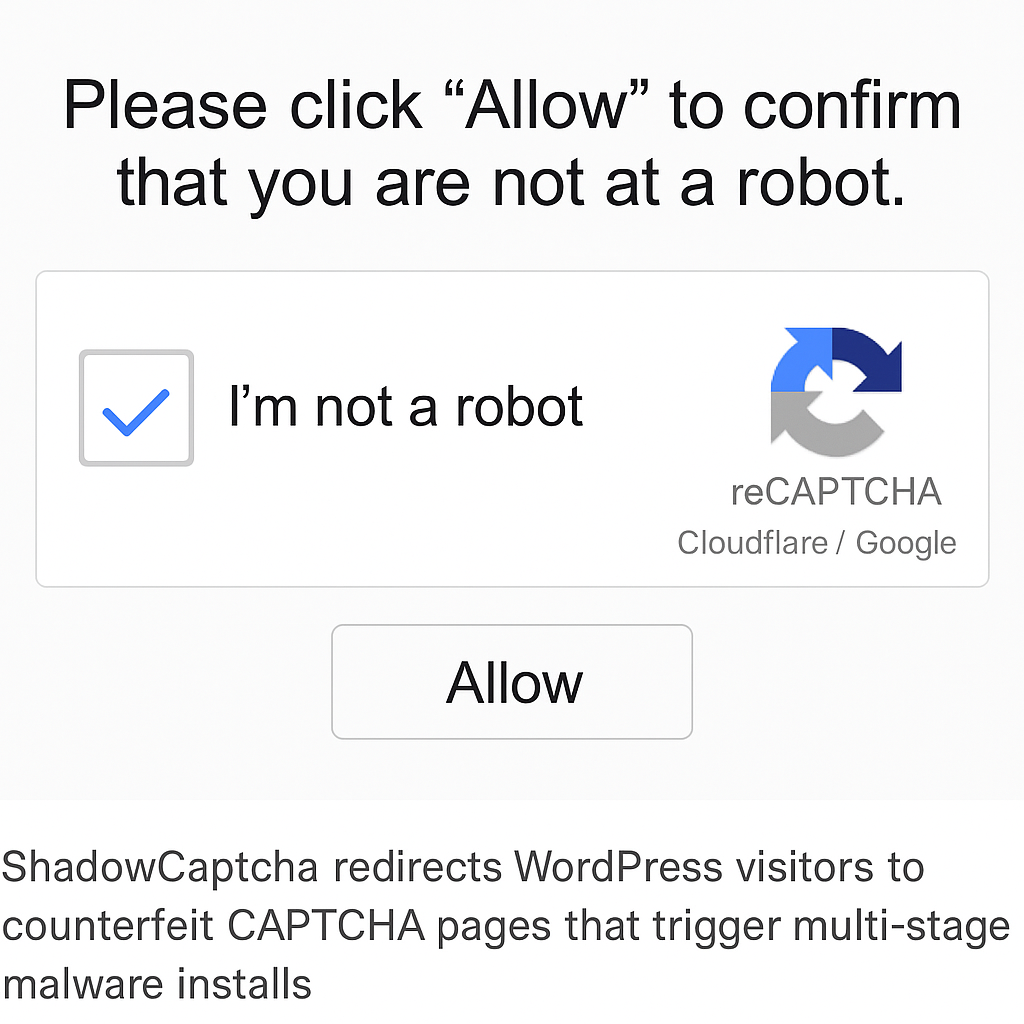

Over 100 hacked WordPress sites redirect visitors to fake Cloudflare/Google CAPTCHA pages using “ClickFix” to execute Lumma, Rhadamanthys, Epsilon Red, and XMRig payloads, researchers say. A...