

Governor’s Technology Office says no evidence of PII exposure as FBI joins probe; DMV, agency websites and phone lines saw disruptions while emergency 911 remained available....
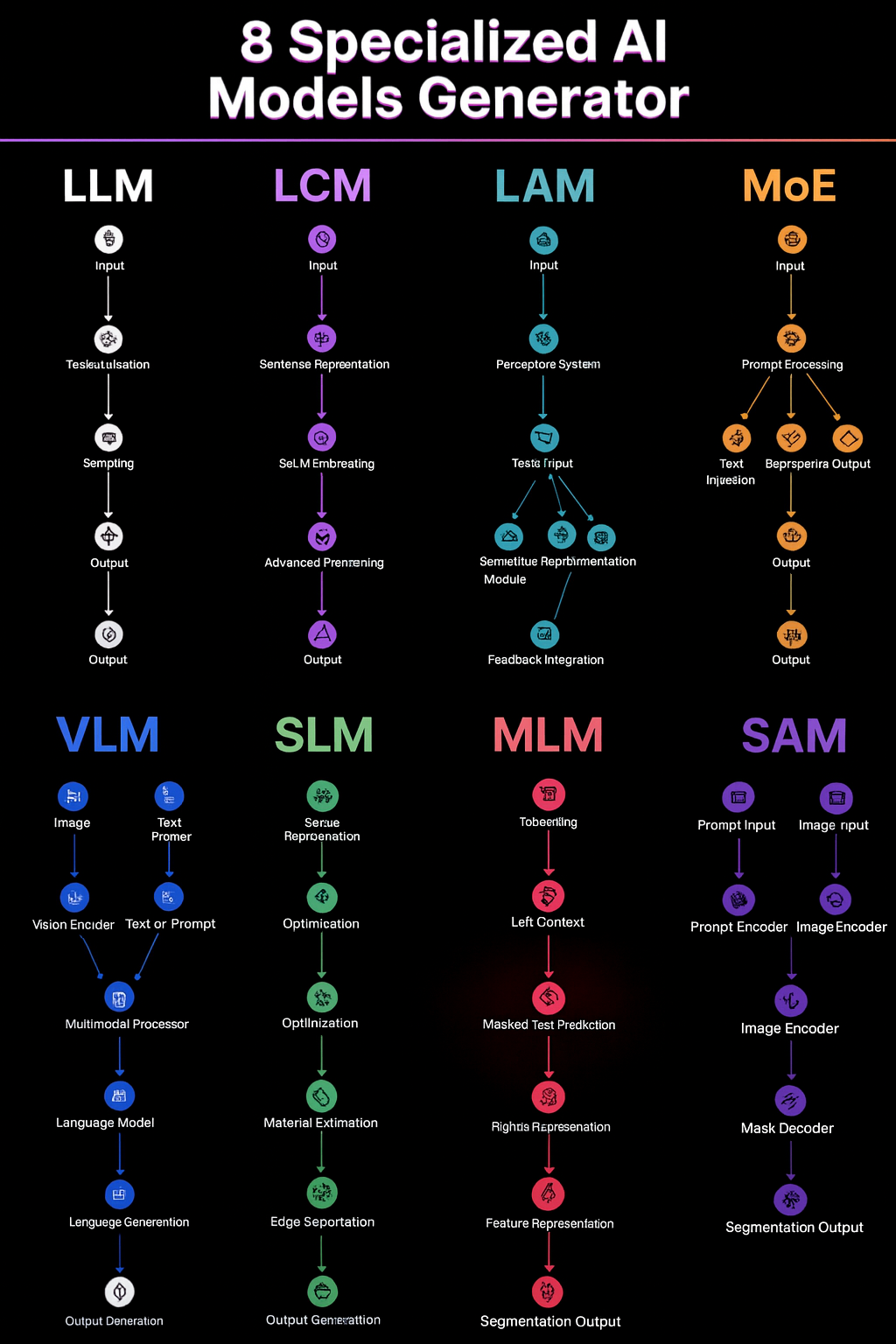

AI isn’t “one giant model for everything” anymore. The fastest progress is coming from specialized models—each excellent at a narrow slice of the problem—and smart integration...
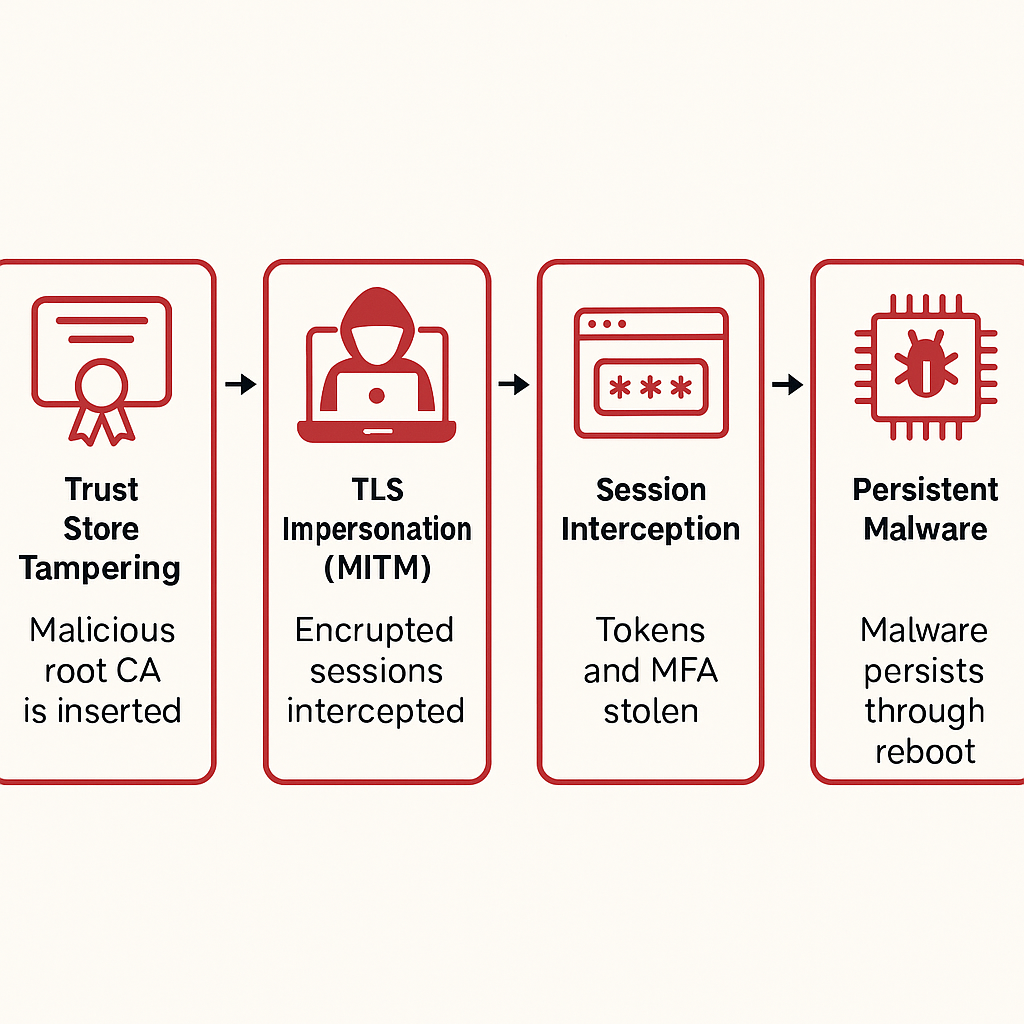

Secret Blizzard’s embassy campaign shows why device trust beats TLS trust alone—and how to harden firmware, keys, and boot chains A new expert analysis warns that...
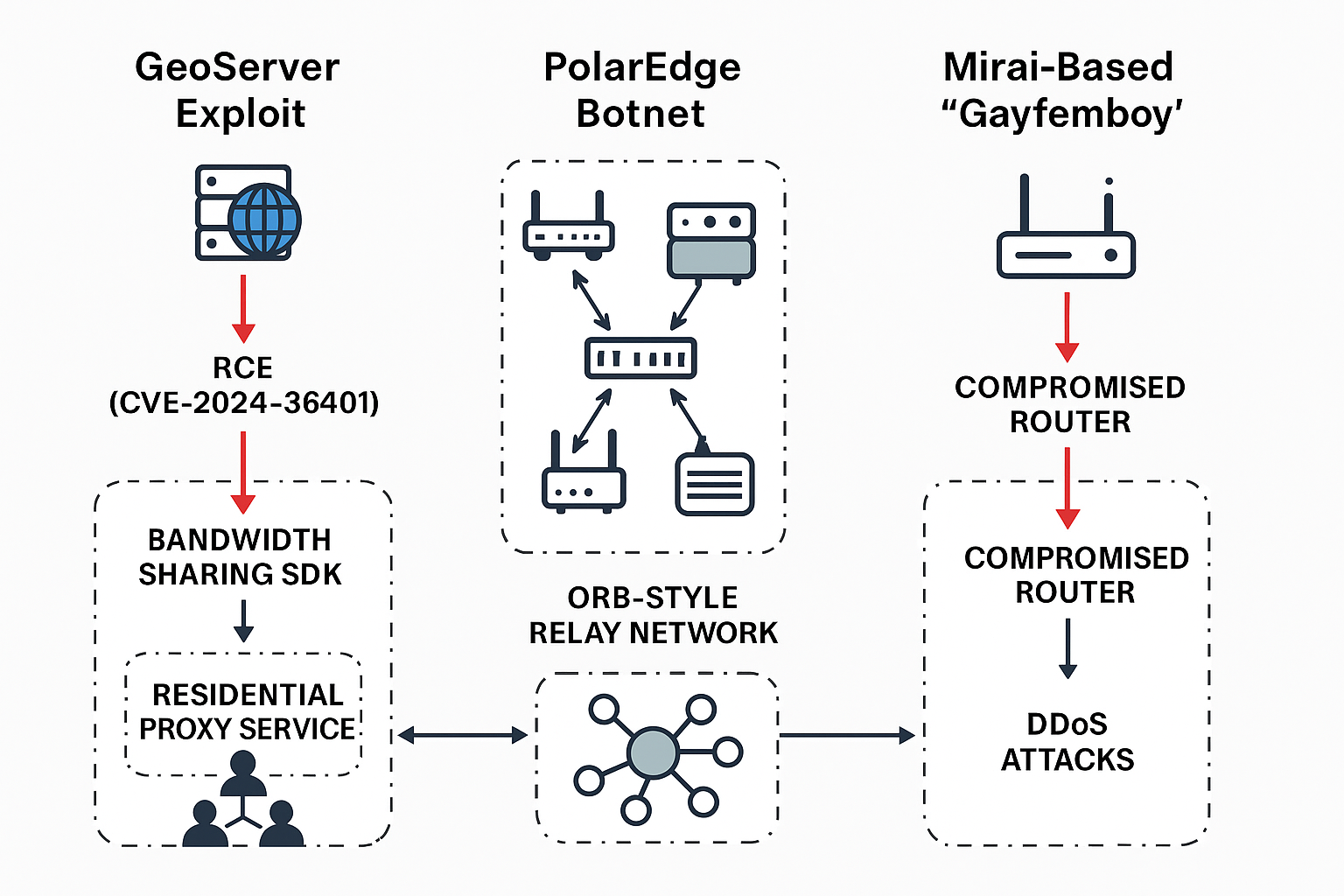

ORB-style relay networks, SDK-based bandwidth theft, and Mirai spin-offs fuel a new wave of silent monetization and stealthy ops Excerpt (40–60 words)Attackers are chaining a critical...


AI, data, cybersecurity and project management lead the list as employers prioritize job-ready skills. Here are high-quality Coursera courses you can audit for free—plus how to...


Two-day February intrusion leaked financial and medical details; group begins notifications and offers credit monitoring as regulators are alerted. The Business Council of New York State...


Contact data for ~280k email accounts and 1.7k modem passwords accessed; breach isolated to iiNet order system, company says Australia’s TPG Telecom disclosed unauthorized access to...


From permits to youth benefits, the kingdom consolidates e-government portals for residents and the diaspora. RABAT, Morocco — Morocco’s government is expanding a network of official...


Experts urge MAC randomization and power tuning as homeowners seek to curb street-level network tracking. Security specialists warn that home Wi-Fi networks are quietly cataloged by...
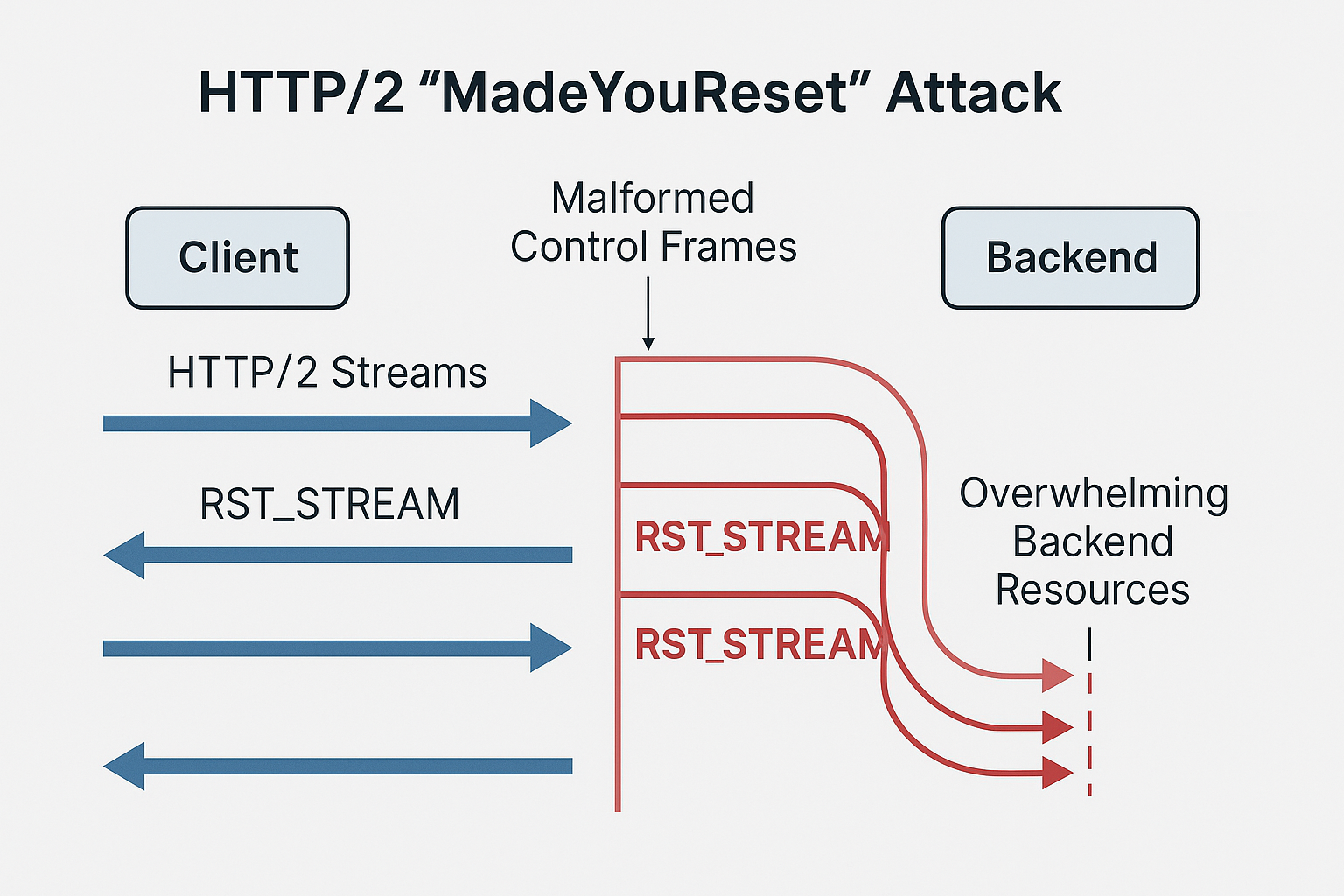

New CVE-2025-8671 technique bypasses Rapid Reset defenses; patches rolling out for Tomcat, Netty, F5 as vendors coordinate with CERT/CC. A newly disclosed HTTP/2 vulnerability dubbed “MadeYouReset”...