business
Crypto Milestone: Bitcoin Hits $94K, ETFs Surge in Volume

- Market Trends:
- Bitcoin (BTC): Bitcoin has been trading near all-time highs, with reports suggesting it briefly surpassed $94,000. This surge is attributed to several factors including optimistic market sentiment post the U.S. elections, institutional adoption, and expectations of further regulatory clarity under a potentially crypto-friendly administration.
- New Developments and Products:
- BlackRock’s Bitcoin ETF Options: BlackRock launched options for its iShares Bitcoin Trust ETF (IBIT), which saw an unprecedented trading volume of $1.9B on its first day. This indicates strong institutional interest in crypto derivatives.
- Memecoins and DeFi: There’s significant activity in the memecoin sector, with Solana-based tokens like BONK regaining dominance, showcasing the volatile yet lucrative nature of memecoins. Raydium, a decentralized exchange on Solana, has flipped Tether in 24-hour fees generated, highlighting the growth in DeFi activities on alternative blockchains.
- Regulatory News:
- South Korea’s Tax Proposals: South Korea’s Democratic Party is pushing for a 20% crypto tax in 2025 but with an increased taxable gains threshold from $1,800 to $36,000. This move could significantly impact crypto holders in Korea.
- Technological Advancements:
- Ethereum: There’s noted growth in Ethereum’s DeFi sector, with DApp volumes gaining 38% in a month, which might signal an upcoming price movement for ETH.
- Market Sentiment:
- The crypto market is experiencing a mix of retail and institutional interest, with rotations happening fast among various assets. Despite Bitcoin’s highs, some altcoins and memecoins are experiencing volatility, suggesting a complex market dynamic where different segments behave independently.
- Noteworthy Mentions:
- The launch of “first major DeFi-native stablecoin” $USDS on Solana by Sky (formerly Maker) marks another step in the evolution of decentralized finance on alternative blockchains.
These activities underline a vibrant, evolving landscape in the cryptocurrency sector, with significant moves towards mainstream adoption, regulatory adjustments, and technological innovation.
business
🇲🇦 King Mohammed VI’s Speech Sparks Heated Debate in Parliament — “جيل زد يُجيب”
Rabat — October 2025
Inside Morocco’s Parliament, tension and reflection filled the air just hours after His Majesty King Mohammed VI delivered his opening-session speech. What was meant as a national roadmap quickly turned into a day of open confrontation, emotional testimonies, and unexpected admissions from members of both majority and opposition blocs.
🏛️ A Speech That Touched Nerves
The King’s address, described by analysts as “direct and reform-oriented,” called for greater social justice, job creation, and balanced development across Morocco’s regions.
“No village left forgotten, no coast without a hand,” the King declared — a message that resonated deeply with citizens and lawmakers alike.
Within hours, parliamentary corridors buzzed with interviews, arguments, and introspection. Some MPs hailed the speech as “a moral reset,” while others questioned whether the government was capable of turning royal vision into tangible results.
🧠 From Rabat to the Sahara — Gen Z Responds
Younger members of Parliament — labeled as جيل زد (Gen Z) — became the focus of cameras and public curiosity. Many expressed frustration at what they see as a widening gap between political promises and everyday realities faced by Moroccan youth.
“The King spoke about unity and work. We agree — but the youth need a chance to prove themselves,” said one 28-year-old deputy.
“We have the energy; the system just needs to open its doors.”
Another young MP caused a social-media storm after saying that “in some ways, Moroccan social values are stronger than Germany’s.”
Critics accused him of downplaying Europe’s economic strength, while others applauded his pride in Moroccan family cohesion.
He later clarified his words, emphasizing that every nation faces challenges — and that Morocco’s real wealth lies in its people.
💬 Resignation, Reflection, and Responsibility
Just a week earlier, one deputy had submitted his resignation in protest over what he called “a lack of listening to the new generation.”
After the King’s address, he withdrew it.
“The royal speech gave me renewed hope. This is not the time to quit — it’s time to work,” he told reporters.
Across party lines, both RNI and PAM youth wings echoed similar messages: commitment to reform, but also impatience with bureaucracy.
Several MPs criticized ministers who, they said, “do not answer calls, do not reply to written questions, and have lost touch with citizens.”
⚖️ Opposition Voices: ‘A Government in Denial’
Members of the opposition used the session to accuse the cabinet of denial and poor communication, arguing that ministers are “living in a different reality” from citizens struggling with prices and unemployment.
“The royal messages were clear,” said one opposition leader. “The problem is not the King’s vision — it’s implementation.”
🌍 Morocco’s Path Forward
Analysts note that the King’s address aligned with long-standing themes: national cohesion, balanced territorial development, and respect for dignity in public service.
But the 2025 context — economic pressure, youth disillusionment, and the digital activism of Gen Z — gives these calls new urgency.
“This generation communicates differently,” said a policy researcher. “If institutions don’t adapt, they’ll lose credibility.”
🕊️ A Message Beyond Politics
As the parliamentary session ended, one young MP summed up the mood:
“الملك تكلّم… ونحن سنُجيب بالعمل — The King spoke, and we will answer through action.”
For now, the chamber that often echoes with partisan debates found itself united — briefly — under a single message:
Morocco’s future belongs to its youth, but responsibility belongs to everyone.
business
Luxury Carmaker Jaguar Land Rover Shuts IT Systems After Cyberattack

Tata Motors’ luxury brand shuts global IT systems amid suspected ransomware attack; no customer data reported compromised.
Jaguar Land Rover has shut down production and retail systems worldwide after a cyberattack “severely disrupted” operations. A hacking group linked to previous attacks on UK retailers has claimed responsibility. While no customer data appears compromised, the incident halted vehicle registrations and manufacturing, raising fresh alarms about the auto industry’s vulnerability to cyber threats
Jaguar Land Rover Hit by Major Cyberattack
Jaguar Land Rover’s global production and retail operations were brought to a standstill this week after a cyberattack “severely disrupted” its IT systems. The company shut down core applications and suspended manufacturing across key UK plants, including Halewood and Solihull, during one of the busiest sales periods of the year.
The UK’s National Crime Agency has opened an investigation, while the company races to restore operations. JLR confirmed that, as of now, there is no evidence that customer data has been compromise
Immediate Disruption to Plants and Dealers
The September 2 cyber incident forced JLR, owned by India’s Tata Motors, to halt assembly lines, send staff home, and suspend dealer systems used to register new vehicles. Dealers reported they could sell in-stock cars but could not process new registrations, delaying deliveries and revenue flows.
A company spokesperson said:
“We took immediate action to mitigate its impact by proactively shutting down our systems. We are now working at pace to restart our global applications in a controlled manner.”
Expert Reactions
Cybersecurity specialists warn the incident highlights the fragility of digitally integrated manufacturing.
Dray Agha, Senior Manager at Huntress, said:
“This incident highlights the critical vulnerability of modern manufacturing, where a single IT system attack can halt a multi-billion-pound physical production line.”
Aiden Sinnott, a researcher at Sophos, compared the attackers’ tactics to those of notorious cyber gangs:
“They speak English and they are keen on using social media channels. Lapsus$ shared similar tactics and demographics as the Scattered Spider collective.”
Technical Analysis
While JLR has not disclosed the specific intrusion method, several indicators suggest ransomware-style tactics:
- Proactive Shutdowns: JLR’s decision to disable IT and OT (operational technology) systems aligns with standard ransomware containment measures.
- Interconnected Impact: The attack disrupted not just IT but entire supply chains, underscoring the risks of tightly linked digital production networks.
- Extortion Motive Likely: Although no ransom demand has been confirmed, past incidents involving JLR and similar industries suggest data exfiltration and extortion are possible.
The incident underscores the importance of segmentation, real-time monitoring, and robust incident response across manufacturing IT and OT systems.
Impact and Response
- Employees: Factory staff in the UK were sent home as assembly lines stopped.
- Dealers & Customers: Dealers could not register new vehicles, delaying customer deliveries.
- Suppliers: Supply chains faced ripple effects, with halted orders and logistics disruptions.
JLR has engaged external cybersecurity teams and is working with government agencies to restore operations in stages. The company must also prepare for regulatory inquiries and possible long-term trust issues with suppliers and consumers.
Broader Context
The cyberattack comes amid a surge in UK corporate cyber incidents. Retailers including Marks & Spencer, Co-op, and Harrods have all suffered breaches in recent months.
For JLR, this is the second major attack in 2025, following a March breach where a ransomware group claimed to have stolen internal data. The company had invested heavily in cybersecurity modernization, including a contract with Tata Consultancy Services—but repeated incidents suggest lingering vulnerabilities.
Conclusion
Jaguar Land Rover’s shutdown highlights the growing risks of interconnected, digital-first manufacturing. In today’s auto industry, downtime no longer means a local setback—it translates directly into lost global revenue and potential long-term reputational harm.
As JLR works to restore its systems, the incident serves as a stark reminder: in modern manufacturing, operational resilience depends as much on cybersecurity as on engineering.
Sources:
Reuters, Britain’s JLR hit by cyber incident that disrupts production, sales;
The Guardian, Hackers linked to M&S breach claim responsibility for Jaguar Land Rover cyber-attack;
Financial Times, Jaguar Land Rover says production ‘severely’ disrupted by cyber incident;
SecurityWeek, Jaguar Land Rover Operations Severely Disrupted by Cyberattack.
business
Windows 10 Deadline Looms: How to Stay Protected Beyond 2025
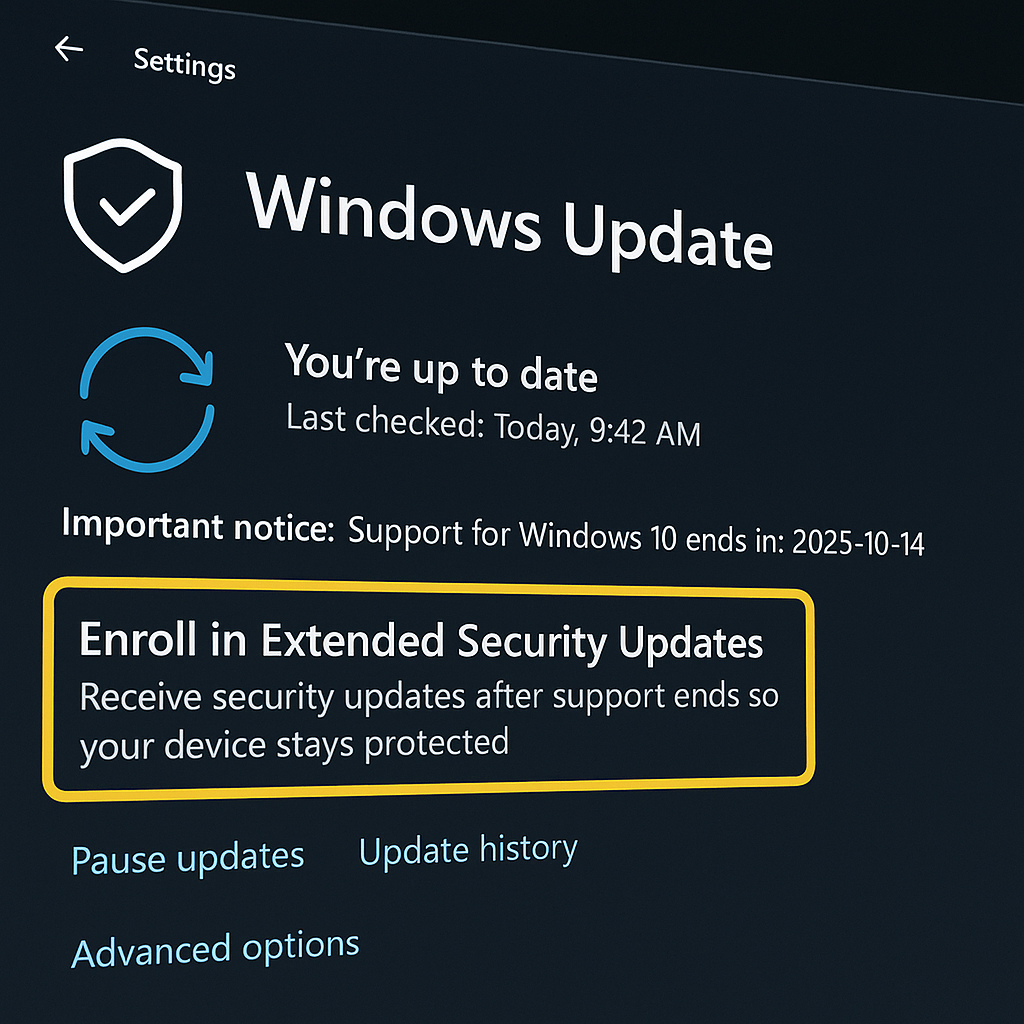
Free support ends October 14, 2025; new KB5063709 unlocks Extended Security Updates enrollment to keep critical patches flowing through October 2026.
Microsoft is warning Windows 10 users that free security updates end on October 14, 2025. A new cumulative update, KB5063709, enables a built-in enrollment flow for the Extended Security Updates (ESU) program, offering another year of fixes to October 13, 2026. Edge and WebView2 will still receive updates on Windows 10 until 2028.
With less than two months before Windows 10 reaches end of support, Microsoft has issued a final security warning: after October 14, 2025, no more free fixes. A fresh update, KB5063709, now exposes an “Enroll in Extended Security Updates” option inside Windows Update to help users secure one more year of patches.
- End of free support: Windows 10 (22H2) stops receiving free security updates on Oct. 14, 2025.
- Bridge program: Microsoft’s Consumer ESU extends security fixes to Oct. 13, 2026; enrollment is now available from Settings after installing KB5063709.
- Browser exception: Microsoft Edge and WebView2 Runtime will keep updating on Windows 10 through at least Oct. 2028—even if you don’t buy ESU.
- Scale: Windows 10 still represents roughly 43% of active Windows desktops worldwide (Statcounter, July 2025).
“After October 14, 2025… Microsoft will no longer provide security updates or fixes.” — Microsoft support page. Microsoft Support
“KB5063709… includes a fix for a bug that prevented enrollment in extended security updates.” — BleepingComputer (Aug. 12, 2025). BleepingComputer
“Edge and the WebView2 Runtime will continue to receive updates on Windows 10… until at least October 2028.” — Microsoft Edge lifecycle. Microsoft Learn
A separate storyline continues to roil the transition: a California lawsuit alleges Microsoft set the 2025 cutoff to push AI-ready PCs; Microsoft points to ESU as a safety net, but litigation underscores user anxiety about older, ineligible hardware.
What’s changing on Patch Tuesday:
- KB5063709 (Aug. 2025): Required to expose the ESU enrollment UI under Settings → Update & Security → Windows Update. It also resolves the enrollment-wizard crash and rolls in July’s security fixes (including one zero-day).
Enrollment mechanics (consumer ESU):
- Prereqs: Windows 10 22H2, admin rights, and Microsoft account sign-in (local accounts are not supported for ESU).
- Cost options: $30 one-year ESU, 1,000 Microsoft Rewards points, or free if you enable OneDrive settings sync—all visible in the built-in wizard after KB5063709.
Risk surface if you skip ESU:
- Unpatched remote code execution and privilege-escalation flaws accrue monthly across the kernel, Win32k, networking stack, printing, and driver ecosystems. Even with a supported browser, OS-level exposures (SMB, RPC, LSA, Credential Guard bypasses) remain unmitigated. (Derived from Microsoft monthly CVE cadence; see KB5063709 advisory context.)
Mitigations checklist (if you must remain on Windows 10):
- Enroll in ESU and keep Windows Defender/EDR signatures current.
- Harden attack surface: disable legacy protocols (SMBv1), restrict RDP, enforce LSA protection, and require smartcard/Windows Hello where possible. (General guidance aligned with Microsoft security baselines.)
- Application control: enable ASR rules and Smart App Control-equivalents; prefer standard user rights.
- Network containment: segment legacy Windows 10 devices; use firewall allow-lists and zero-trust access.
- Browser updates: keep Edge/WebView2 current; isolate risky web apps in Application Guard where available.
Impact & Response
Who’s affected: Home users, SMBs, schools, and agencies still running Windows 10—hundreds of millions of devices globally. Statcounter shows Windows 10 usage near 43% in July 2025, meaning a large residual population will face patch gaps without ESU.
Actions to take now:
- Install KB5063709, then open Windows Update → Enroll in Extended Security Updates and choose a plan.
- Plan upgrades to Windows 11 24H2+ or supported alternatives; Microsoft reiterates Oct. 2025 as the firm cutoff for free updates.
Long-term implications: Expect shrinking driver/app support and rising exploit availability on unpatched systems, even as browsers continue to update through 2028.
Background
Microsoft set Windows 10 22H2 as the final feature version and has repeated the Oct. 14, 2025 deadline since 2023–24 guidance. ESU is designed as a temporary bridge, not a multi-year extension. Browser support to 2028 offers partial protection, but it does not replace OS security hardening.
- “ESU buys time—but not immunity. Treat it like a controlled exit ramp: enroll now, apply strict hardening (kill SMBv1, lock down RDP, enforce LSA protection), and move critical workloads to supported platforms within 12 months. The cost of delaying migration will be paid in incident response.” — El Mostafa Ouchen, cybersecurity author & practitioner.
- Microsoft (support notice):
“After October 14, 2025… we will no longer provide security updates or fixes.” - BleepingComputer (on KB5063709):
“The update… fixes a bug that prevented enrollment in extended security updates.” - Microsoft Edge team (lifecycle policy):
“Edge and WebView2 will continue to receive updates on Windows 10 until at least October 2028.”
Conclusion
Microsoft’s warning is unambiguous: Windows 10’s free patch era ends on October 14, 2025. The KB5063709 + ESU path is a short-term safety measure to October 2026, not a strategy. Organizations and households should enroll if needed—but prioritize upgrading or retiring Windows 10 endpoints to reduce exposure as exploit pressure rises.