


Incident forces suspension of 80 UK funds as forensic investigation and system restoration efforts intensify. France-based FinTech firm Linedata has suffered a cyberattack that encrypted data...

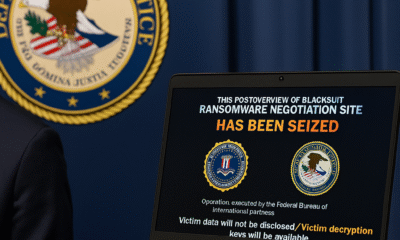

Law enforcement seized four servers, nine domains, and about $1.09M in crypto linked to the Royal/BlackSuit operation, following a July 24 takedown coordinated with eight countries....
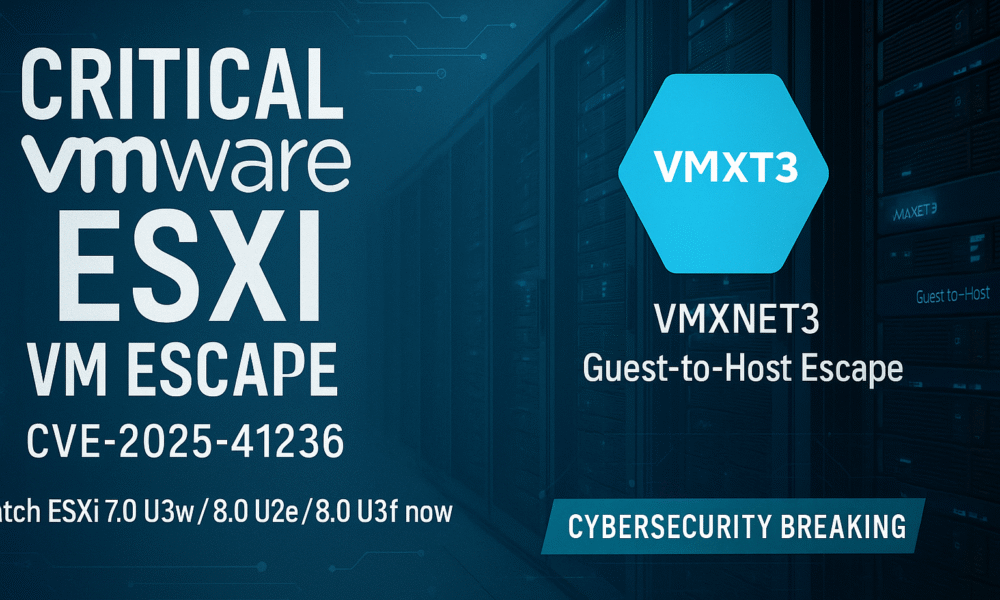
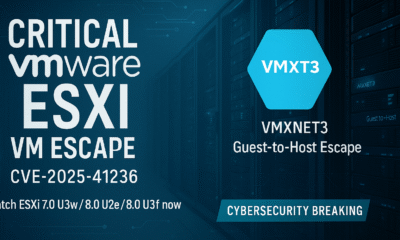

Broadcom/VMware patches CVE-2025-41236 in ESXi 7.x/8.x, but Shadowserver counts show slow remediation as thousands of internet-reachable hosts remain on vulnerable builds. A critical integer-overflow flaw (CVE-2025-41236)...



Phone, email, and website went dark as investigators probe links to widely exploited Citrix NetScaler flaws. The Pennsylvania Attorney General’s Office says a cyberattack disabled its...
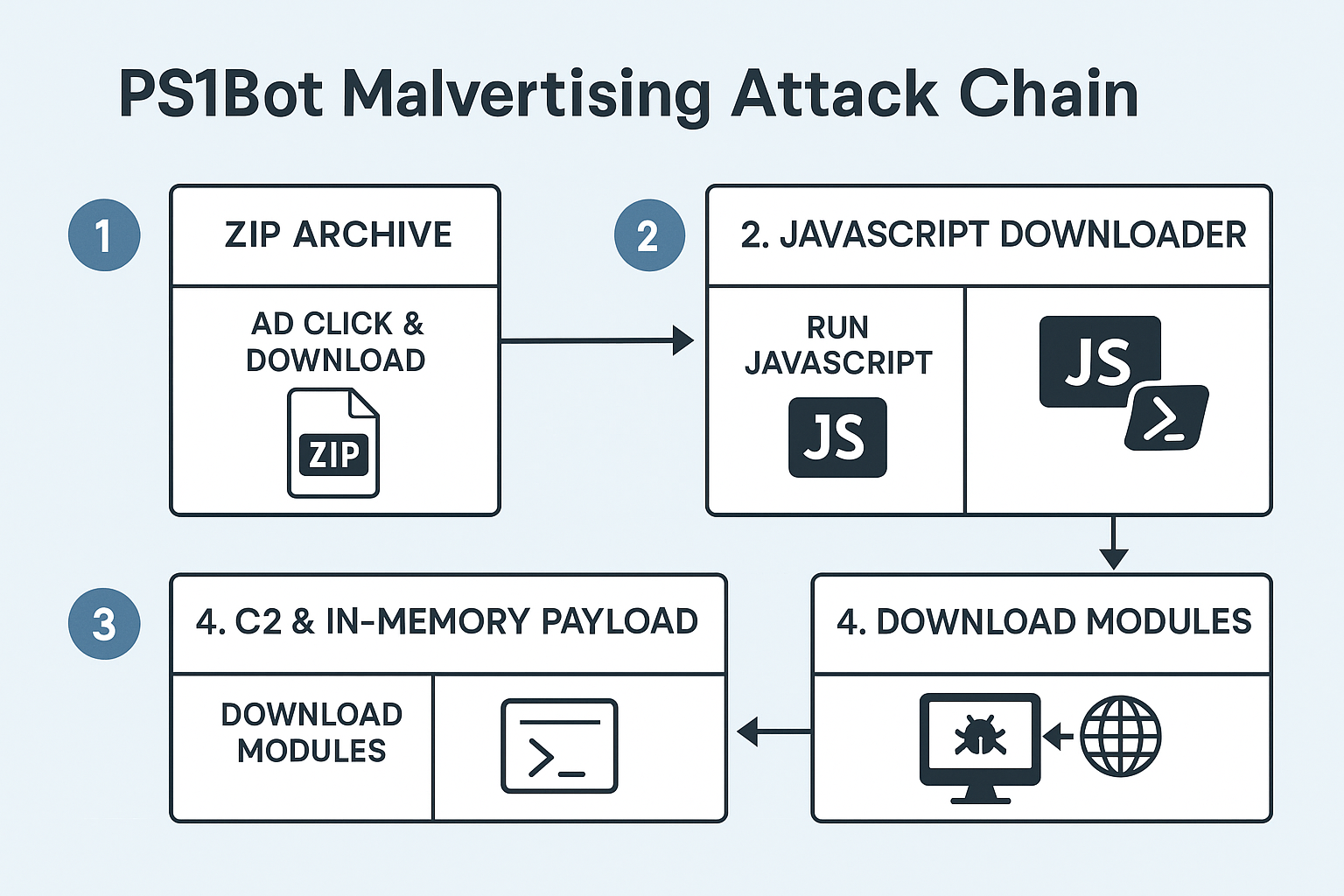


Cisco Talos warns of a modular PowerShell/C# threat stealing wallets, logging keystrokes, and persisting without writing payloads to disk. A new malvertising campaign is delivering PS1Bot,...

Hackers claim “full system compromise,” say all servers were encrypted and backups wiped; company has not confirmed the incident as investigators assess potential operational impact Royal...

Cyber threat actors orchestrated a massive, two-wave brute-force assault on Fortinet SSL VPNs, shifting mid-campaign to FortiManager—raising alarm as such patterns often precede critical CVE disclosures....



Morocco’s Directorate General of Information Systems Security (DGSSI) issues a dire warning: a zero-day vulnerability in WinRAR is being actively exploited, putting countless users at risk...



In a precision cyber strike, Kyiv’s defense intelligence infiltrated a top-tier private ISP serving Russian security agencies—raising stakes far beyond the digital realm. When the hum...



Fresh vulnerabilities in the TETRA standard allow attackers to replay calls, brute-force encryption, and inject fake voice/data—even on “secure” networks. No universal fixes exist, leaving critical...