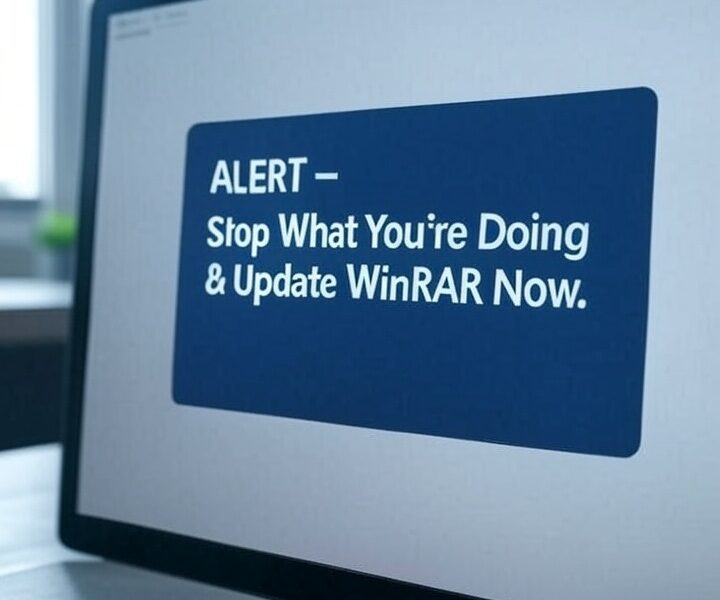


A zero-day flaw (CVE-2025-8088) is under active attack by Russian-linked groups Paper Werewolf and RomCom. Booby-trapped archives can plant malware in Windows startup folders—silently hijacking your...



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...



From cryptographic signing to hardened base images, a new security webinar unpacks the real-world tactics to stop supply-chain breaches targeting Python’s vast open-source ecosystem. The command...


A coordinated supply‑chain campaign dating from March 2023 has unleashed 60 rogue Ruby gems—and unknown Python packages—disguised as benign tools, siphoning credentials and crypto data, triggering...



France’s third-largest mobile operator confirms unauthorized access to sensitive data, including IBANs, as authorities probe breach amid rising telecom sector cyber threats. A wave of anxiety...



From speculative chip flaws to zero-day exploits, Apple rushes to patch a series of high-risk vulnerabilities targeting billions of users worldwide. A Perfect Storm: Apple Grapples...



Medical data at risk as ransomware attack compromises DaVita’s third-party billing provider; experts warn of growing cyber threats targeting healthcare infrastructure. By El Mostafa Ouchen |...



New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...


Malicious apps disguised as utility tools rake in hidden subscription fees, spam users relentlessly, and harvest personal data—millions of installs and growing exposes a broader mobile...



Cybercrime syndicate UNC6040 used spoofed IT helpdesk calls and legitimate remote access tools to infiltrate corporate environments—Google TAG reveals ongoing threat to global organizations. SEO-Optimized Excerpt:Google’s...