


Security experts urge a shift from once-a-year audits to continuous 24/7 defense. Organizations are being pushed to build “Offensive SOC” teams that hunt threats proactively, aligning...



CISA and FBI raise red flags about a new ransomware strain crippling essential services while urging critical sectors to adopt robust defense strategies. Washington D.C. |...


Chinese-state hackers allegedly exploited a SharePoint zero-day to breach the U.S. National Nuclear Security Administration (NNSA), prompting urgent calls for patching, segmentation, and zero-trust enforcement. 🔍...



Dissecting the internals of modern credential theft campaigns with command-line insights, evasion techniques, and real-world behavior. 🧬 Introduction In 2025, cybercriminals are no longer relying on...



As Morocco’s citizens turn to cyber offices to access essential public services, sensitive personal data may be at risk—raising urgent questions about digital security, regulatory gaps,...



As cyberattacks grow in scale and complexity, leading cybersecurity firms are turning to cutting-edge attack simulation tools like SafeBreach, XM Cyber, and CALDERA to preempt threats,...
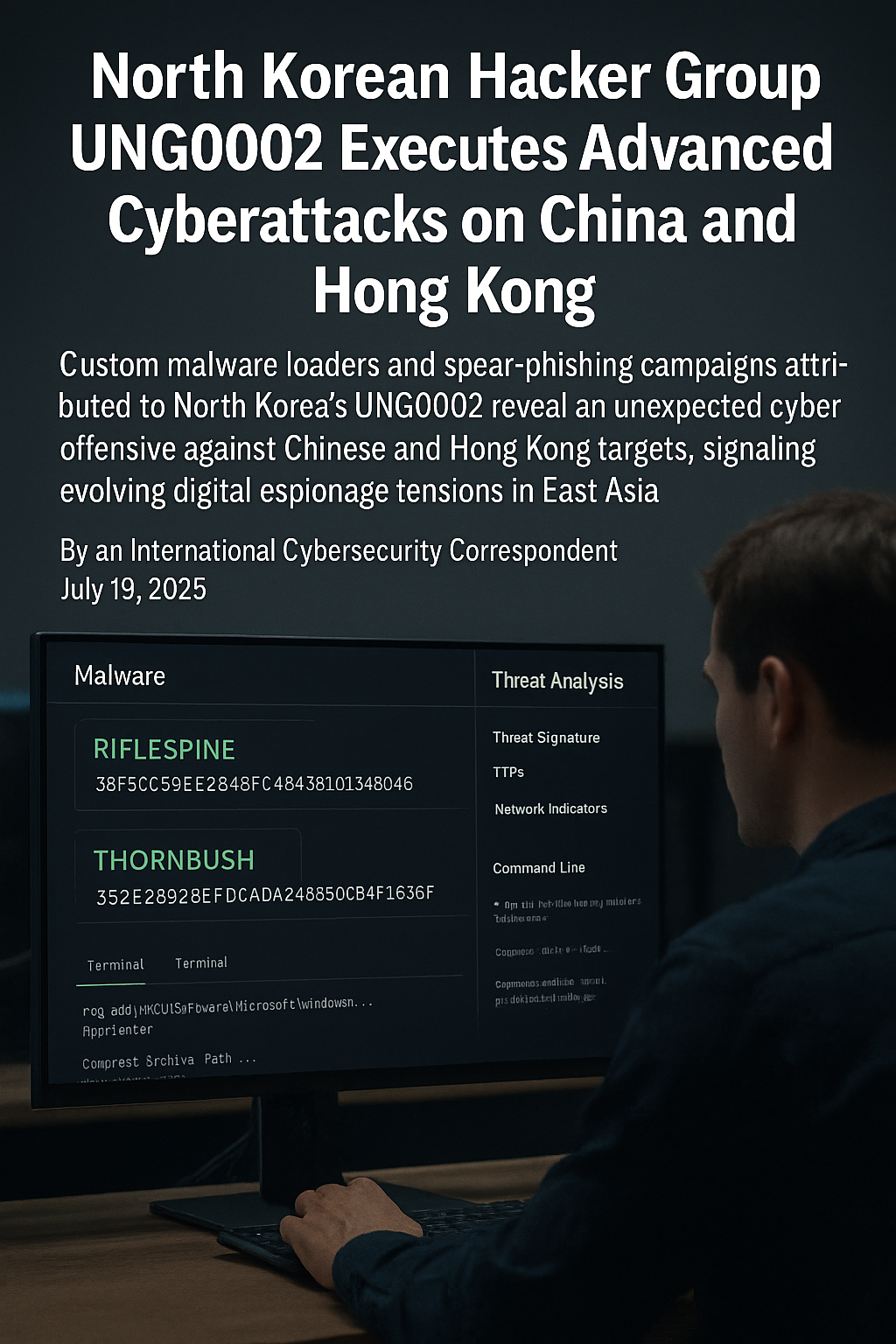


Custom malware loaders and spear-phishing campaigns attributed to North Korea’s UNG0002 reveal an unexpected cyber offensive against Chinese and Hong Kong targets, signaling evolving digital espionage...



State-backed threat actors exploit two Ivanti Connect Secure vulnerabilities to breach high-value networks, steal credentials, and drop sophisticated malware—raising alarms over critical infrastructure defense worldwide. Global...
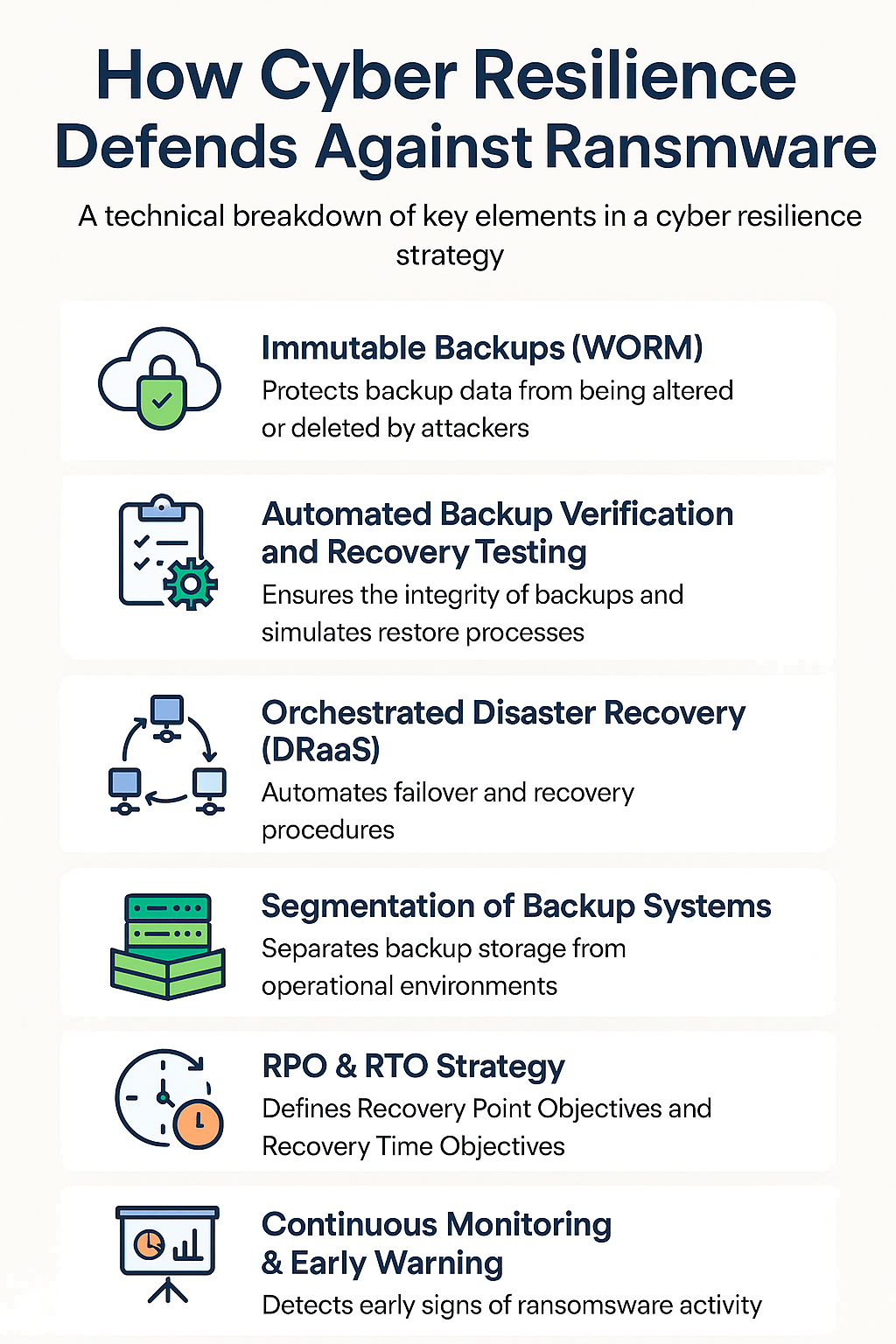


As ransomware actors escalate attacks on backups and recovery systems, IT leaders worldwide are pivoting from traditional backup strategies to holistic cyber resilience frameworks to safeguard...



Novabev Group, one of Russia’s largest alcohol producers, confirms cyberattack crippled point-of-sale systems and online services; no group has claimed responsibility. Vodka on Hold: Ransomware Attack...