


State‑linked cyber actors leverage zero‑day vulnerabilities in on‑premises SharePoint servers to target critical infrastructure—affecting hundreds of organizations and raising alarms over national security and economic disruption....



Rising airfare, political frustration, and lack of confidence in public services push thousands of Moroccan immigrants to skip summer visits home By El Mostafa Ouchen |...



New cross-platform malware strains abuse PostgreSQL, Tomcat, JupyterLab, and Confluence to hijack compute power for cryptocurrency mining—leaving cloud workloads vulnerable and detection difficult. 🧨 Introduction: Clouds...



RABAT — July 26, 2025 In a landmark step toward digital transformation, Morocco’s National Telecommunications Regulatory Agency (ANRT) has officially launched the bidding process for 5G...



In preparation to co-host the 2030 World Cup, Morocco is investing 38 billion dirhams to double its airport capacity, aiming to position itself as a global...



The ambitious MAD 38 billion investment aims to transform Morocco’s air travel infrastructure, enhance passenger experience, and position the country as a premier global tourism and...



The Kingdom’s ambitious “Maroc Digital 2030” strategy aims to extend 5G coverage to 85% of its population, promising socio-economic transformation and digital inclusivity across urban and...
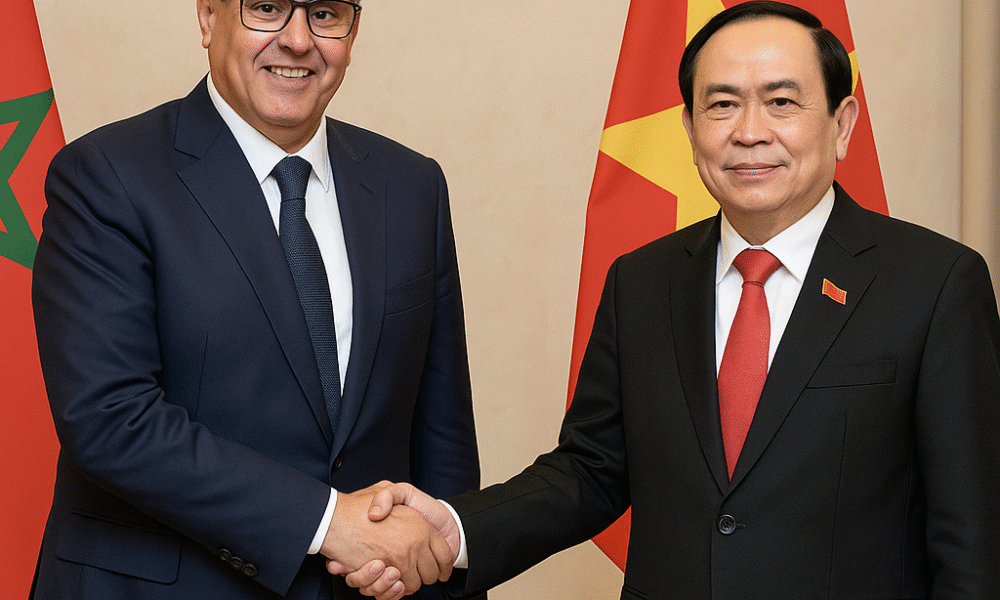


Prime Minister Aziz Akhannouch meets with Vietnamese National Assembly President Tran Thanh Man to expand economic, diplomatic, and parliamentary cooperation. By El Mostafa Ouchen | MAG212NEWS...



A youth jobs program meant to empower teens became the gateway to one of New York City’s largest ATM frauds—leaving behind shock, unanswered questions, and a...


Forensic investigations reveal how attackers exploited a SharePoint flaw using PowerShell, web shells, and lateral movement—now joined by ransomware payloads. We explain the exploit chain, with...