


AI, data, cybersecurity and project management lead the list as employers prioritize job-ready skills. Here are high-quality Coursera courses you can audit for free—plus how to...
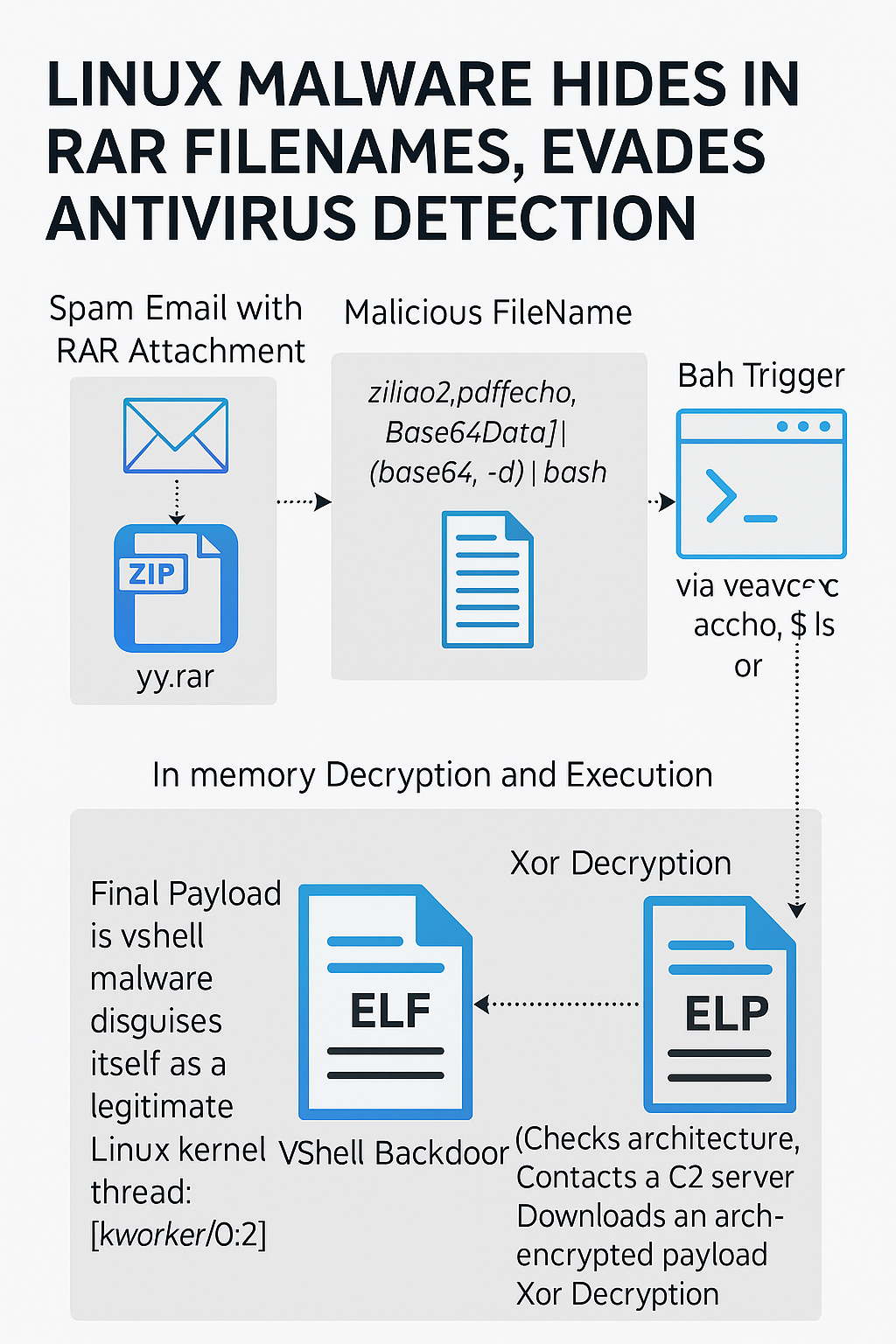


Trellix says a phishing campaign weaponizes RAR archive filenames to auto-trigger Bash, fetch a multi-arch loader, and execute the VShell backdoor entirely in memory. A new...
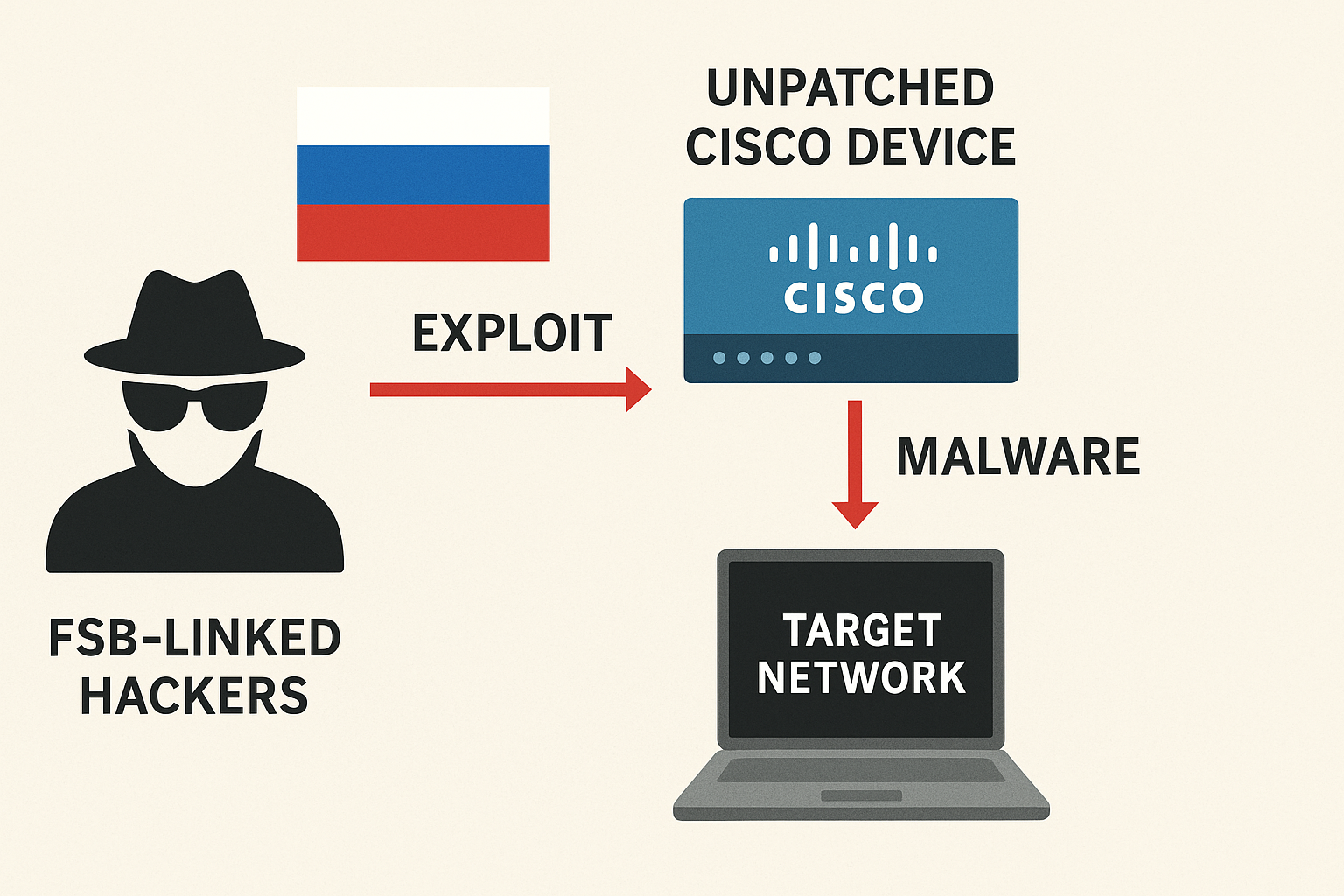


“Static Tundra,” tied to Russia’s FSB Center 16, is abusing a 2018 Cisco Smart Install bug to loot configs and plant router implants across critical infrastructure,...



Threat actors abuse misconfigurations and living-off-the-land tools—using fake 404 pages and panda JPEG “polyglot” files—to drop miners on Linux and Windows at scale. Twin campaigns dubbed...



Two-day February intrusion leaked financial and medical details; group begins notifications and offers credit monitoring as regulators are alerted. The Business Council of New York State...



Leaked SIM and PUK data heighten SIM-swapping risks as critics fault Orange’s response; company says no passwords, emails or banking data were taken. Orange Belgium disclosed...



Attackers use CVE-2023-46604 to breach Linux cloud hosts, drop “DripDropper” malware, and quietly fix the flaw to lock in access, researchers say. Threat actors are abusing...



Contact data for ~280k email accounts and 1.7k modem passwords accessed; breach isolated to iiNet order system, company says Australia’s TPG Telecom disclosed unauthorized access to...
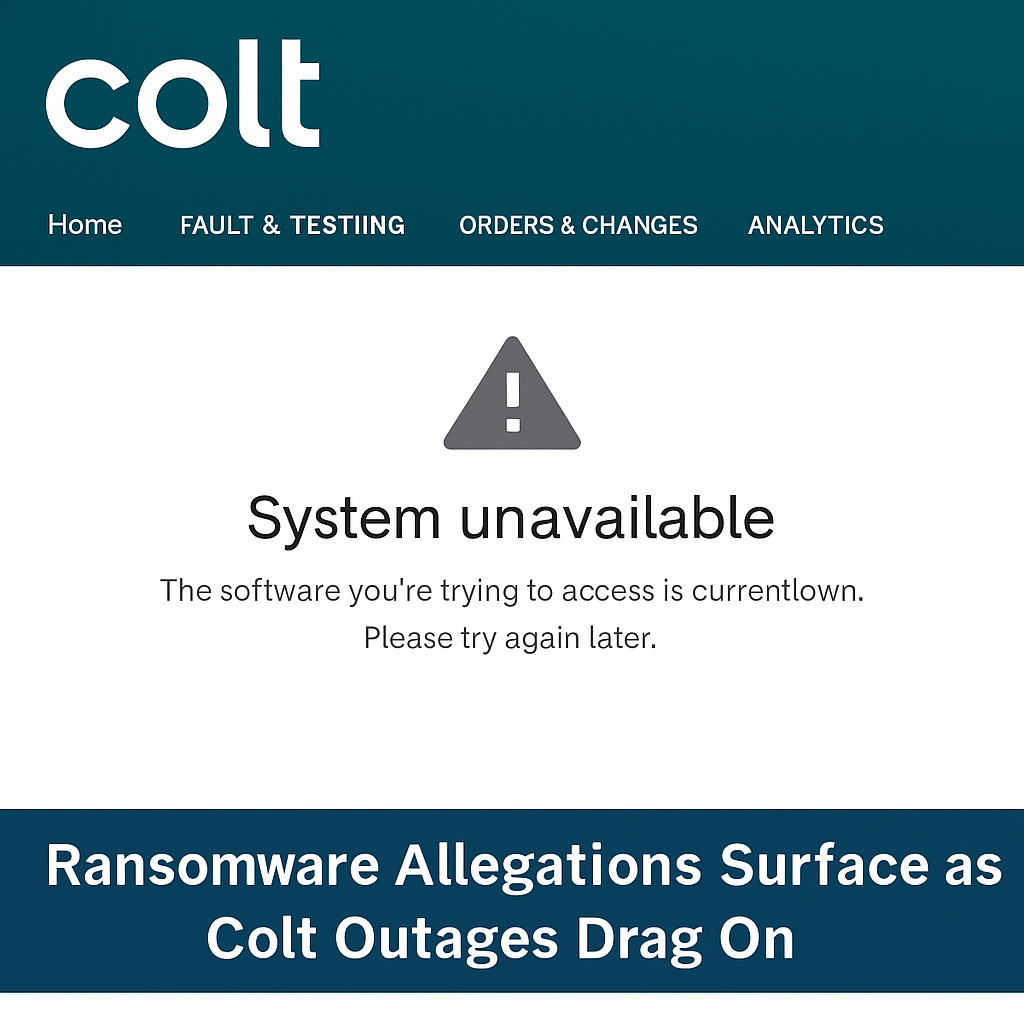


Colt Technology Services’ internal systems remain down after a suspected ransomware attack; WarLock gang claims to have stolen 1 million documents, demanding $200K ransom Colt Technology...
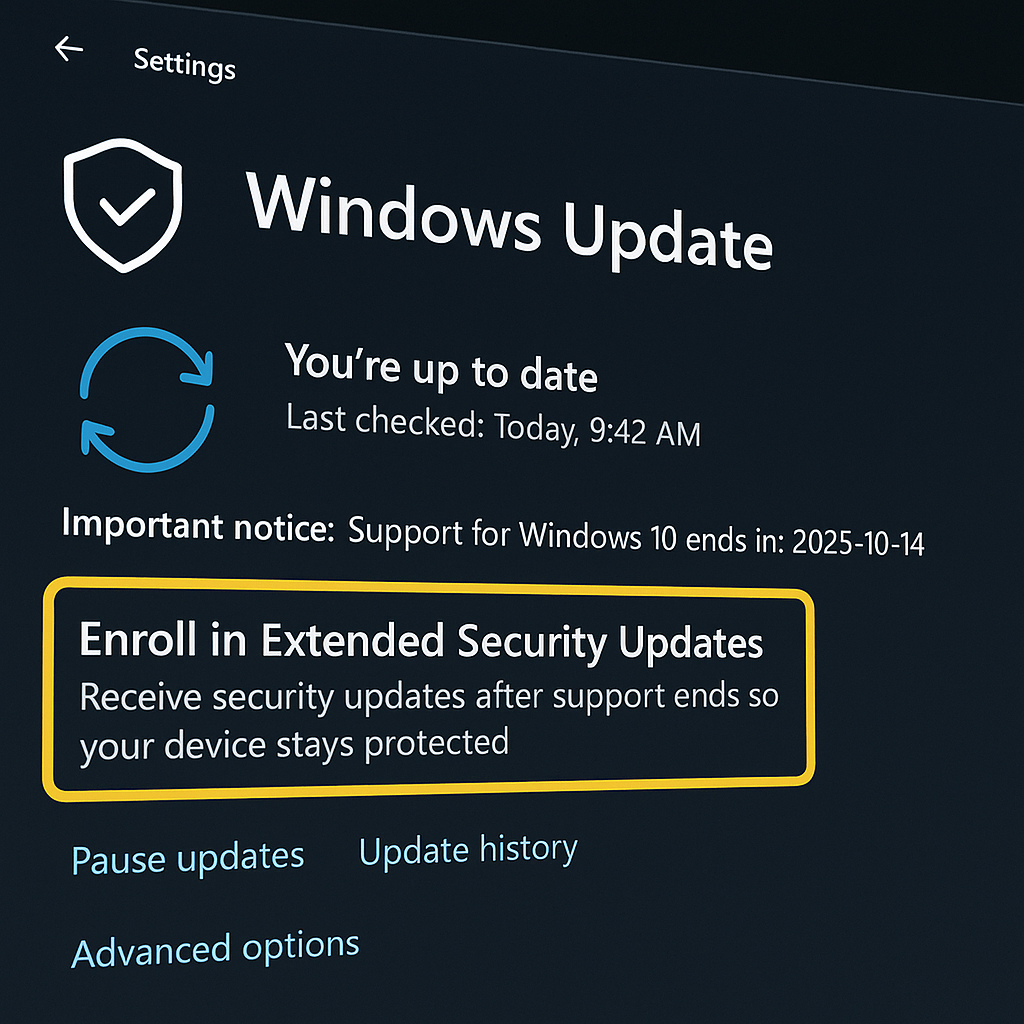


Free support ends October 14, 2025; new KB5063709 unlocks Extended Security Updates enrollment to keep critical patches flowing through October 2026. Microsoft is warning Windows 10...