


RABAT — July 26, 2025 In a landmark step toward digital transformation, Morocco’s National Telecommunications Regulatory Agency (ANRT) has officially launched the bidding process for 5G...



The Kingdom’s ambitious “Maroc Digital 2030” strategy aims to extend 5G coverage to 85% of its population, promising socio-economic transformation and digital inclusivity across urban and...
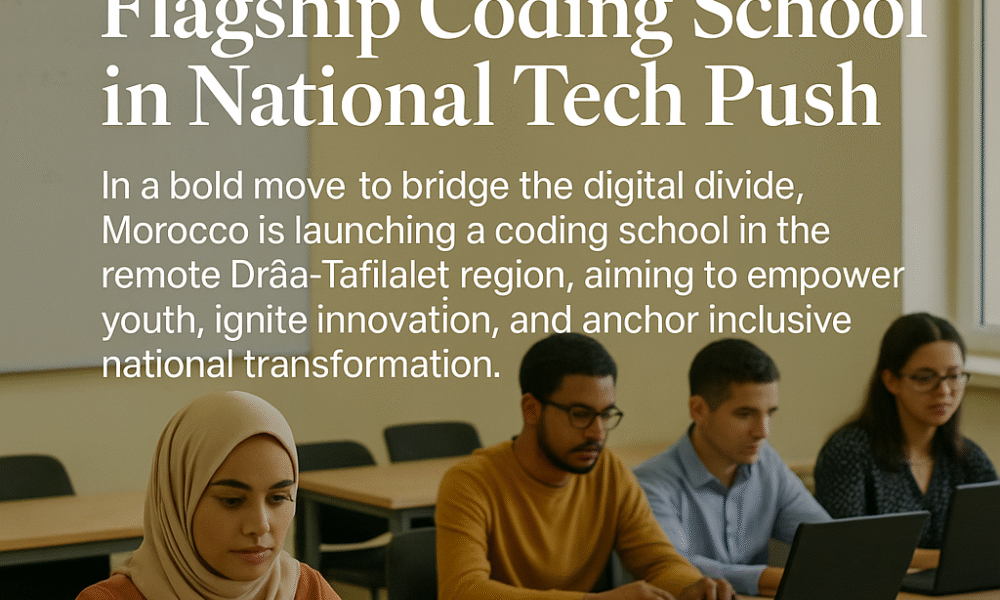


In a bold move to bridge the digital divide, Morocco is launching a coding school in the remote Drâa-Tafilalet region, aiming to empower youth, ignite innovation,...
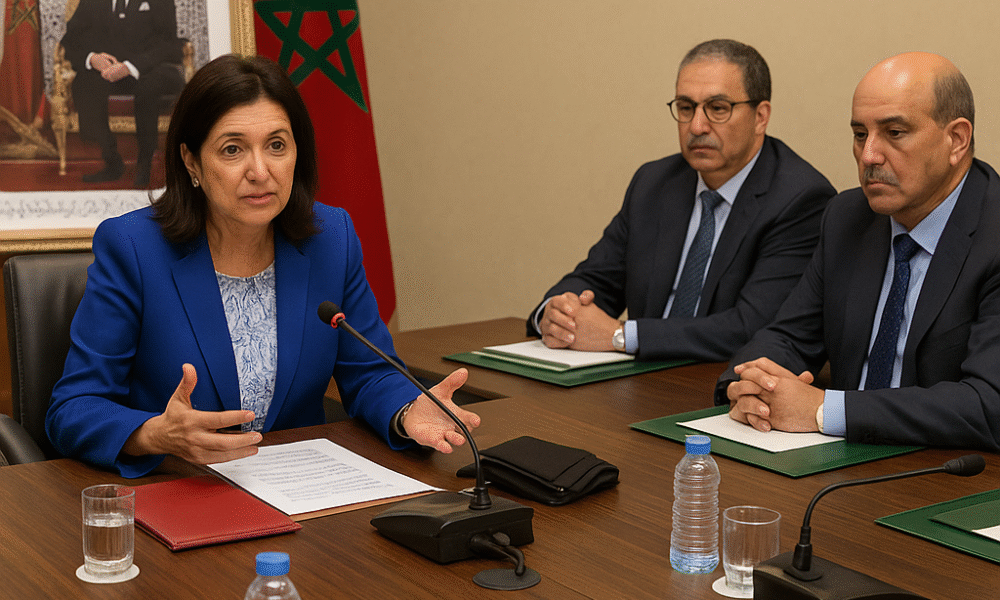

A strategic meeting in Rabat brings together government and regional leaders to advance digital transformation and foster youth inclusion through coding schools across Drâa-Tafilalet. Rabat |...
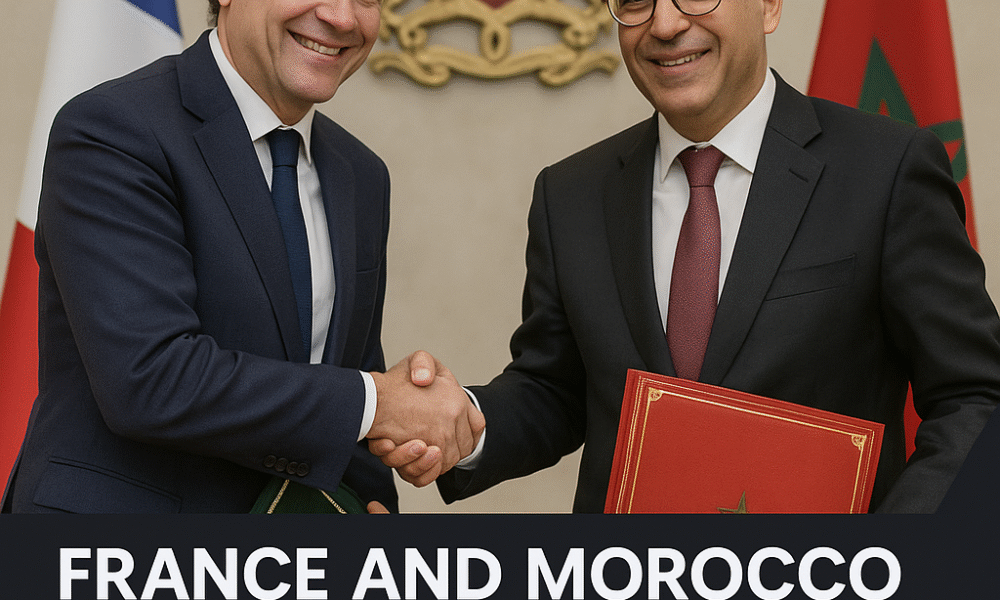


A landmark MoU signed in Rabat paves the way for a major Franco-Moroccan partnership to establish a Center of Excellence in Data and Artificial Intelligence, positioning...



As cyberattacks grow in scale and complexity, leading cybersecurity firms are turning to cutting-edge attack simulation tools like SafeBreach, XM Cyber, and CALDERA to preempt threats,...



State-backed threat actors exploit two Ivanti Connect Secure vulnerabilities to breach high-value networks, steal credentials, and drop sophisticated malware—raising alarms over critical infrastructure defense worldwide. Global...
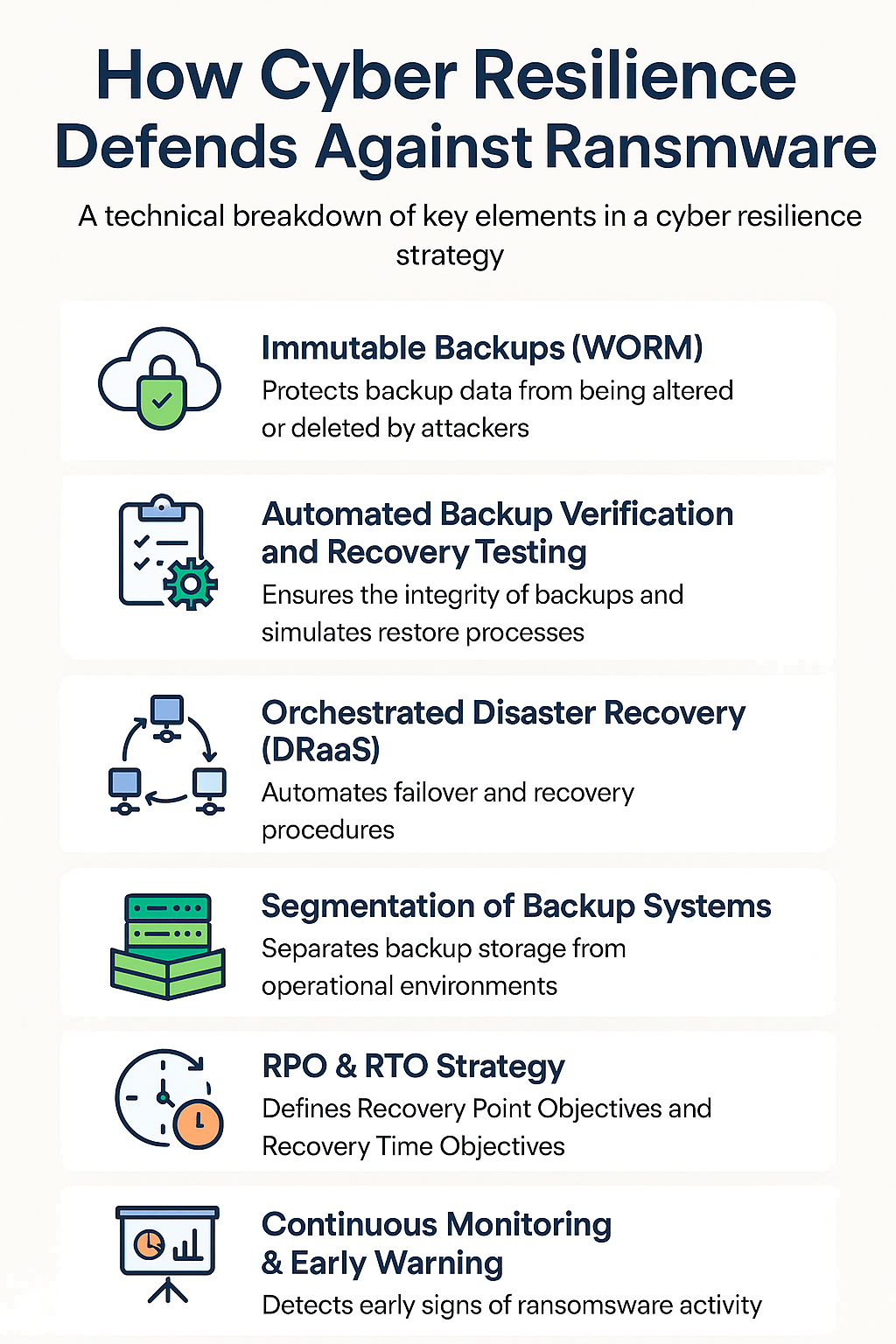


As ransomware actors escalate attacks on backups and recovery systems, IT leaders worldwide are pivoting from traditional backup strategies to holistic cyber resilience frameworks to safeguard...
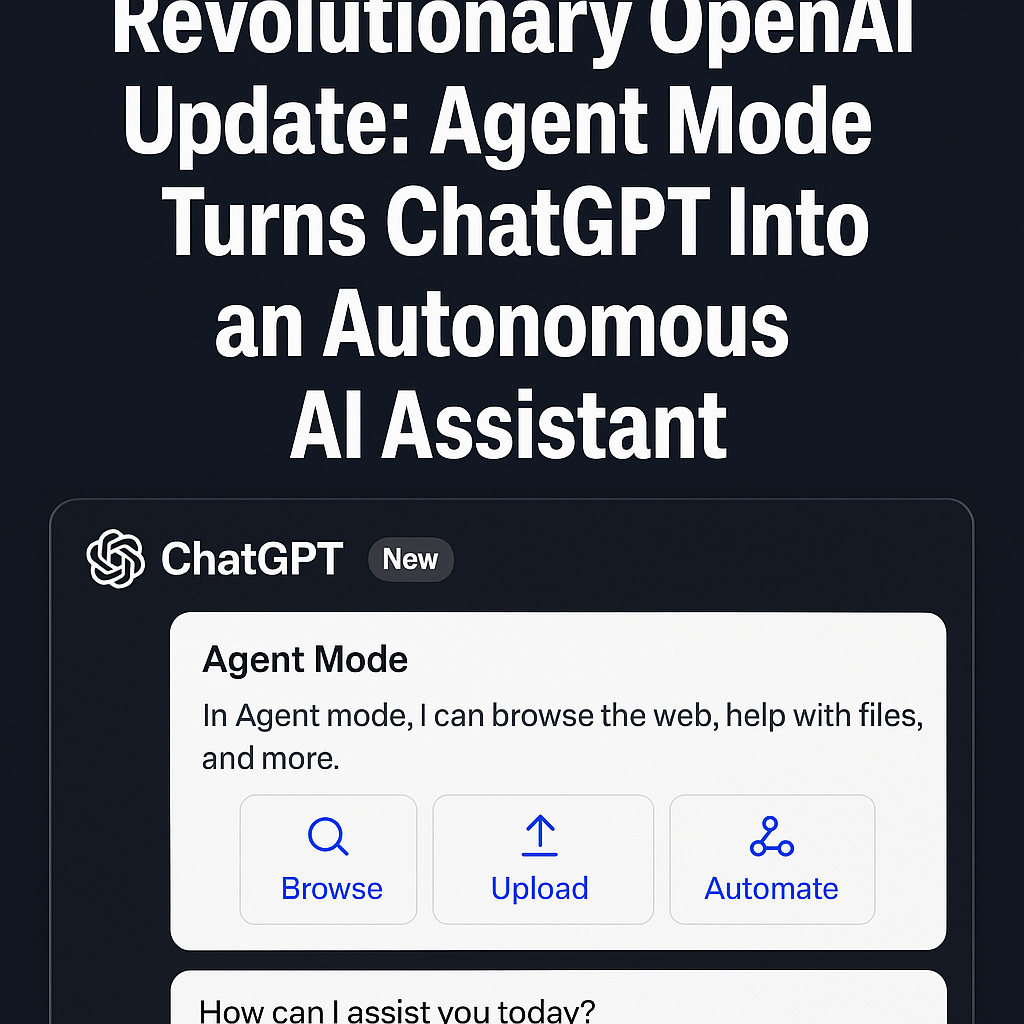


With integrated browsing, file management, and real-world tool access, OpenAI’s new Agent Mode may redefine the role of AI in daily productivity, software development, and human-computer...


Cybercriminals are using fileless malware embedded in email chains to bypass security systems, compromising businesses and individuals across multiple sectors. “Reply Chain” Malware Attacks Infiltrate Email...