data breaches
Annual Pen Tests Can’t Stop Modern Attacks. Here’s the Better Way

Security experts urge a shift from once-a-year audits to continuous 24/7 defense. Organizations are being pushed to build “Offensive SOC” teams that hunt threats proactively, aligning cybersecurity operations with real-time adversary behavior.
Excerpt: Cybersecurity leaders worldwide are warning that the old practice of annual penetration testing can no longer keep businesses safe in the face of daily-evolving cyber threats. Instead of “playing defense” once a year, companies are being urged to adopt an always-on approach – establishing Offensive Security Operations Centers that hunt hackers around the clock. The move from reactive annual audits to proactive 24/7 threat hunting, experts say, is vital to protect sensitive data and maintain customer trust in an era of nonstop cyberattacks.
LONDON, UK – At 2:00 AM on a chilly winter night, the security team at a European financial firm stared in disbelief as hackers breached their network – exploiting a software flaw announced just days earlier. The twist: the company had passed its annual penetration test only a month before. This harrowing incident underscores a growing consensus in the cybersecurity community: annual security tests are no longer enough. With new threats emerging every day, experts say organizations must replace once-yearly audits with continuous, aggressive defense if they hope to keep hackers at bay.
“That’s not defense. It’s theater,” quips one industry analyst, lamenting how many companies still treat offensive security as a one-off exercise. In the real world, attackers don’t operate on a yearly schedule – their reconnaissance is continuous, their tactics adapt weekly or even hourly, and they often weaponize freshly disclosed vulnerabilities within hours of a patch release. By the time an annual pen test report is written and delivered, the network it assessed may have changed drastically. “You’re chasing what was, not what is,” as one report put it, likening yearly tests to checking last month’s security camera footage to see what’s happening today.
Evolving Threats Expose the Gaps in Yearly Testing
The pace of cyber threats has become blistering. In 2024 alone, over 40,000 new software vulnerabilities (CVEs) were disclosed – a 38% jump from the previous year – averaging more than 100 new flaws every day. Alarmingly, about 28% of those vulnerabilities were **exploited by attackers within 24 hours of public disclosure]. This means that if your organization’s last penetration test was even a few weeks ago, it likely missed dozens of critical new weaknesses. “Pen tests conducted once a year leave serious gaps in security posture,” notes Chris Dale, a SANS Institute instructor, adding that the traditional reactive testing cycle “doesn’t align with the agile, continuous innovation of modern businesses”.
Real-world incidents bear out the danger of these gaps. In June 2023, for example, criminals seized on a zero-day flaw in a popular file-transfer tool and compromised over 620 organizations within days, including global firms like the BBC and British Airways. Back in 2013, U.S. retailer Target infamously suffered a massive breach exposing 110 million customers’ data – just weeks after auditors had certified the company’s security as PCI compliant. The lesson, experts say, is that compliance checkboxes and one-time tests provide only a “snapshot in time” of security. Unless defenses are maintained and continuously validated, new gaps will inevitably appear – and attackers will find them.
“Attackers certainly don’t limit themselves to one attempt per year – they are probing continuously,” a report by Apollo Security notes dryly. In fact, studies show cyber intruders are bombarding businesses relentlessly – an estimated 2,200 attacks per day, or one attack every 39 seconds on average. Meanwhile, IT environments are changing faster than ever: companies like Netflix have shifted from releasing software every few weeks to deploying updates daily, and Amazon is rumored to push new code every few minutes. “It’s now impossible to keep security risk mitigation running at the same pace as development” using ad-hoc yearly tests. When your systems, apps, and users are in constant flux, a once-a-year checkup simply can’t catch all the silent drift – the misconfigurations, forgotten assets, or weak points that accumulate over time. Little wonder, then, that a recent survey found 43% of companies still only test once or twice a year (often just to meet compliance), while only a small vanguard – 17% – conduct security testing weekly or daily.
The human and business impacts of this status quo are profound. Data breaches resulting from unaddressed vulnerabilities can expose millions of people’s personal information and cost companies fortunes. IBM’s 2023 analysis put the average cost of a corporate data breach at $4.45 million. In Target’s case, the fallout from its breach – beyond the $18.5 million legal settlement – included an estimated $200 million in total damages and a 46% drop in quarterly profits as customers’ trust plummeted. “Compliance alone isn’t enough for robust security,” says a security consultant. “It might satisfy auditors, but it won’t stop real attackers in between those audits.” In short, the threat is continuous – and defense must be as well.
From Annual Checkups to an Offensive SOC: Hunt Threats 24/7
Facing this reality, leading organizations and experts are advocating a dramatic shift in strategy: move from reactive to proactive, from occasional testing to continuous threat hunting. In practice, this means standing up an Offensive Security Operations Center (OSOC) – a dedicated team (and toolkit) that doesn’t just monitor for intrusions, but actively imitates attackers every single day to find and fix weaknesses before the bad guys do. “If a traditional SOC raises alerts on attacks that do reach you, the Offensive SOC raises alerts on vulnerabilities that could,” explains one industry report, highlighting the forward-looking mandate of such teams.
An Offensive SOC essentially flips the script: instead of waiting for alarms after an attack has occurred, the security team is constantly on the offensive, identifying cracks in the armor through simulated attacks, red-team exercises, and rigorous validation of defenses in real time. “The shift to an Offensive SOC with continuous validation is key to real-time visibility and resilience,” says Rajiv Shah, a cybersecurity operations lead. Today’s attackers don’t wait for your next assessment, so neither can you. The approach is collaborative and iterative – often combining automated tools with human expertise – to uncover tangible risks and drive fixes continuously. Crucially, this doesn’t abolish traditional pen testing; it augments it. By automating the routine and continuous checks, companies free up human pen-testers to focus on creative, complex attack scenarios that no script could cover. “An Offensive SOC doesn’t replace pentesting – it gives it room to evolve,” as The Hacker News noted.
Key Pillars of a Proactive Defense
Security leaders outline several fundamental shifts for organizations building a 24/7 proactive defense:
- Shift from Reactive to Proactive: Instead of primarily reacting to incidents and compliance mandates, teams actively hunt for threats and weaknesses before any breach occurs. This cultural change means anticipating attackers’ moves and consistently testing one’s own systems in the same aggressive way. “Most organizations have adopted a reactive stance – placing damage control over preventative vigilance,” observes a World Economic Forum report. A proactive posture flips that priority to prevention first.
- Continuously Hunt and Neutralize Threats: Adopt a continuous monitoring and testing regimen. This can involve automated breach simulations and “attack surface” scans running daily, as well as an internal “red team” or external service conducting frequent micro-pentests. The goal is to identify vulnerabilities or suspicious activity in real time and remediate immediately, shrinking the window of exposure from months to days or hours. For example, adversary simulation platforms now let companies safely execute the same techniques used by hackers – from ransomware attacks to credential theft – in their production environment to see if defenses hold up.
- Align Security with Real-Time Adversary Behavior: Keep defense tactics and tools calibrated to the latest attacker techniques. Cybercriminals constantly update their arsenal – from novel phishing lures to AI-driven malware – so security operations must continuously learn and adapt as well. This might mean integrating threat intelligence feeds about emerging exploits, using frameworks like MITRE ATT&CK to emulate current tactics, and ensuring detection rules and response plans evolve as attackers do. “Adversarial exposure validation (AEV) delivers consistent, continuous and automated evidence of the feasibility of an attack,” noted Gartner analysts in a 2025 report, urging firms to focus on validated, real-world attack scenarios rather than theoretical risks. In practice, this means regularly confirming how an attacker today would break in – and adjusting defenses to counter those techniques in real time.
This continuous, offense-oriented model marks a stark departure from the traditional SOC of the past. A conventional Security Operations Center is built to react – it watches dashboards for intrusions and responds to incidents. In contrast, an Offensive SOC is built to act first – constantly stress-testing the organization’s own defenses through simulated attacks, probing for weaknesses, and generating its own alerts when it finds a crack or lapse. The approach has been compared to having a “sparring partner” for your security: always training, never complacent.
“We’re essentially institutionalizing the hacker mindset within the defense team,” says Maria Torres, a chief information security officer who implemented an Offensive SOC at a large telecom firm. Her team runs mock attacks on the company’s infrastructure every week. “If we can break into our own systems today, we make sure to fix that by tomorrow – rather than waiting for a real attacker to do it.” The payoff has been significant, Torres notes: the company’s incident response times have plummeted, and previously unknown vulnerabilities are getting discovered and patched on a rolling basis. It’s a proactive ethos that industry data suggests many organizations will need to adopt. Gartner, for instance, predicts a convergence of automated pentesting tools and breach simulation into unified solutions that feed continuous improvement – effectively bringing this Offensive SOC capability within reach for more enterprises.
A New Era of Cyber Defense – and What’s at Stake
The broader significance of this shift extends far beyond IT departments. In an age where almost every aspect of business and daily life depends on digital technology, cybersecurity is no longer just a technical issue – it’s a fundamental pillar of consumer safety, trust, and economic stability. When security testing fails to keep up with threats, real people are hurt: hospital patients have had treatments delayed by ransomware attacks; energy pipeline shutdowns have caused fuel shortages; personal data leaks have led to identity theft and financial ruin for individuals. Eternal vigilance, it turns out, is not just an ideal – it’s becoming a basic requirement for doing business responsibly in the digital era.
The encouraging news is that more organizations are waking up to this reality. Nearly 80% of large enterprises are now exploring some form of “continuous security validation” – whether through in-house red teams, managed services, or emerging automated platforms – according to industry surveys. Companies in high-risk sectors like finance and healthcare, in particular, are moving beyond the annual checklist and embracing ongoing offensive testing to safeguard the sensitive data they hold. Regulators, too, are beginning to recognize the need for continuous assurance: several standards bodies have started recommending more frequent security assessments, and newer frameworks stress continuous monitoring and improvement as core principles.
Still, challenges remain. Building an Offensive SOC capability requires investment and a shift in mindset. There can be resistance from executives used to thinking of security tests as something you “pass” once a year, or from engineers worried that constant testing could disrupt operations. Security teams also need the right mix of tools and talent – including people skilled in thinking like hackers. And organizations must be careful to avoid “alert fatigue” by prioritizing which simulated findings to tackle first. It’s a demanding effort, no doubt. But the cost of not doing it, experts argue, is far greater.
In the end, the push to retire the annual pen test in favor of 24/7 proactive defense is about building resilience in a world of ceaseless cyber onslaughts. It’s about ensuring that one day’s security report isn’t tomorrow’s hacker road map. “We have to be right every day; attackers only need to be right once,” says Torres. Her words echo a sobering truth heard often in security circles. By operationalizing continuous offense – effectively letting your defenders “be the attackers” too – organizations can flip that script and drastically improve their odds. They gain visibility into their weaknesses in real time, and they can fix them before they’re exploited for real. As momentum builds behind the Offensive SOC movement, the message to businesses is clear: stop playing defense once a year. The adversaries evolve daily – so must your defenses. Build resilience. Build visibility. Build your Offensive Security Operations Center.
📘 Core Sources
- Apollo Security explains how annual pen tests leave organizations exposed to new CVEs—over 40,000 disclosed in 2024—of which approximately 28% are exploited within 24 hours. They also highlight how pen tests become quickly outdated in dynamic environments Cymulate+1CyberProof+1blog.wei.com+7ApolloSec+7SANS Institute+7.
- SANS Institute (Continuous Penetration Testing and the Rise of the Offensive SOC) outlines the evolution from annual assessments to year‑round offensive operations, detailing how an Offensive SOC integrates continuous attack surface management (ASM) with proactive testing Linford & Co.+2SANS Institute+2SANS Institute+2.
- The Hacker News discusses limitations of traditional pentesting—such as slow engagement timelines and narrow scope—and contrasts them with continuous, automated testing The Hacker News+1Horizon3.ai+1.
data breaches
Cloudflare Outage Disrupts Global Internet — Company Restores Services After Major Traffic Spike

November 18, 2025 — MAG212NEWS
A significant outage at Cloudflare, one of the world’s leading internet infrastructure providers, caused widespread disruptions across major websites and online services on Tuesday. The incident, which began mid-morning GMT, temporarily affected access to platforms including ChatGPT, X (formerly Twitter), and numerous business, government, and educational services that rely on Cloudflare’s network.
According to Cloudflare, the outage was triggered by a sudden spike in “unusual traffic” flowing into one of its core services. The surge caused internal components to return 500-series error messages, leaving users unable to access services across regions in Europe, the Middle East, Asia, and North America.
Impact Across the Web
Because Cloudflare provides DNS, CDN, DDoS mitigation, and security services for millions of domains — powering an estimated 20% of global web traffic — the outage had swift and wide-reaching effects.
Users reported:
- Website loading failures
- “Internal Server Error” and “Bad Gateway” messages
- Slowdowns on major social platforms
- Inaccessibility of online tools, APIs, and third-party authentication services
The outage also briefly disrupted Cloudflare’s own customer-support portal, highlighting the interconnected nature of the company’s service ecosystem.
Cloudflare’s Response and Restoration
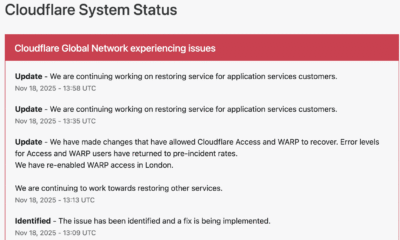
Cloudflare responded within minutes, publishing updates on its official status page and confirming that engineering teams were investigating the anomaly.
The company took the following steps to restore operations:
1. Rapid Detection and Acknowledgement
Cloudflare engineers identified elevated error rates tied to an internal service degradation. Public communications were issued to confirm the outage and reassure customers.
2. Isolating the Affected Systems
To contain the disruption, Cloudflare temporarily disabled or modified specific services in impacted regions. Notably, the company deactivated its WARP secure-connection service for users in London to stabilize network behavior while the fix was deployed.
3. Implementing Targeted Fixes
Technical teams rolled out configuration changes to Cloudflare Access and WARP, which successfully reduced error rates and restored normal traffic flow. Services were gradually re-enabled once systems were verified stable.
4. Ongoing Root-Cause Investigation
While the unusual-traffic spike remains the confirmed trigger, Cloudflare stated that a full internal analysis is underway to determine the exact source and prevent a recurrence.
By early afternoon UTC, Cloudflare confirmed that systems had returned to pre-incident performance levels, and affected services worldwide began functioning normally.
Why This Matters
Tuesday’s outage underscores a critical truth about modern internet architecture: a handful of infrastructure companies underpin a massive portion of global online activity. When one of them experiences instability — even briefly — the ripple effects are immediate and worldwide.
For businesses, schools, governments, and content creators, the incident is a reminder of the importance of:
- Redundant DNS/CDN providers
- Disaster-recovery and failover plans
- Clear communication protocols during service outages
- Vendor-dependency risk assessments
Cloudflare emphasized that no evidence currently points to a cyberattack, though the nature of the traffic spike remains under investigation.
Looking Ahead
As Cloudflare completes its post-incident review, the company is expected to provide a detailed breakdown of the technical root cause and outline steps to harden its infrastructure. Given Cloudflare’s central role in global internet stability, analysts say the findings will be watched closely by governments, cybersecurity professionals, and enterprise clients.
For now, services are restored — but the outage serves as a powerful reminder of how interconnected and vulnerable the global web can be.
data breaches
Cloudflare Outage Analysis: Systemic Failure in Edge Challenge Mechanism Halts Global Traffic
SAN FRANCISCO, CA — A widespread disruption across major internet services, including AI platform ChatGPT and social media giant X (formerly Twitter), has drawn critical attention to the stability of core internet infrastructure. The cause traces back to a major service degradation at Cloudflare, the dominant content delivery network (CDN) and DDoS mitigation provider. Users attempting to access affected sites were met with an opaque, yet telling, error message: “Please unblock challenges.cloudflare.com to proceed.”
This incident was not a simple server crash but a systemic failure within the crucial Web Application Firewall (WAF) and bot management pipeline, resulting in a cascade of HTTP 5xx errors that effectively severed client-server connections for legitimate users.
The Mechanism of Failure: challenges.cloudflare.com
The error message observed globally points directly to a malfunction in Cloudflare’s automated challenge system. The subdomain challenges.cloudflare.com is central to the company’s security and bot defense strategy, acting as an intermediate validation step for traffic suspected of being malicious (bots, scrapers, or DDoS attacks).
This validation typically involves:
- Browser Integrity Check (BIC): A non-invasive test ensuring the client browser is legitimate.
- Managed Challenge: A dynamic, non-interactive proof-of-work check.
- Interactive Challenge (CAPTCHA): A final, user-facing verification mechanism.
In a healthy system, a user passing through Cloudflare’s edge network is either immediately granted access or temporarily routed to this challenge page for verification.
During the outage, however, the Challenge Logic itself appears to have failed at the edge of Cloudflare’s network. When the system was invoked (likely due to high load or a misconfiguration), the expected security response—a functional challenge page—returned an internal server error (a 500-level status code). This meant:
- The Request Loop: Legitimate traffic was correctly flagged for a challenge, but the server hosting the challenge mechanism failed to process or render the page correctly.
- The
HTTP 500Cascade: Instead of displaying the challenge, the Cloudflare edge server returned a “500 Internal Server Error” to the client, sometimes obfuscated by the text prompt to “unblock” the challenges domain. This effectively created a dead end, blocking authenticated users from proceeding to the origin server (e.g., OpenAI’s backend for ChatGPT).
Technical Impact on Global Services
The fallout underscored the concentration risk inherent in modern web architecture. As a reverse proxy, Cloudflare sits between the end-user and the origin server for a vast percentage of the internet.
For services like ChatGPT, which rely heavily on fast, secure, and authenticated API calls and constant data exchange, the WAF failure introduced severe latency and outright connection refusal. A failure in Cloudflare’s global network meant that fundamental features such as DNS resolution, TLS termination, and request routing were compromised, leading to:
- API Timeouts: Applications utilizing Cloudflare’s API for configuration or deployment experienced critical failures.
- Widespread Service Degradation: The systemic 5xx errors at the L7 (Application Layer) caused services to appear “down,” even if the underlying compute resources and databases of the origin servers remained fully operational.
Cloudflare’s official status updates confirmed they were investigating an issue impacting “multiple customers: Widespread 500 errors, Cloudflare Dashboard and API also failing.” While the exact trigger was later traced to an internal platform issue (in some historical Cloudflare incidents, this has been a BGP routing error or a misconfigured firewall rule pushed globally), the user-facing symptom highlighted the fragility of relying on a single third-party for security and content delivery on a global scale.
Mitigation and the Single Point of Failure
While Cloudflare teams worked to roll back configuration changes and isolate the fault domain, the incident renews discussion on the “single point of failure” doctrine. When a critical intermediary layer—responsible for security, routing, and caching—experiences a core logic failure, the entire digital economy resting on it is exposed.
Engineers and site reliability teams are now expected to further scrutinize multi-CDN and multi-cloud strategies, ensuring that critical application traffic paths are not entirely dependent on a single third-party’s edge infrastructure, a practice often challenging due to cost and operational complexity. The “unblock challenges” error serves as a stark reminder of the technical chasm between a user’s browser and the complex, interconnected security apparatus that underpins the modern web.
data breaches
Manufacturing Software at Risk from CVE-2025-5086 Exploit
Dassault Systèmes patches severe vulnerability in Apriso manufacturing software that could let attackers bypass authentication and compromise factories worldwide.
A newly disclosed flaw, tracked as CVE-2025-5086, poses a major security risk to manufacturers using Dassault Systèmes’ DELMIA Apriso platform. The bug could allow unauthenticated attackers to seize control of production environments, prompting urgent patching from the vendor and warnings from cybersecurity experts.
A critical vulnerability in DELMIA Apriso, a manufacturing execution system used by global industries, could let hackers bypass authentication and gain full access to sensitive production data, according to a security advisory published this week.
Dassault Systèmes confirmed the flaw, designated CVE-2025-5086, affects multiple versions of Apriso and scored 9.8 on the CVSS scale, placing it in the “critical” category. Researchers said the issue stems from improper authentication handling that allows remote attackers to execute privileged actions without valid credentials.
The company has released security updates and urged immediate deployment, warning that unpatched systems could become prime targets for industrial espionage or sabotage. The flaw is particularly alarming because Apriso integrates with enterprise resource planning (ERP), supply chain, and industrial control systems, giving attackers a potential foothold in critical infrastructure.
- “This is the kind of vulnerability that keeps CISOs awake at night,” said Maria Lopez, industrial cybersecurity analyst at Kaspersky ICS CERT. “If exploited, it could shut down production lines or manipulate output, creating enormous financial and safety risks.”
- “Manufacturing software has historically lagged behind IT security practices, making these flaws highly attractive to threat actors,” noted James Patel, senior researcher at SANS Institute.
- El Mostafa Ouchen, cybersecurity author, told MAG212News: “This case shows why manufacturing execution systems must adopt zero-trust principles. Attackers know that compromising production software can ripple across supply chains and economies.”
- “We are actively working with customers and partners to ensure systems are secured,” Dassault Systèmes said in a statement. “Patches and mitigations have been released, and we strongly recommend immediate updates.”
Technical Analysis
The flaw resides in Apriso’s authentication module. Improper input validation in login requests allows attackers to bypass session verification, enabling arbitrary code execution with administrative privileges. Successful exploitation could:
- Access or modify production databases.
- Inject malicious instructions into factory automation workflows.
- Escalate attacks into connected ERP and PLM systems.
Mitigations include applying vendor patches, segmenting Apriso servers from external networks, enforcing MFA on supporting infrastructure, and monitoring for abnormal authentication attempts.
Impact & Response
Organizations in automotive, aerospace, and logistics sectors are particularly exposed. Exploited at scale, the vulnerability could cause production delays, supply chain disruptions, and theft of intellectual property. Security teams are advised to scan their environments, apply updates, and coordinate incident response planning.
Background
This disclosure follows a string of high-severity flaws in industrial and operational technology (OT) software, including vulnerabilities in Siemens’ TIA Portal and Rockwell Automation controllers. Experts warn that adversaries—ranging from ransomware gangs to state-sponsored groups—are increasingly focusing on OT targets due to their high-value disruption potential.
Conclusion
The CVE-2025-5086 flaw underscores the urgency for manufacturers to prioritize cybersecurity in factory software. As digital transformation accelerates, securing industrial platforms like Apriso will be critical to ensuring business continuity and protecting global supply chains.