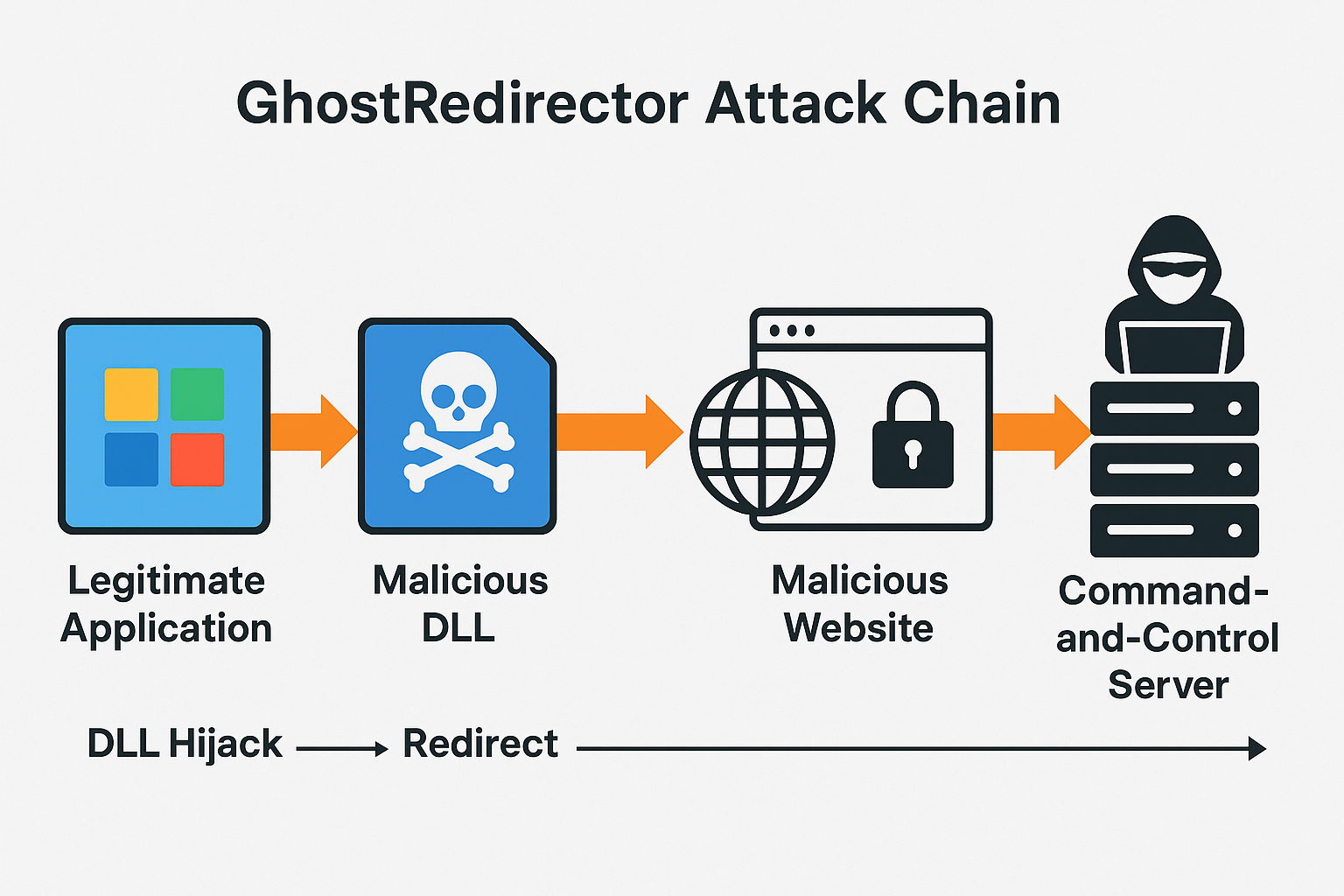


Cybercriminals abuse trusted Windows executables to redirect users, spread malware, and harvest sensitive data. A new malware campaign dubbed GhostRedirector has compromised more than 65 legitimate...
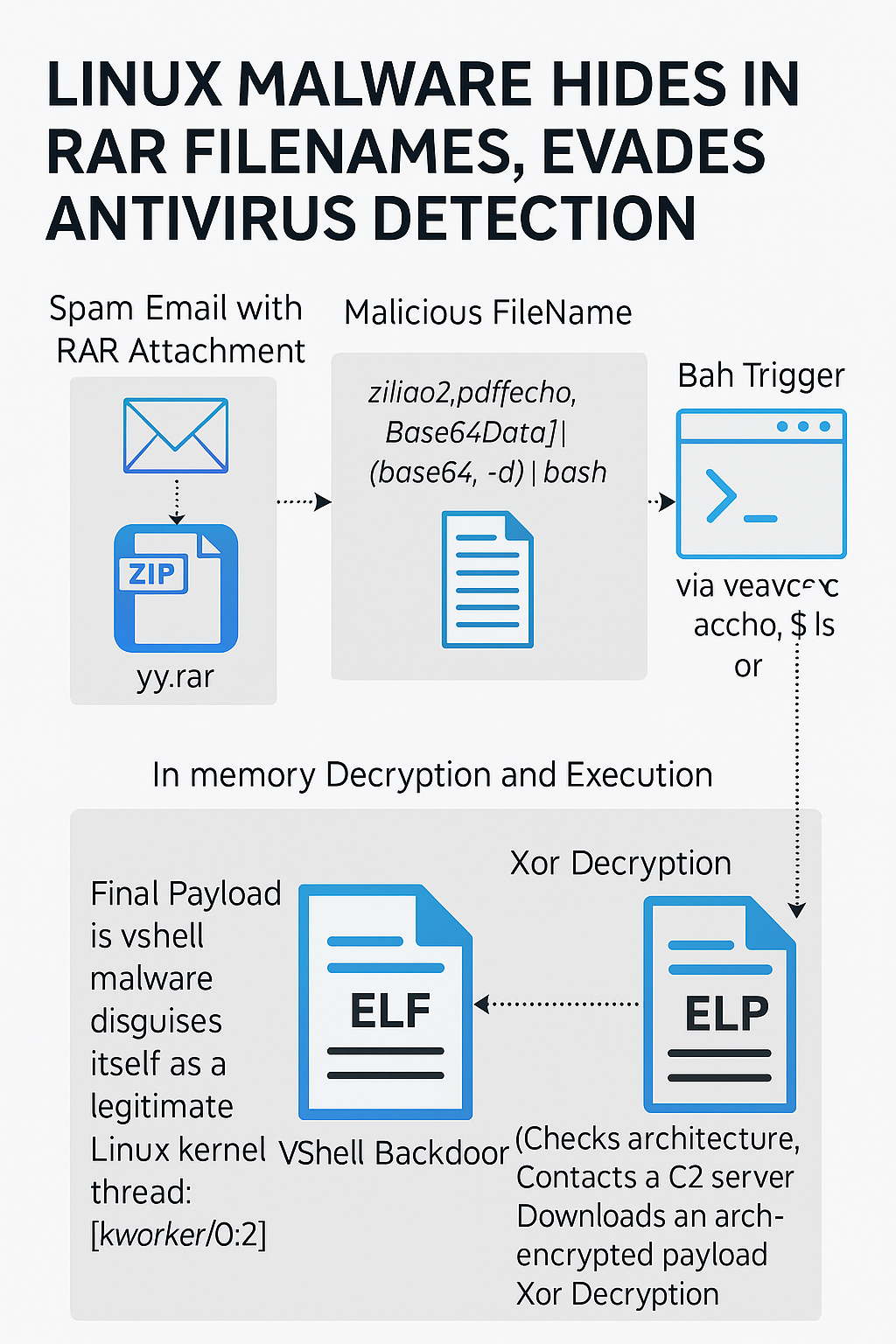


Trellix says a phishing campaign weaponizes RAR archive filenames to auto-trigger Bash, fetch a multi-arch loader, and execute the VShell backdoor entirely in memory. A new...
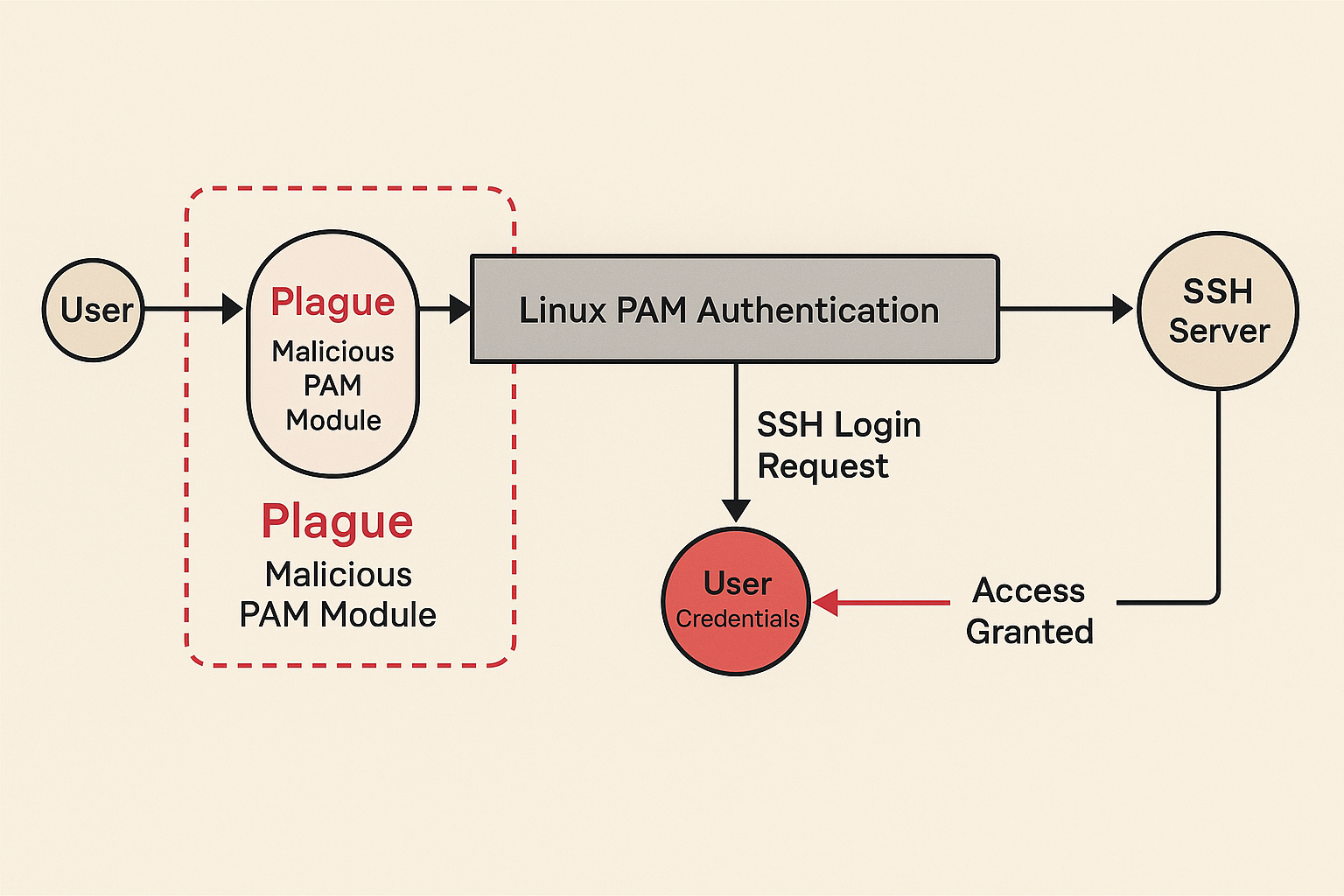


A newly discovered malicious PAM module named “Plague” stealthily hijacks SSH logins, bypasses Linux authentication, and evades antivirus—threatening enterprise servers worldwide with root-level backdoors. It didn’t...


Forensic investigations reveal how attackers exploited a SharePoint flaw using PowerShell, web shells, and lateral movement—now joined by ransomware payloads. We explain the exploit chain, with...



CISA and FBI raise red flags about a new ransomware strain crippling essential services while urging critical sectors to adopt robust defense strategies. Washington D.C. |...



A sophisticated cyberattack campaign, allegedly backed by China, has infiltrated critical systems across Taiwan’s semiconductor and IT sectors, raising global alarm over national security, economic stability,...