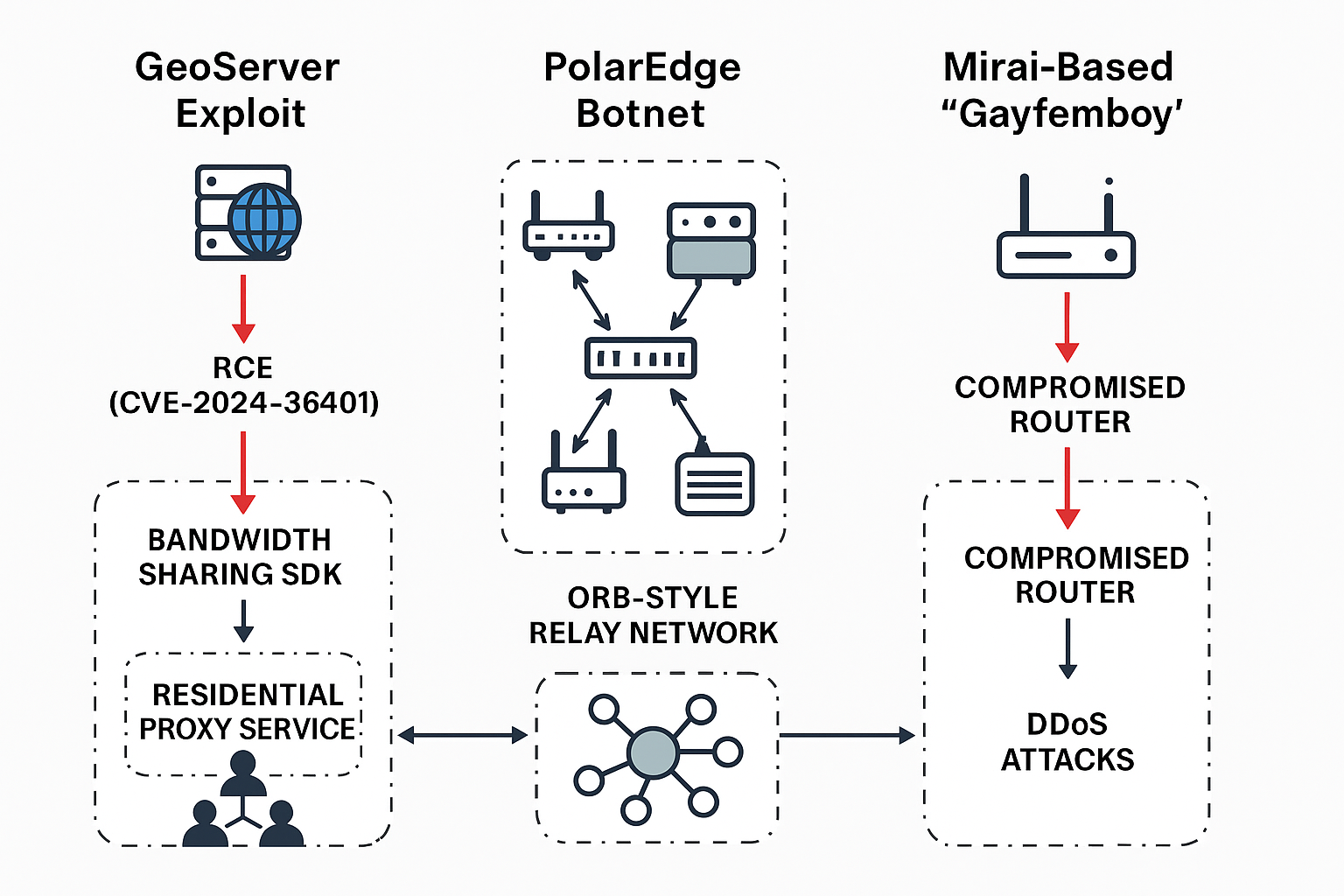


ORB-style relay networks, SDK-based bandwidth theft, and Mirai spin-offs fuel a new wave of silent monetization and stealthy ops Excerpt (40–60 words)Attackers are chaining a critical...



Phone, email, and website went dark as investigators probe links to widely exploited Citrix NetScaler flaws. The Pennsylvania Attorney General’s Office says a cyberattack disabled its...



New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...