


Wiz Research finds an exposed ClickHouse database with 1M+ log lines, including chat histories and secrets—spotlighting human error, weak access controls, and the need for DLP....
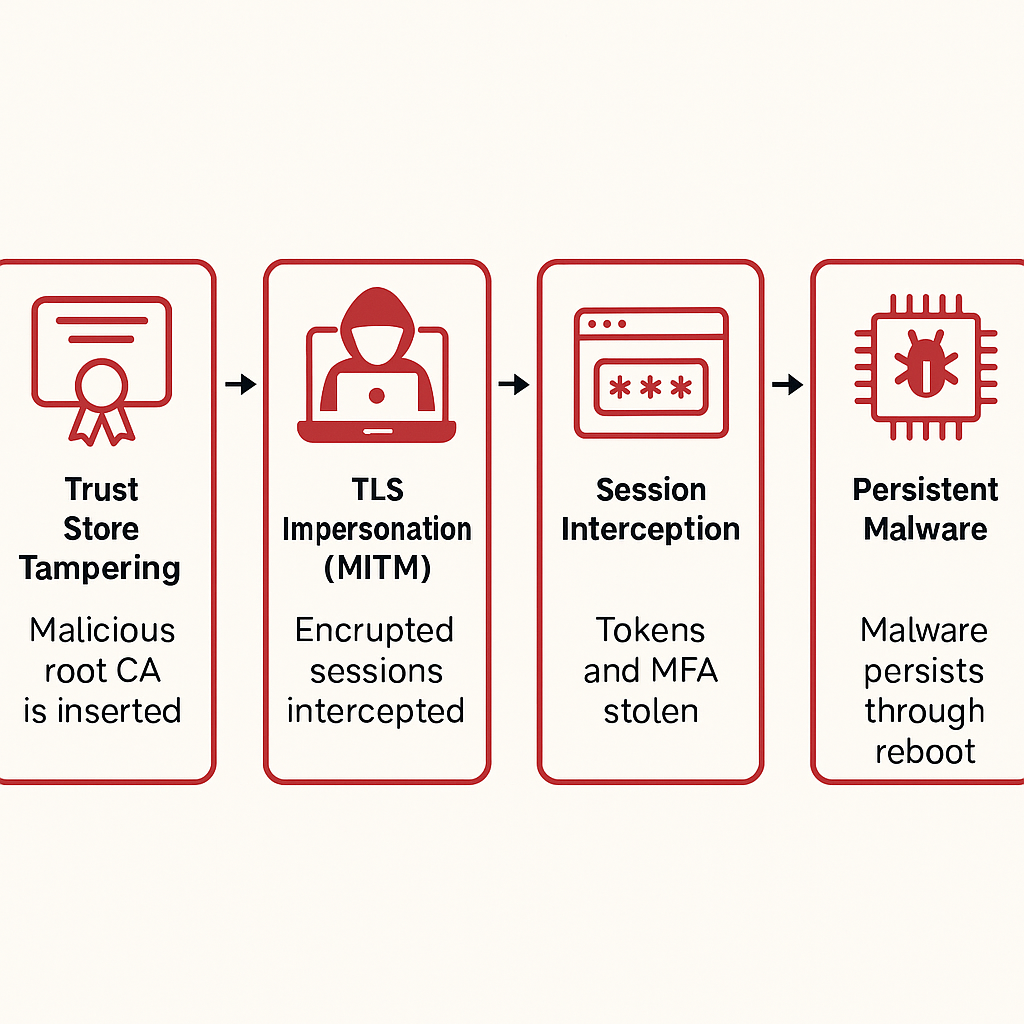


Secret Blizzard’s embassy campaign shows why device trust beats TLS trust alone—and how to harden firmware, keys, and boot chains A new expert analysis warns that...
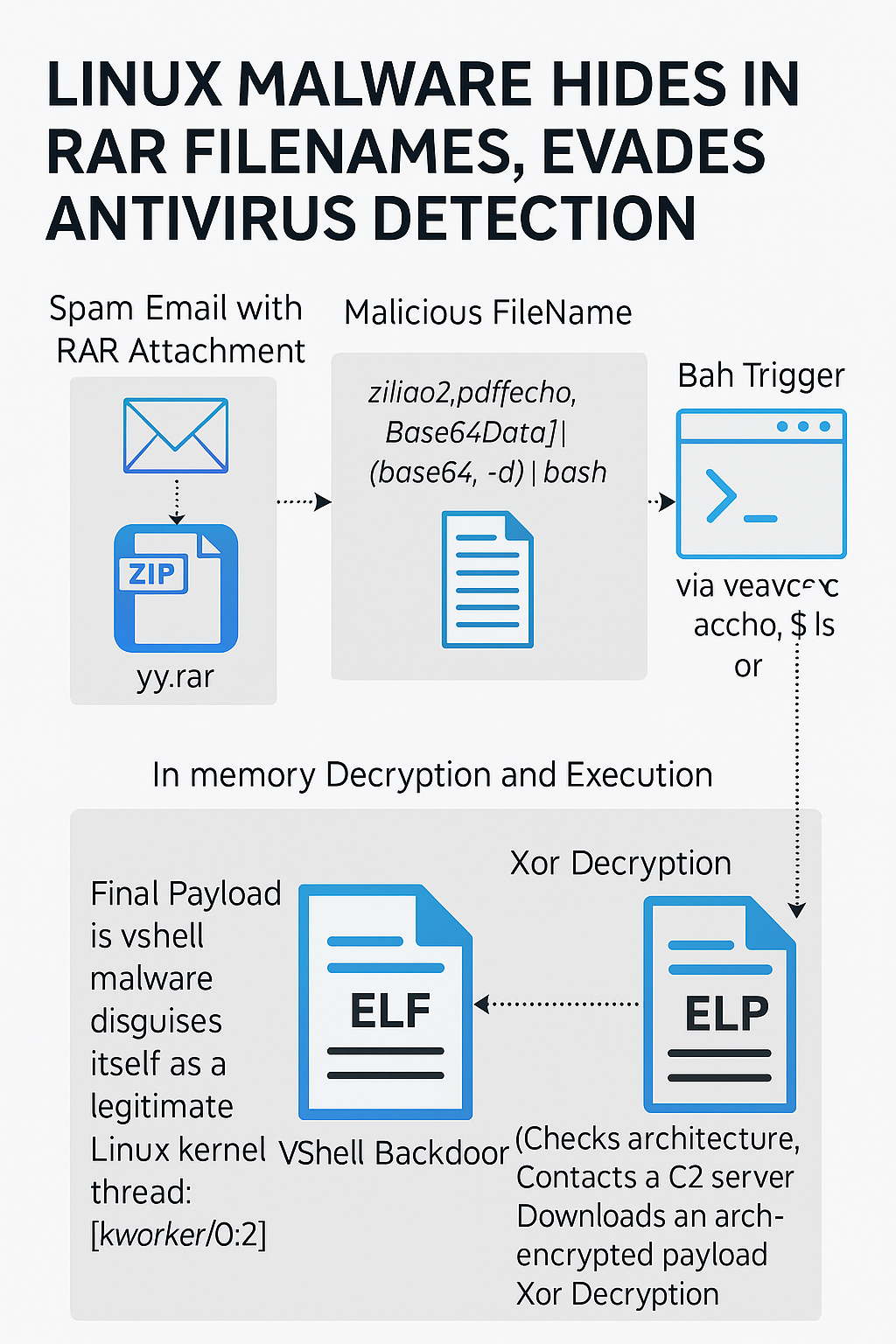


Trellix says a phishing campaign weaponizes RAR archive filenames to auto-trigger Bash, fetch a multi-arch loader, and execute the VShell backdoor entirely in memory. A new...



Threat actors abuse misconfigurations and living-off-the-land tools—using fake 404 pages and panda JPEG “polyglot” files—to drop miners on Linux and Windows at scale. Twin campaigns dubbed...



Attackers use CVE-2023-46604 to breach Linux cloud hosts, drop “DripDropper” malware, and quietly fix the flaw to lock in access, researchers say. Threat actors are abusing...


From August–September 2025, Windows 11 24H2 and Windows Server 2025 drop the legacy engine to simplify the OS and close a long-abused security gap. Microsoft will...
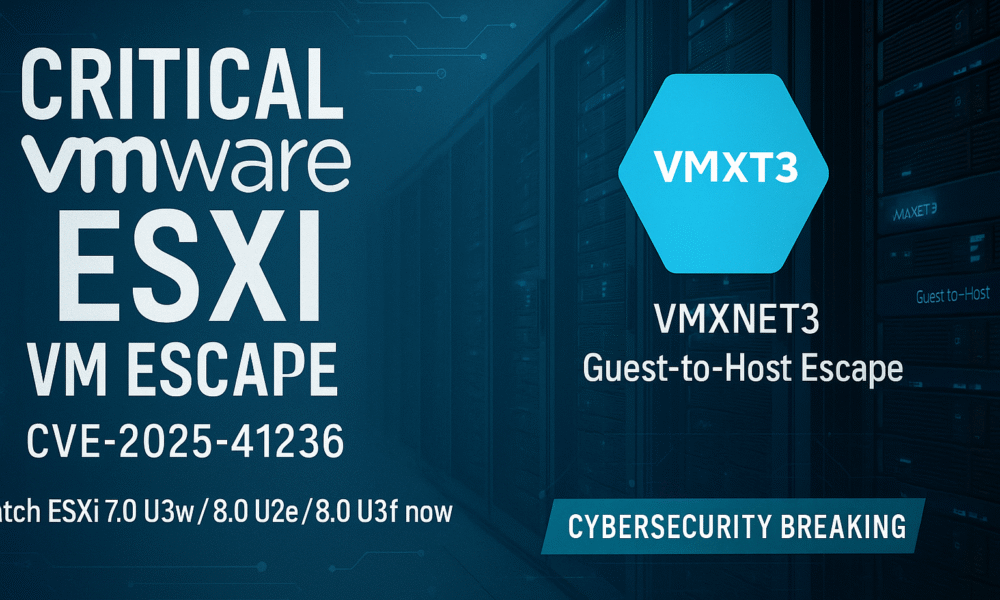

Broadcom/VMware patches CVE-2025-41236 in ESXi 7.x/8.x, but Shadowserver counts show slow remediation as thousands of internet-reachable hosts remain on vulnerable builds. A critical integer-overflow flaw (CVE-2025-41236)...



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...



Hackers Exploited Cloud Misconfiguration and API Weaknesses to Breach the Viral Red-Flag Dating App Used by Thousands of Women July 28, 2025 | MAG212NEWS In a...



New cross-platform malware strains abuse PostgreSQL, Tomcat, JupyterLab, and Confluence to hijack compute power for cryptocurrency mining—leaving cloud workloads vulnerable and detection difficult. 🧨 Introduction: Clouds...