


Contact data for ~280k email accounts and 1.7k modem passwords accessed; breach isolated to iiNet order system, company says Australia’s TPG Telecom disclosed unauthorized access to...



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...


A coordinated supply‑chain campaign dating from March 2023 has unleashed 60 rogue Ruby gems—and unknown Python packages—disguised as benign tools, siphoning credentials and crypto data, triggering...
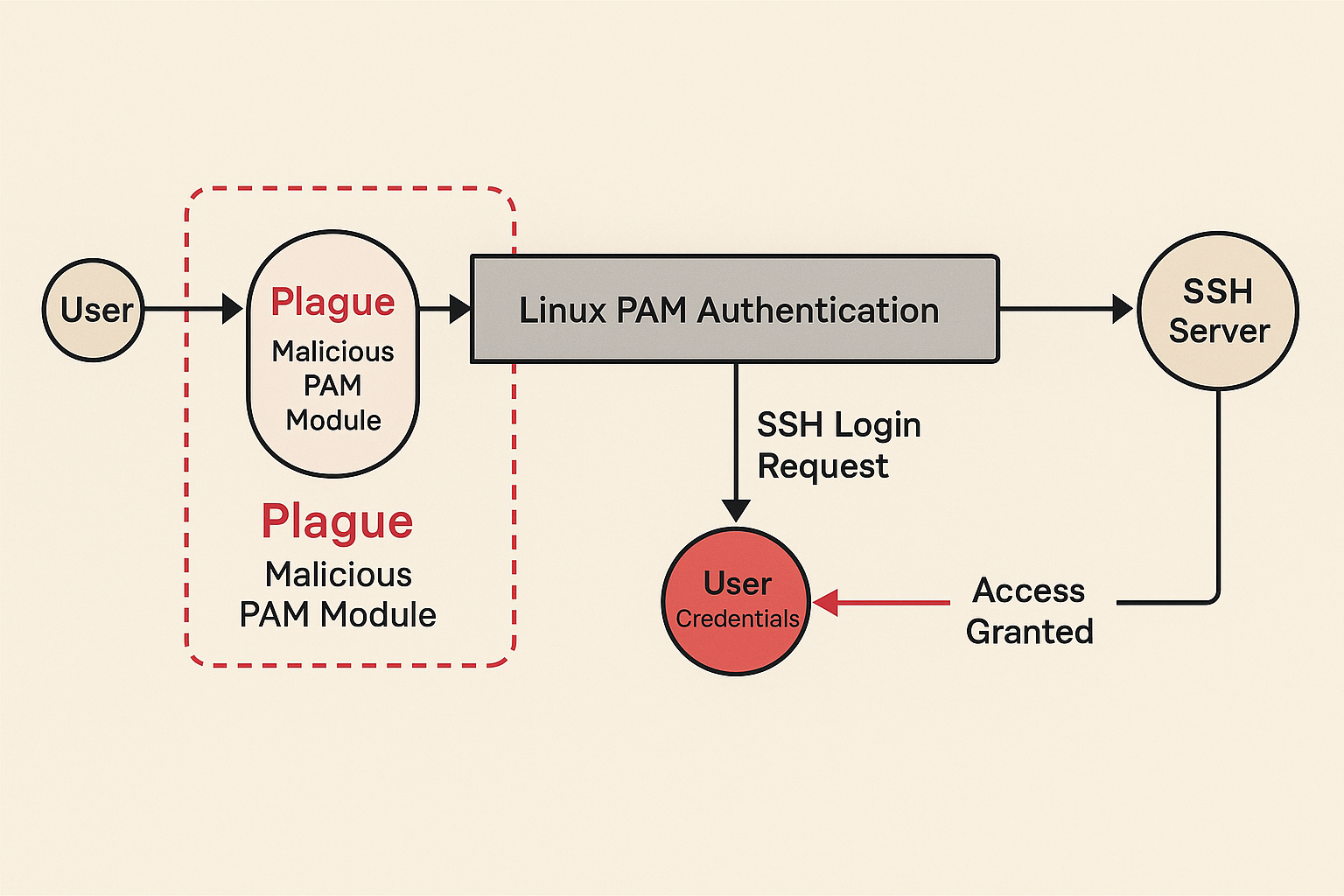


A newly discovered malicious PAM module named “Plague” stealthily hijacks SSH logins, bypasses Linux authentication, and evades antivirus—threatening enterprise servers worldwide with root-level backdoors. It didn’t...



State‑linked cyber actors leverage zero‑day vulnerabilities in on‑premises SharePoint servers to target critical infrastructure—affecting hundreds of organizations and raising alarms over national security and economic disruption....



Dissecting the internals of modern credential theft campaigns with command-line insights, evasion techniques, and real-world behavior. 🧬 Introduction In 2025, cybercriminals are no longer relying on...
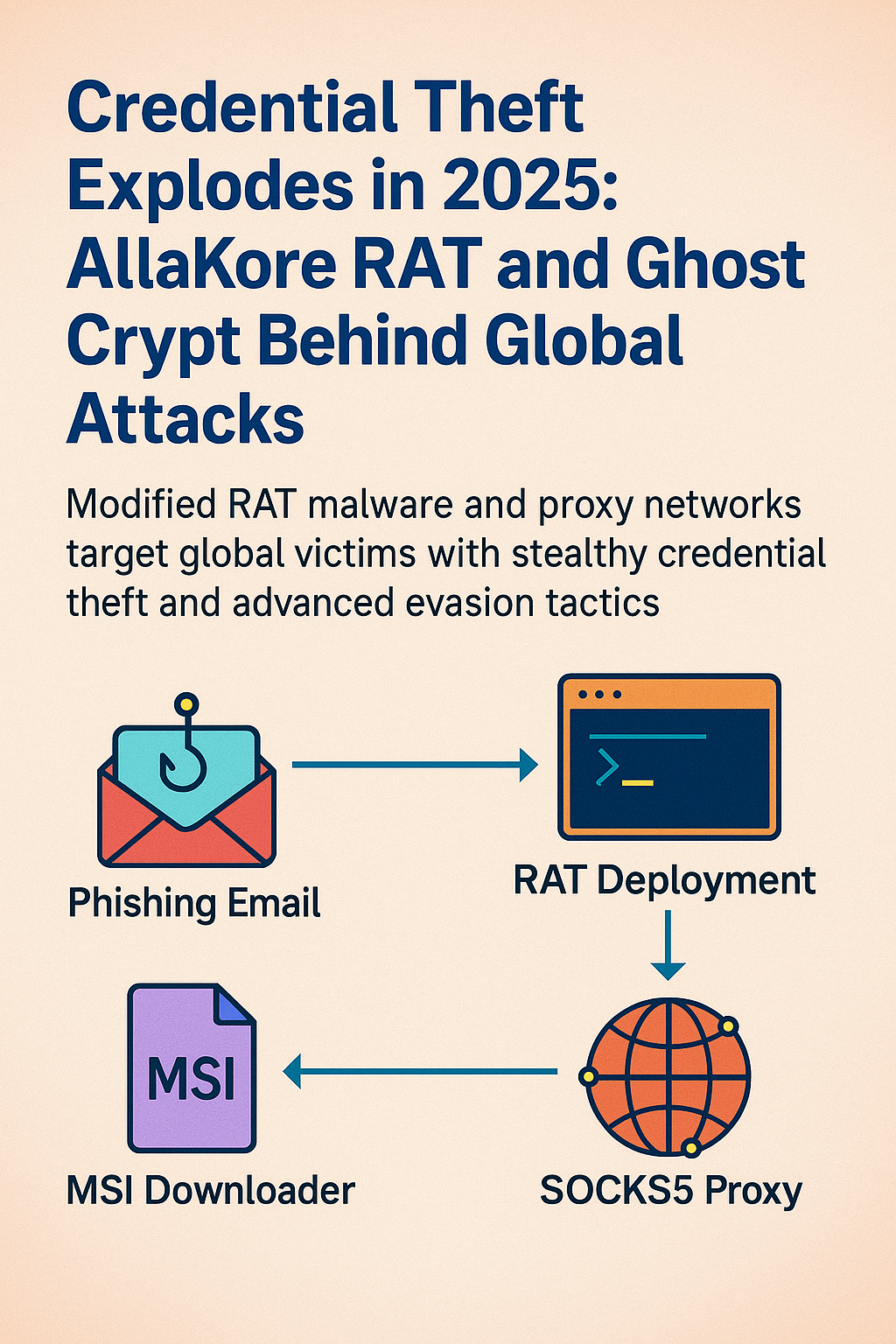


Modified RAT malware and proxy networks target global victims with stealthy credential theft and advanced evasion tactics. When María López clicked to “Update Policy,” she unwittingly...



Six widely-used NPM packages compromised with malware targeting developer environments, prompting urgent warnings for JavaScript and Node.js communities. Malware Injected into Six NPM Packages in Major...