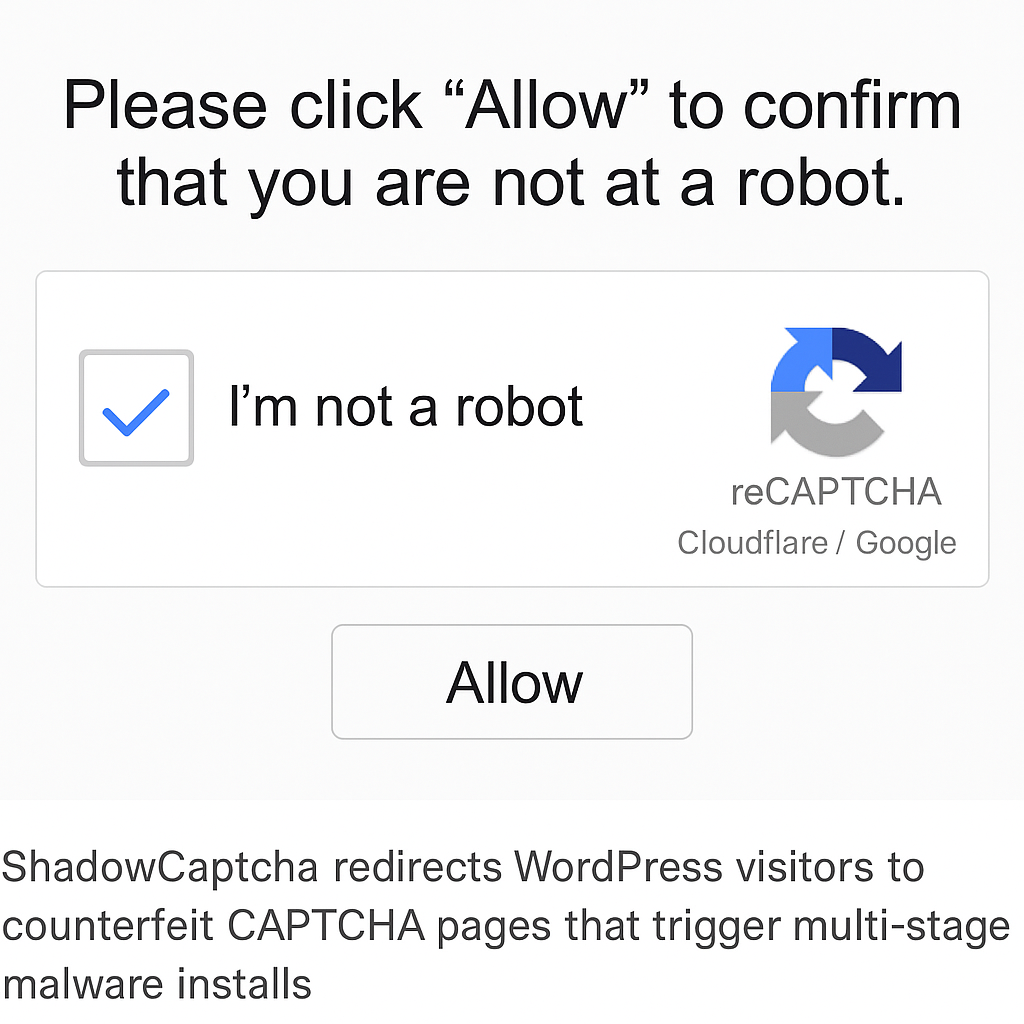


Over 100 hacked WordPress sites redirect visitors to fake Cloudflare/Google CAPTCHA pages using “ClickFix” to execute Lumma, Rhadamanthys, Epsilon Red, and XMRig payloads, researchers say. A...



Threat actors abuse misconfigurations and living-off-the-land tools—using fake 404 pages and panda JPEG “polyglot” files—to drop miners on Linux and Windows at scale. Twin campaigns dubbed...



Attackers use CVE-2023-46604 to breach Linux cloud hosts, drop “DripDropper” malware, and quietly fix the flaw to lock in access, researchers say. Threat actors are abusing...



New cross-platform malware strains abuse PostgreSQL, Tomcat, JupyterLab, and Confluence to hijack compute power for cryptocurrency mining—leaving cloud workloads vulnerable and detection difficult. 🧨 Introduction: Clouds...

The Bitcoin Layer-2 GOAT Network introduces a groundbreaking mechanism that enables users to stake Dogecoin (DOGE) and earn cryptocurrency rewards. By combining the power of Bitcoin’s...