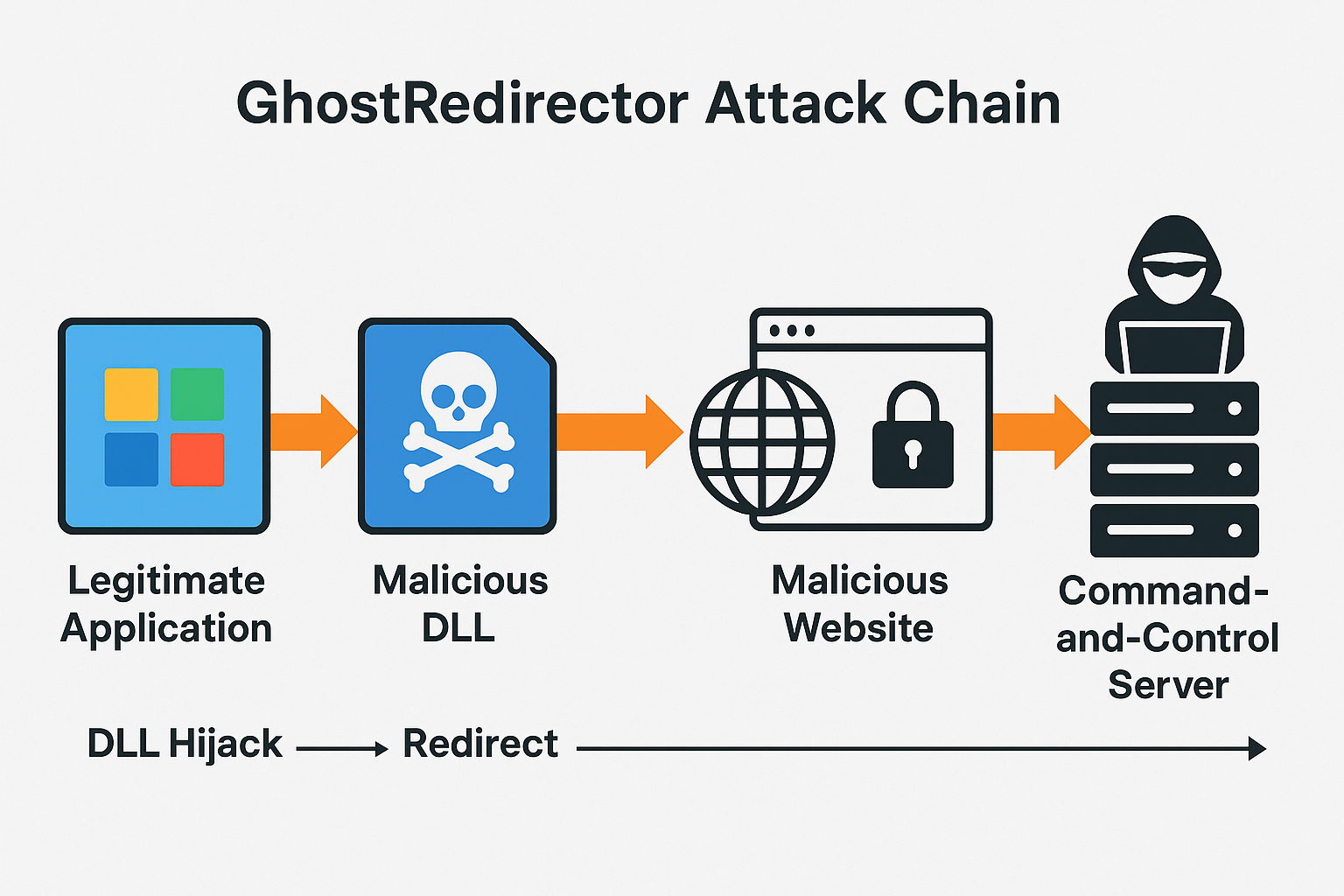


Cybercriminals abuse trusted Windows executables to redirect users, spread malware, and harvest sensitive data. A new malware campaign dubbed GhostRedirector has compromised more than 65 legitimate...
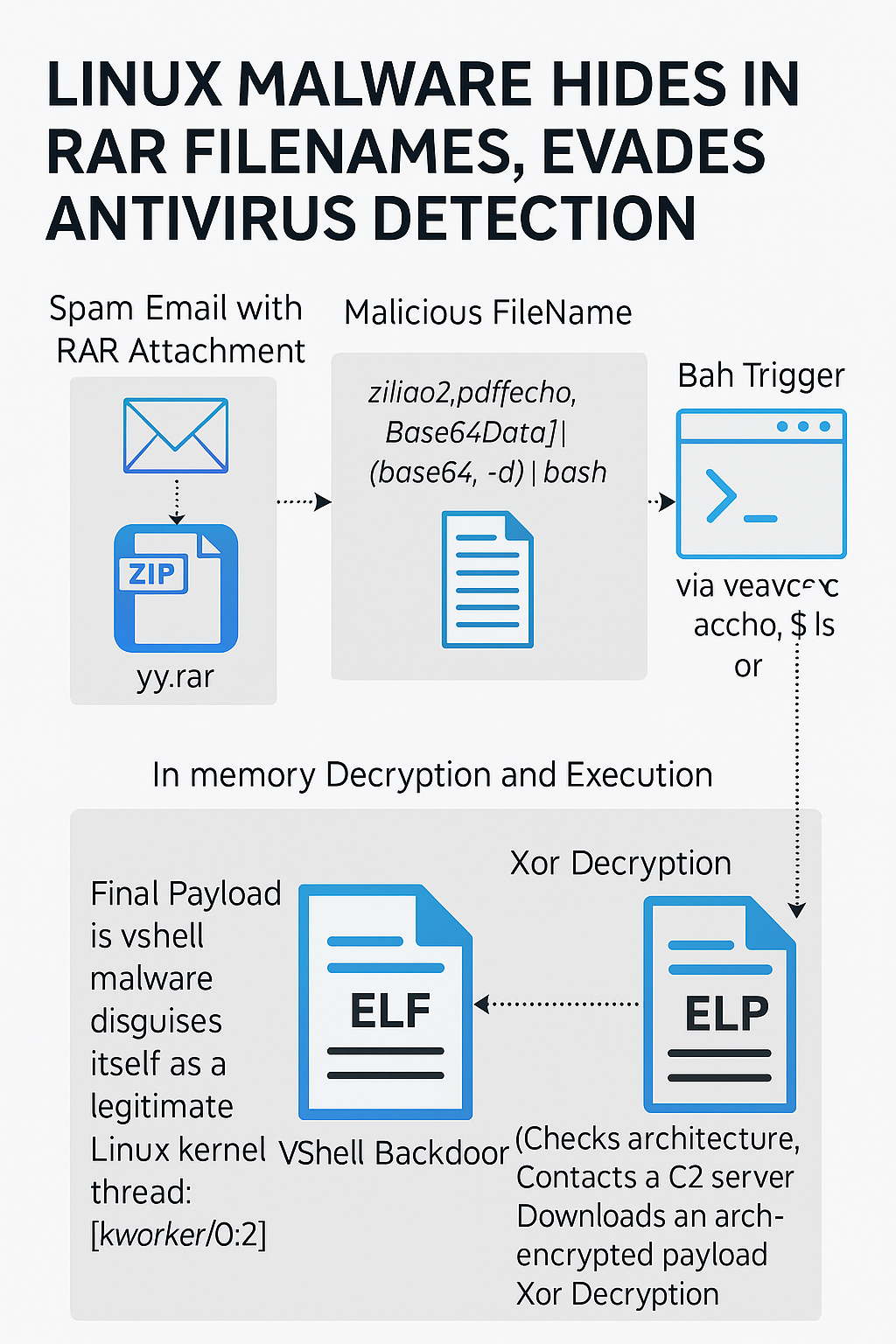


Trellix says a phishing campaign weaponizes RAR archive filenames to auto-trigger Bash, fetch a multi-arch loader, and execute the VShell backdoor entirely in memory. A new...



Contact data for ~280k email accounts and 1.7k modem passwords accessed; breach isolated to iiNet order system, company says Australia’s TPG Telecom disclosed unauthorized access to...
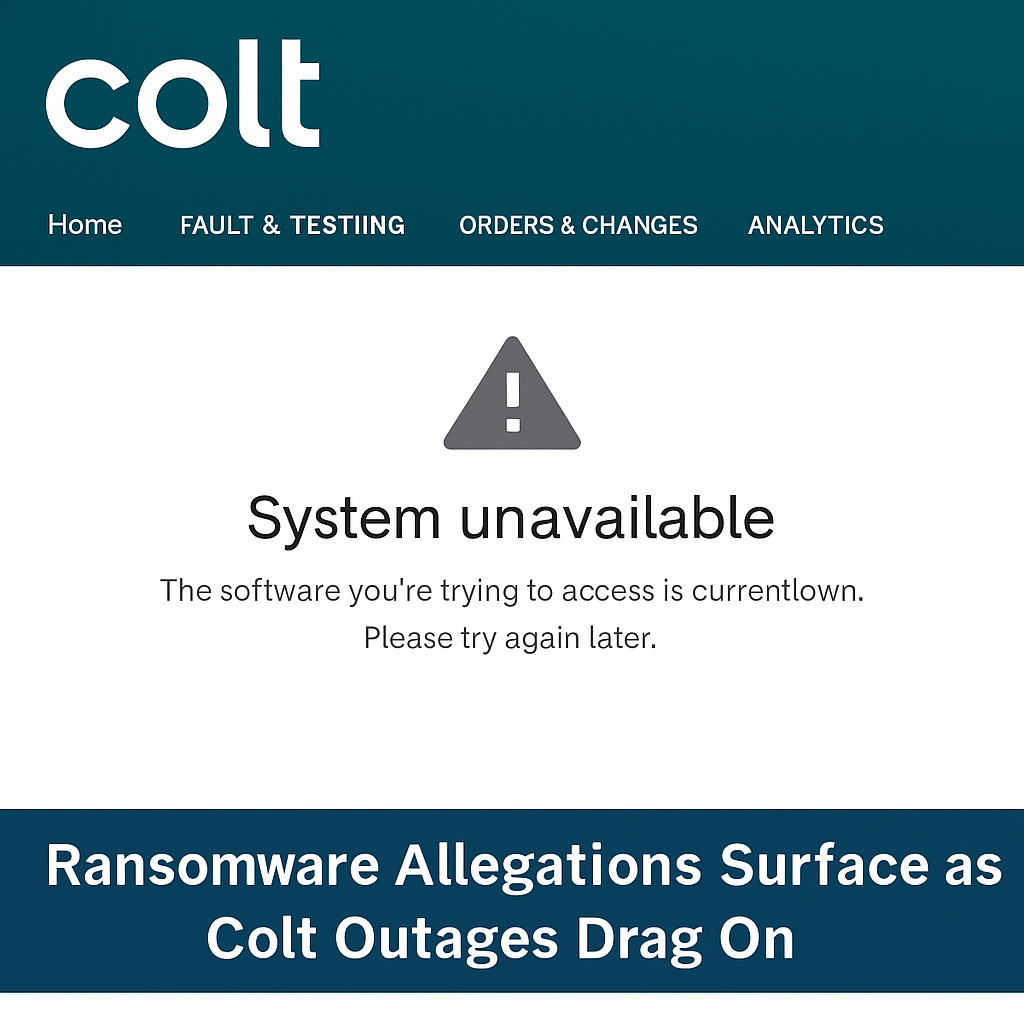


Colt Technology Services’ internal systems remain down after a suspected ransomware attack; WarLock gang claims to have stolen 1 million documents, demanding $200K ransom Colt Technology...


From August–September 2025, Windows 11 24H2 and Windows Server 2025 drop the legacy engine to simplify the OS and close a long-abused security gap. Microsoft will...

Cyber threat actors orchestrated a massive, two-wave brute-force assault on Fortinet SSL VPNs, shifting mid-campaign to FortiManager—raising alarm as such patterns often precede critical CVE disclosures....



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...



From cryptographic signing to hardened base images, a new security webinar unpacks the real-world tactics to stop supply-chain breaches targeting Python’s vast open-source ecosystem. The command...



Cybercrime syndicate UNC6040 used spoofed IT helpdesk calls and legitimate remote access tools to infiltrate corporate environments—Google TAG reveals ongoing threat to global organizations. SEO-Optimized Excerpt:Google’s...


System and Qualcomm GPU vulnerabilities allowed silent device compromise. Google’s patch blocks zero-day exploits affecting millions of Android users. Mountain View / Global – August 5,...