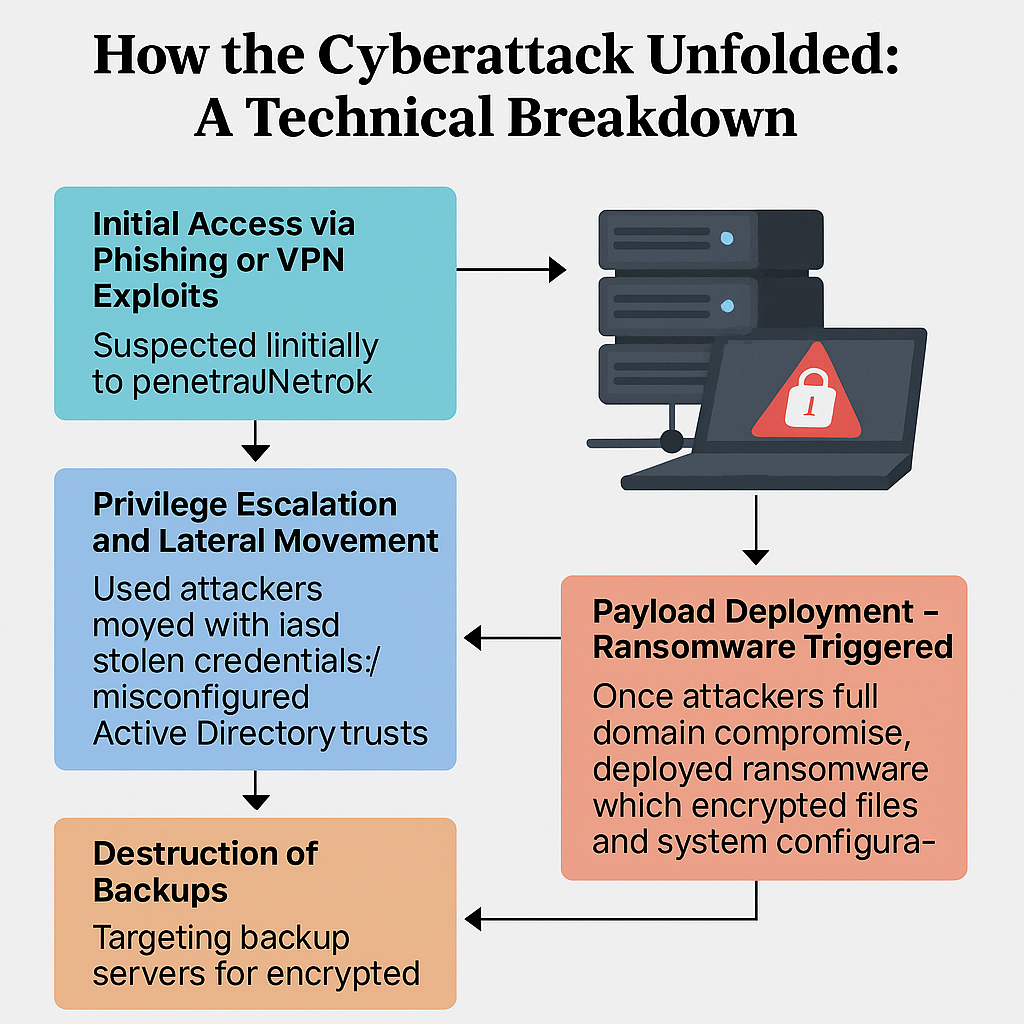


Cybercriminals cripple tax and court systems in Curaçao, Aruba, and Sint Maarten using sophisticated multi-vector ransomware; experts say outdated defenses made critical systems vulnerable. A wave...



Hackers Exploited IVR System at Georgia’s SNAP Contractor, Threatening Sensitive EBT Account Data for Thousands of Vulnerable Families ATLANTA, GEORGIA — In a chilling reminder of...
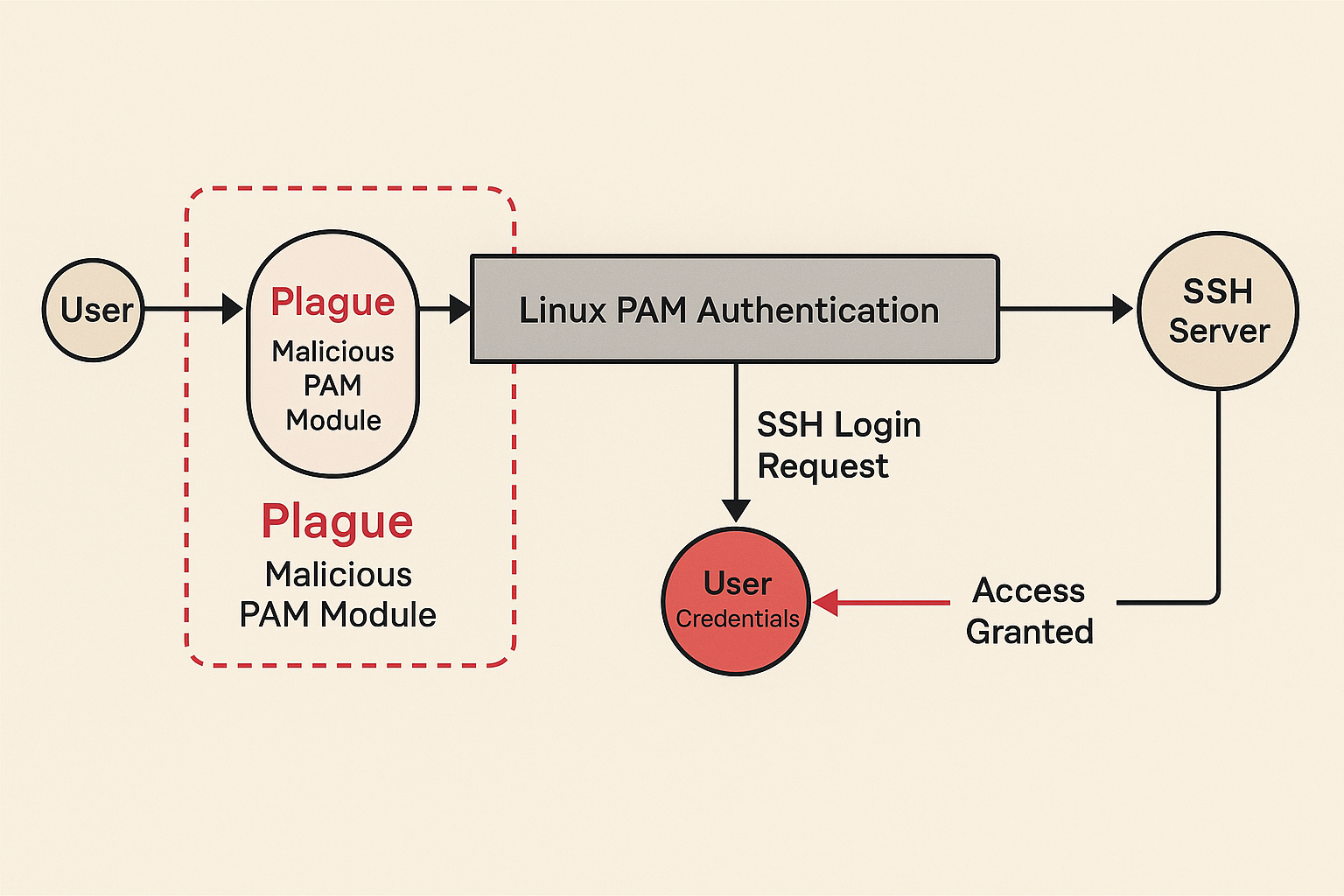


A newly discovered malicious PAM module named “Plague” stealthily hijacks SSH logins, bypasses Linux authentication, and evades antivirus—threatening enterprise servers worldwide with root-level backdoors. It didn’t...
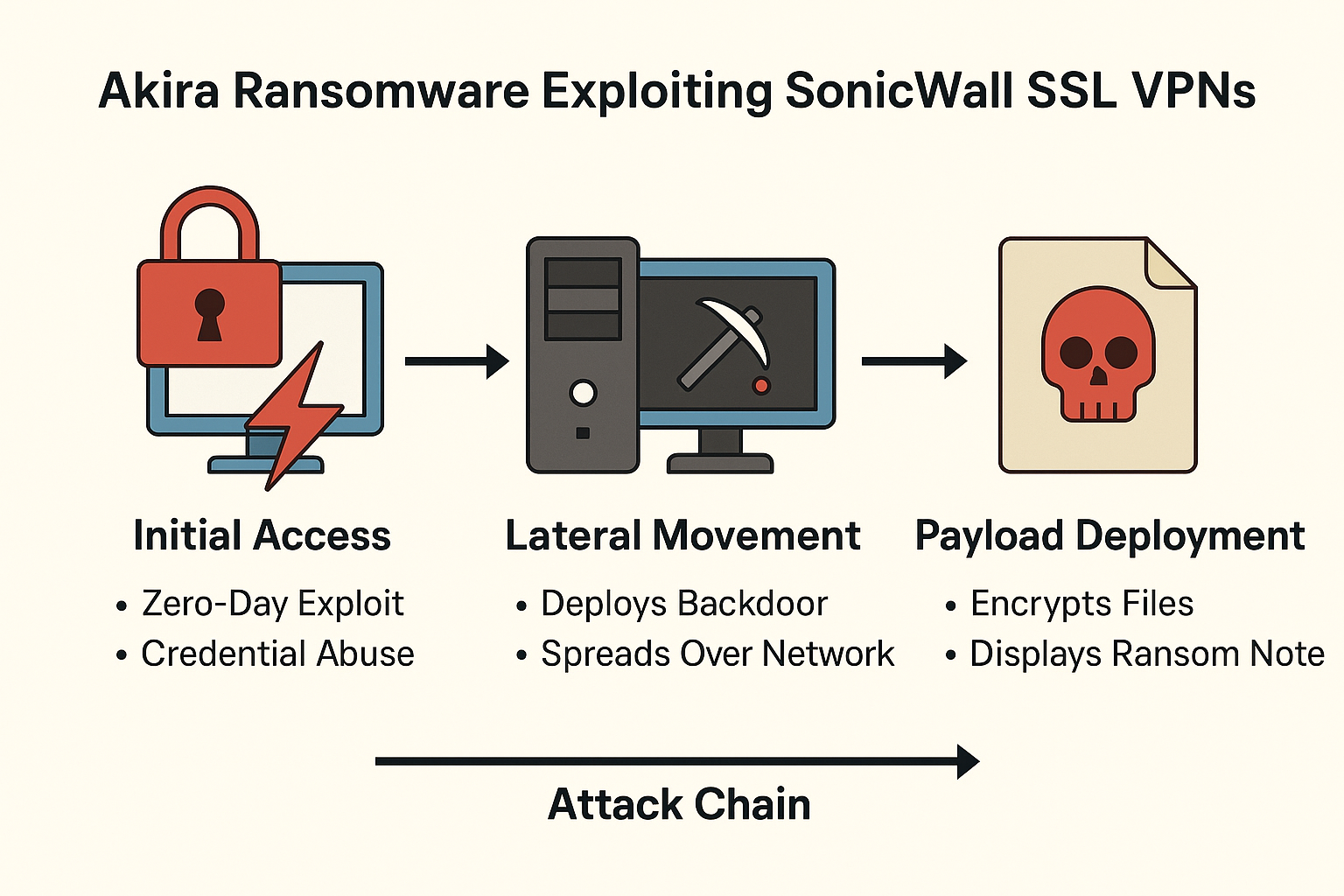


Security researchers urge immediate VPN shutdowns as Akira exploits SonicWall SSL VPN access in a sophisticated attack chain possibly involving zero-day exploits or credential compromise. BRUSSELS...
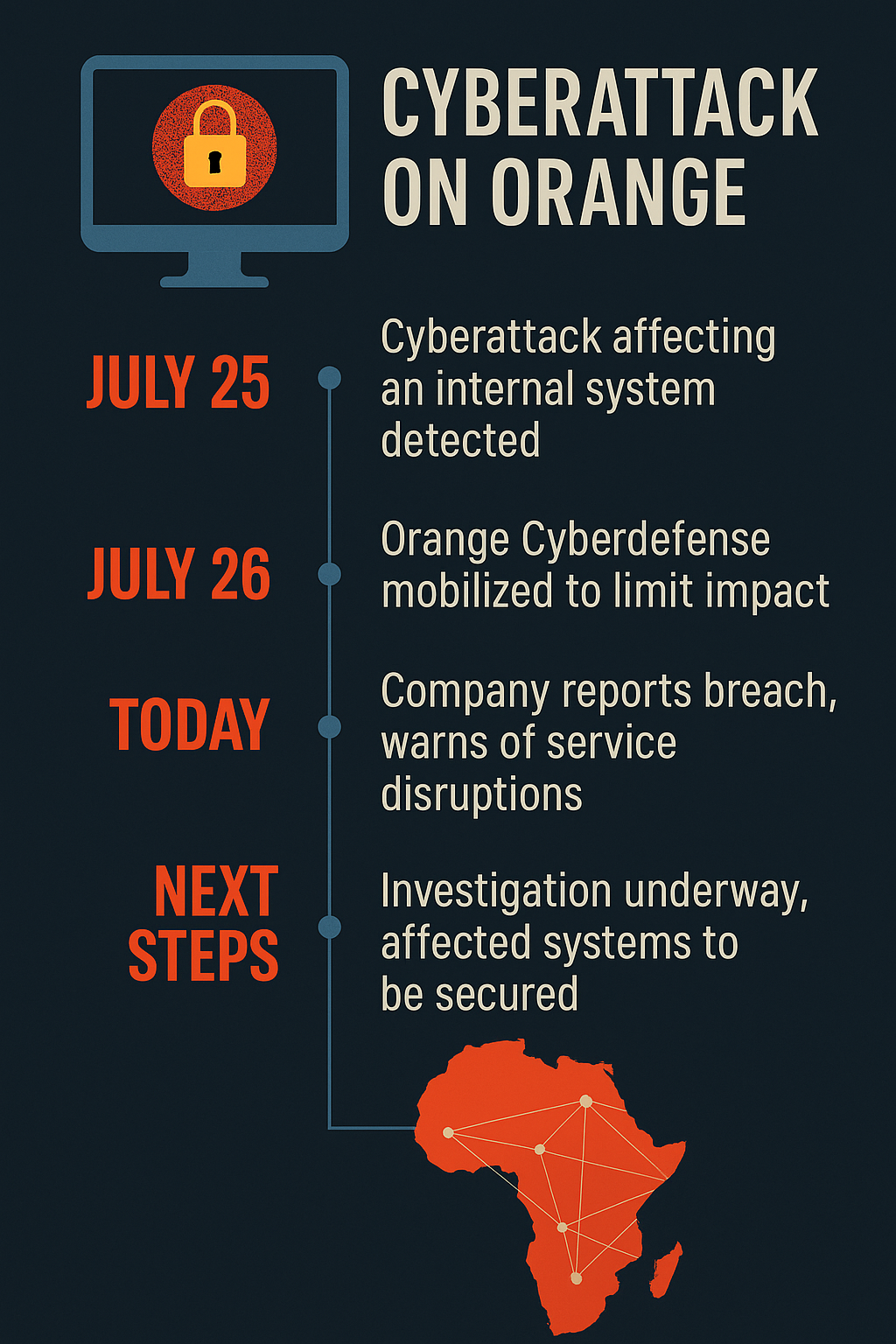


France’s largest telecom provider confirms internal system breach; customers warned of service disruptions as cybersecurity teams race to contain threat Paris — August 1, 2025In a...



State‑linked cyber actors leverage zero‑day vulnerabilities in on‑premises SharePoint servers to target critical infrastructure—affecting hundreds of organizations and raising alarms over national security and economic disruption....



New cross-platform malware strains abuse PostgreSQL, Tomcat, JupyterLab, and Confluence to hijack compute power for cryptocurrency mining—leaving cloud workloads vulnerable and detection difficult. 🧨 Introduction: Clouds...


Forensic investigations reveal how attackers exploited a SharePoint flaw using PowerShell, web shells, and lateral movement—now joined by ransomware payloads. We explain the exploit chain, with...



CISA and FBI raise red flags about a new ransomware strain crippling essential services while urging critical sectors to adopt robust defense strategies. Washington D.C. |...


Chinese-state hackers allegedly exploited a SharePoint zero-day to breach the U.S. National Nuclear Security Administration (NNSA), prompting urgent calls for patching, segmentation, and zero-trust enforcement. 🔍...