


In a precision cyber strike, Kyiv’s defense intelligence infiltrated a top-tier private ISP serving Russian security agencies—raising stakes far beyond the digital realm. When the hum...
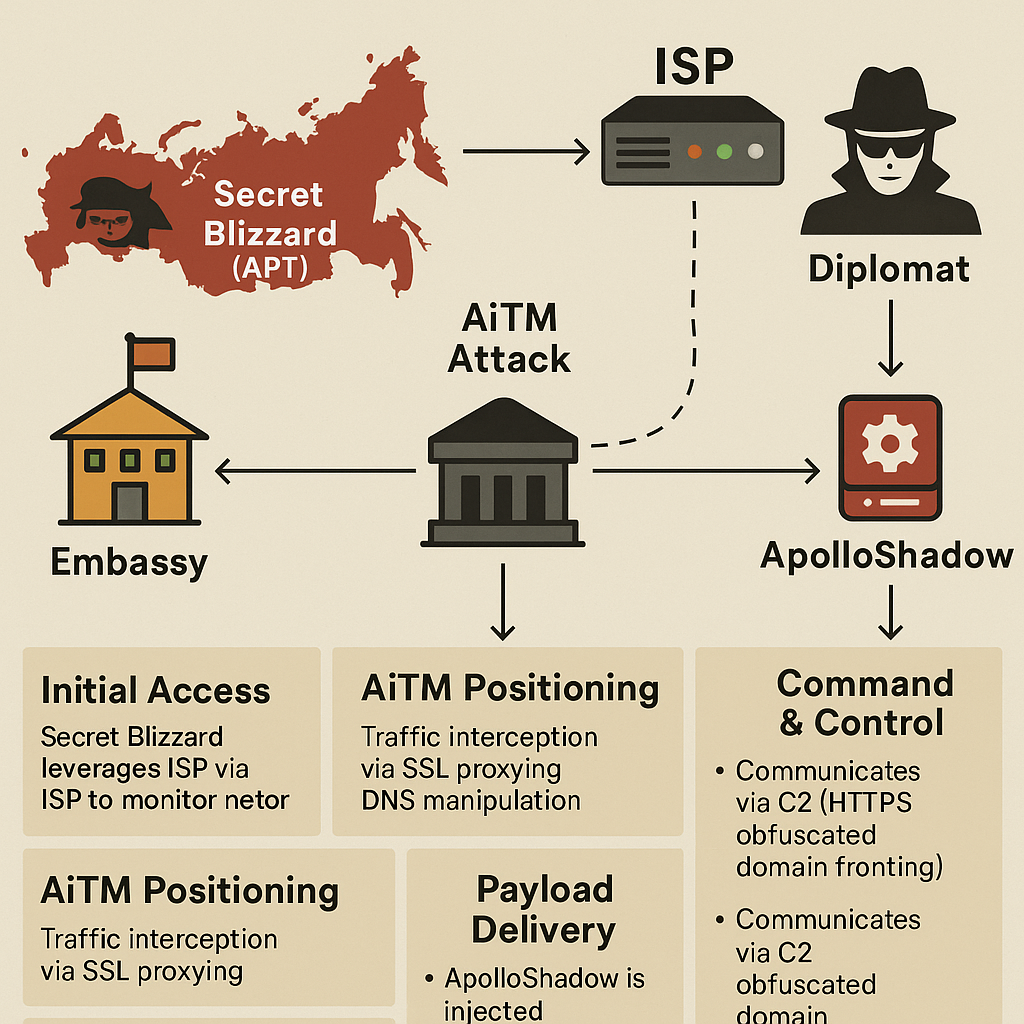


From weaponized telecom networks targeting diplomats in Moscow to AI-generated dev tools and disputed VPN exploits, 2025 is redefining the cyber threat landscape — and trust...


Chinese-state hackers allegedly exploited a SharePoint zero-day to breach the U.S. National Nuclear Security Administration (NNSA), prompting urgent calls for patching, segmentation, and zero-trust enforcement. 🔍...



Opposition party calls for accountability and nationwide protest after hacker group Jabaroot leaks CNSS records, ministerial emails, and financial contracts allegedly exposing high-level corruption. Rabat, Morocco...



Newly discovered DCHSpy malware exploits system accessibility to spy on Android users, with links to Iran’s cyber apparatus raising regional and global surveillance concerns. Iran-Linked DCHSpy...
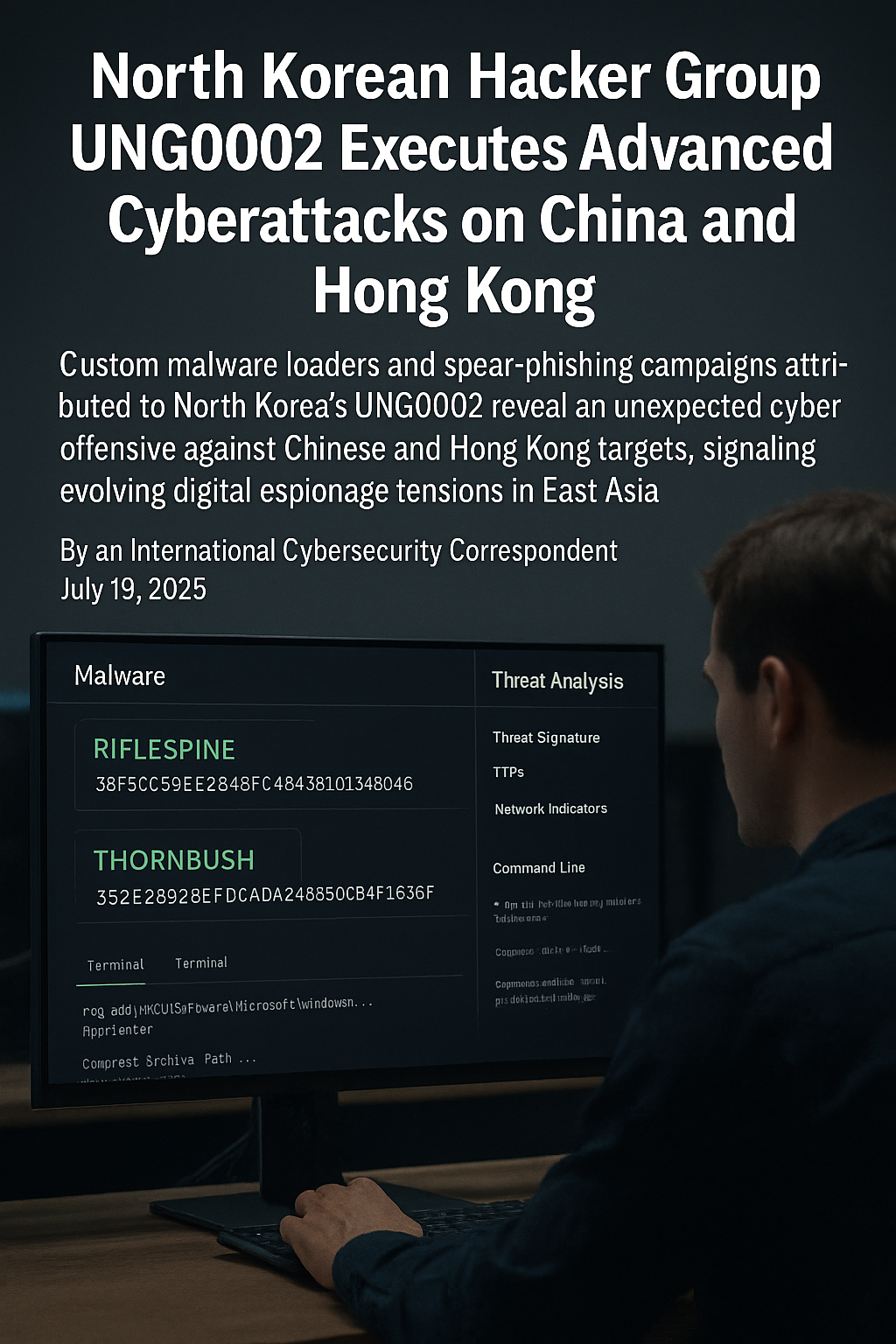


Custom malware loaders and spear-phishing campaigns attributed to North Korea’s UNG0002 reveal an unexpected cyber offensive against Chinese and Hong Kong targets, signaling evolving digital espionage...



State-backed threat actors exploit two Ivanti Connect Secure vulnerabilities to breach high-value networks, steal credentials, and drop sophisticated malware—raising alarms over critical infrastructure defense worldwide. Global...