


OpenAI’s chief, Sam Altman, warns that artificial intelligence could soon unleash an era of “information chaos,” threatening trust, truth, and global cybersecurity stability. Society Is Not...



OpenAI’s GPT-5 launch marks a turning point in artificial intelligence, promising unprecedented power and igniting fierce competition in the AI industry. GPT-5’s Game-Changing Debut “We are...



International defense contractor SOSi warns of a wave of fraudulent job offers targeting job seekers online; urges vigilance and outlines how to verify authentic recruitment communications....



From speculative chip flaws to zero-day exploits, Apple rushes to patch a series of high-risk vulnerabilities targeting billions of users worldwide. A Perfect Storm: Apple Grapples...



Medical data at risk as ransomware attack compromises DaVita’s third-party billing provider; experts warn of growing cyber threats targeting healthcare infrastructure. By El Mostafa Ouchen |...



New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...



Cybercrime syndicate UNC6040 used spoofed IT helpdesk calls and legitimate remote access tools to infiltrate corporate environments—Google TAG reveals ongoing threat to global organizations. SEO-Optimized Excerpt:Google’s...



Milford Management, owner of high-end Battery Park City properties, was duped by a single phishing email—triggering a $19 million transfer to scammers posing as the Battery...


System and Qualcomm GPU vulnerabilities allowed silent device compromise. Google’s patch blocks zero-day exploits affecting millions of Android users. Mountain View / Global – August 5,...
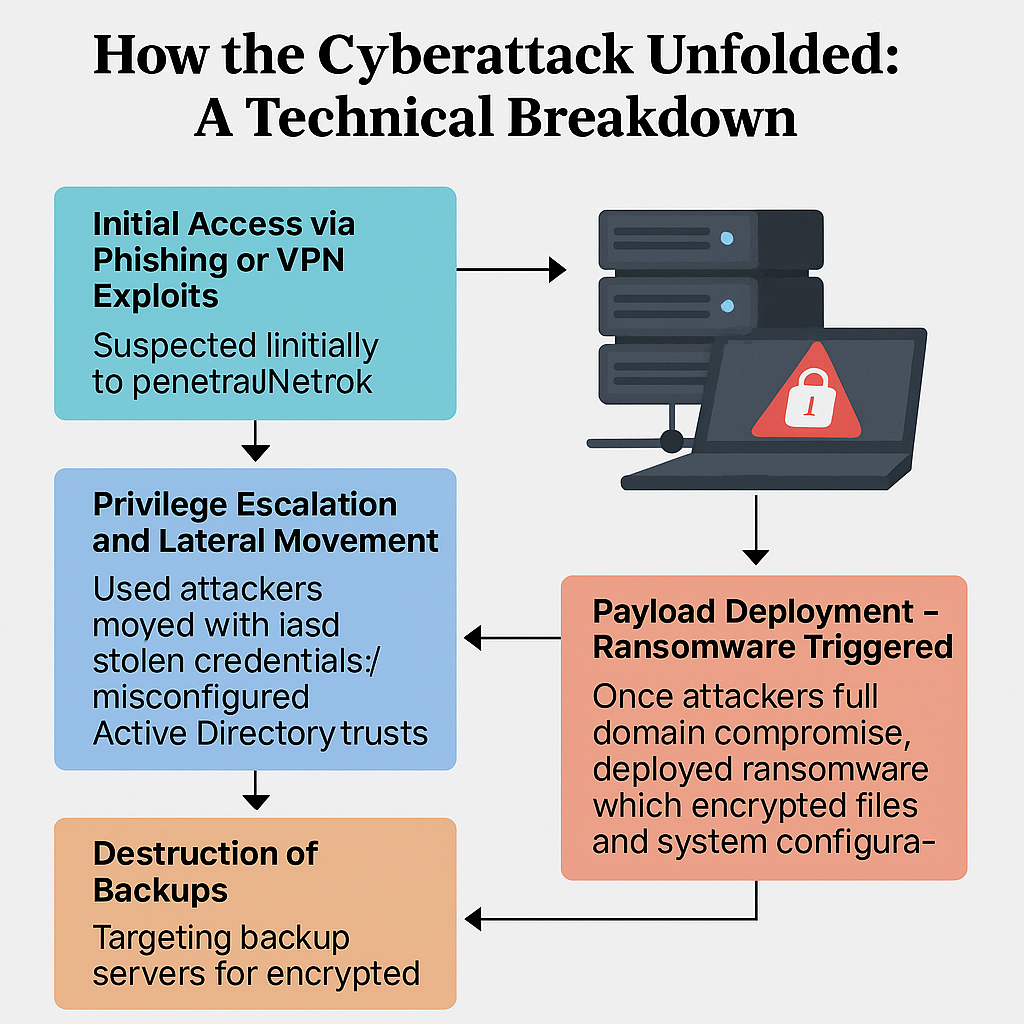


Cybercriminals cripple tax and court systems in Curaçao, Aruba, and Sint Maarten using sophisticated multi-vector ransomware; experts say outdated defenses made critical systems vulnerable. A wave...