


Threat actors abuse misconfigurations and living-off-the-land tools—using fake 404 pages and panda JPEG “polyglot” files—to drop miners on Linux and Windows at scale. Twin campaigns dubbed...



Two-day February intrusion leaked financial and medical details; group begins notifications and offers credit monitoring as regulators are alerted. The Business Council of New York State...

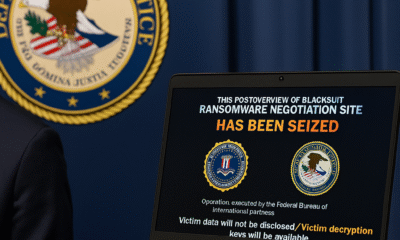

Law enforcement seized four servers, nine domains, and about $1.09M in crypto linked to the Royal/BlackSuit operation, following a July 24 takedown coordinated with eight countries....



New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...
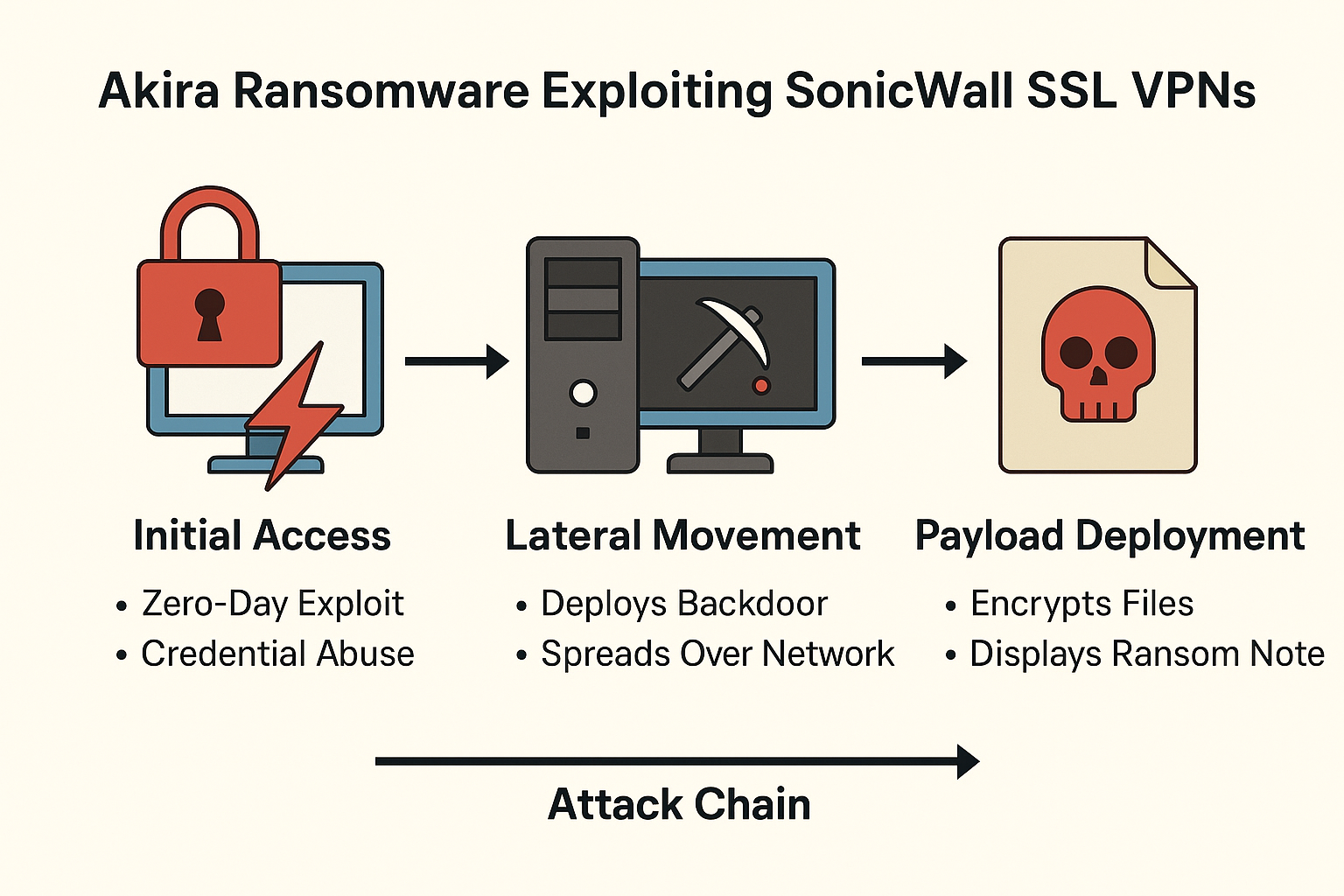


Security researchers urge immediate VPN shutdowns as Akira exploits SonicWall SSL VPN access in a sophisticated attack chain possibly involving zero-day exploits or credential compromise. BRUSSELS...