


Wiz Research finds an exposed ClickHouse database with 1M+ log lines, including chat histories and secrets—spotlighting human error, weak access controls, and the need for DLP....
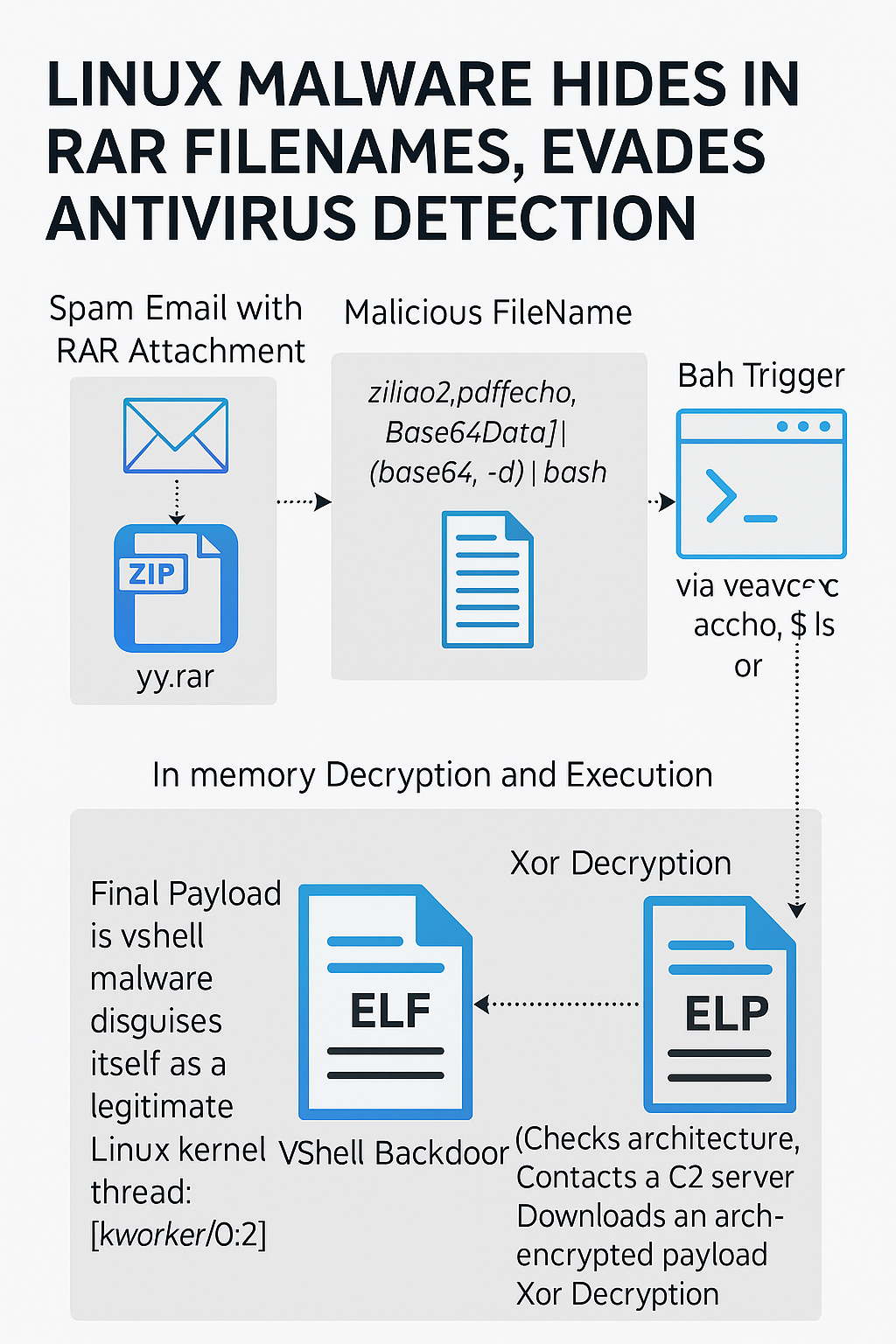


Trellix says a phishing campaign weaponizes RAR archive filenames to auto-trigger Bash, fetch a multi-arch loader, and execute the VShell backdoor entirely in memory. A new...



Threat actors abuse misconfigurations and living-off-the-land tools—using fake 404 pages and panda JPEG “polyglot” files—to drop miners on Linux and Windows at scale. Twin campaigns dubbed...



From cryptographic signing to hardened base images, a new security webinar unpacks the real-world tactics to stop supply-chain breaches targeting Python’s vast open-source ecosystem. The command...


A coordinated supply‑chain campaign dating from March 2023 has unleashed 60 rogue Ruby gems—and unknown Python packages—disguised as benign tools, siphoning credentials and crypto data, triggering...



New cross-platform malware strains abuse PostgreSQL, Tomcat, JupyterLab, and Confluence to hijack compute power for cryptocurrency mining—leaving cloud workloads vulnerable and detection difficult. 🧨 Introduction: Clouds...



Six widely-used NPM packages compromised with malware targeting developer environments, prompting urgent warnings for JavaScript and Node.js communities. Malware Injected into Six NPM Packages in Major...