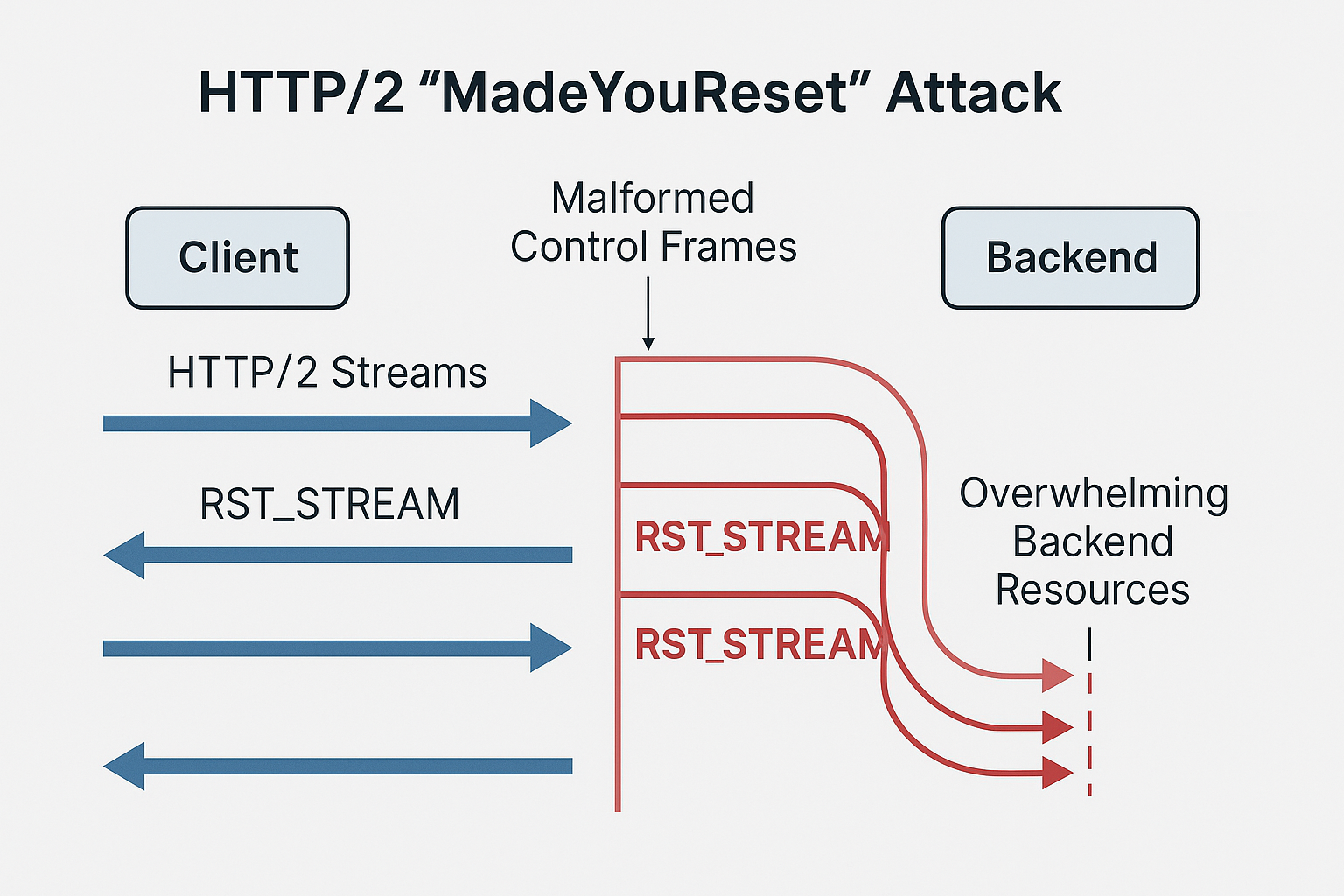


New CVE-2025-8671 technique bypasses Rapid Reset defenses; patches rolling out for Tomcat, Netty, F5 as vendors coordinate with CERT/CC. A newly disclosed HTTP/2 vulnerability dubbed “MadeYouReset”...



Incident forces suspension of 80 UK funds as forensic investigation and system restoration efforts intensify. France-based FinTech firm Linedata has suffered a cyberattack that encrypted data...


Law enforcement seized four servers, nine domains, and about $1.09M in crypto linked to the Royal/BlackSuit operation, following a July 24 takedown coordinated with eight countries....



From potatoes to paleontology, Morocco posts gains across economy, science, and sport, while DV-2025 visa delays put pressure on applicants. Morocco’s potato exports surged after a...

Broadcom/VMware patches CVE-2025-41236 in ESXi 7.x/8.x, but Shadowserver counts show slow remediation as thousands of internet-reachable hosts remain on vulnerable builds. A critical integer-overflow flaw (CVE-2025-41236)...

August cumulative update KB5063877 for Windows Server 2019 resolves a July patch flaw that crashed Cluster service and forced repeated VM reboots—especially on BitLocker-protected CSVs. Microsoft...


HHS OCR’s updated FAQs clarify disclosures to value-based care groups and what must be released under the “designated record set,” aligning with CMS’s new interoperability push....



Phone, email, and website went dark as investigators probe links to widely exploited Citrix NetScaler flaws. The Pennsylvania Attorney General’s Office says a cyberattack disabled its...
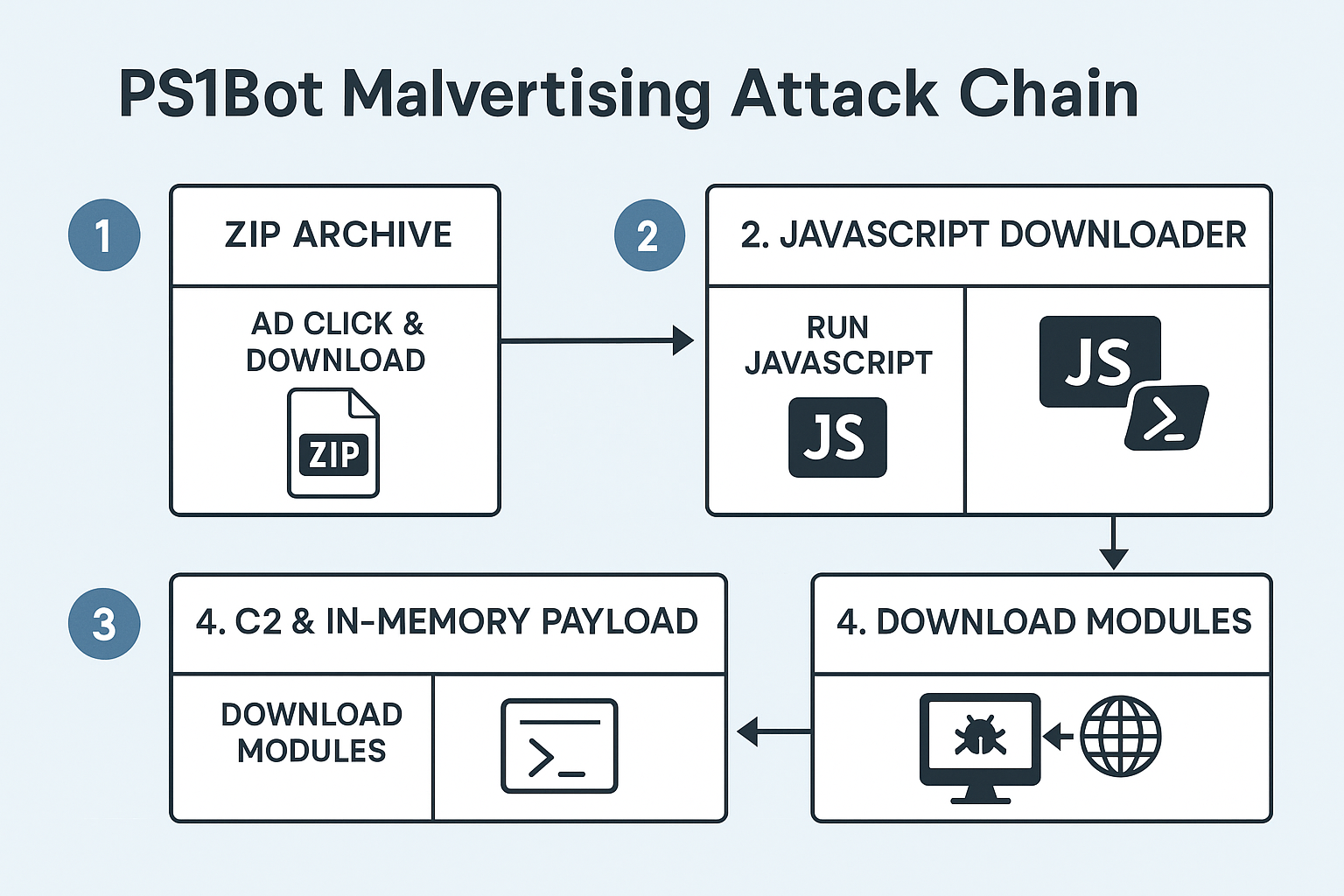


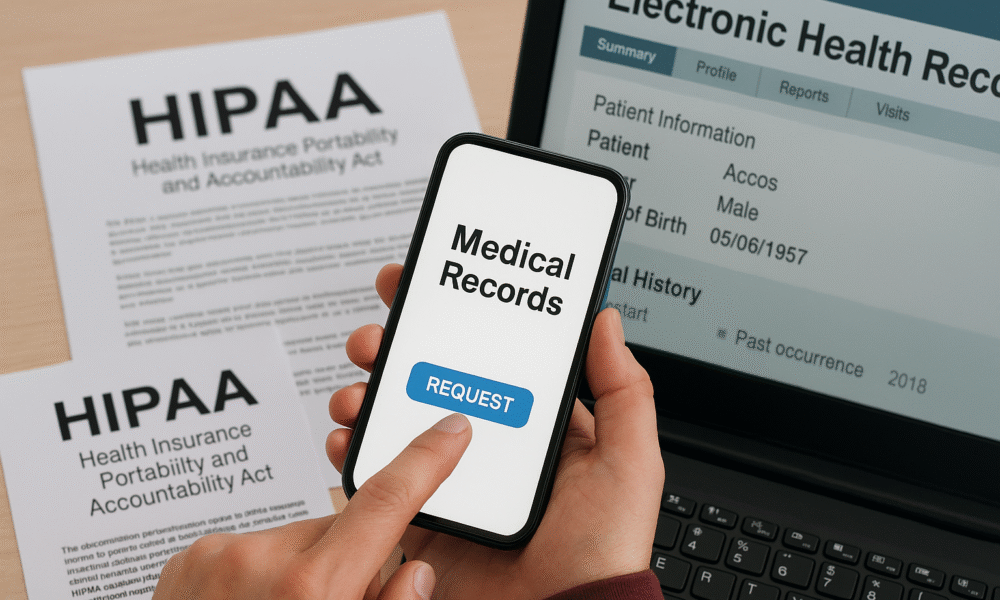
Cisco Talos warns of a modular PowerShell/C# threat stealing wallets, logging keystrokes, and persisting without writing payloads to disk. A new malvertising campaign is delivering PS1Bot,...

Hackers claim “full system compromise,” say all servers were encrypted and backups wiped; company has not confirmed the incident as investigators assess potential operational impact Royal...