


Multiple high-severity vulnerabilities in NVIDIA’s Triton Inference Server could allow unauthenticated attackers to execute remote code, compromise AI models, and disrupt production environments. NVIDIA Triton AI...
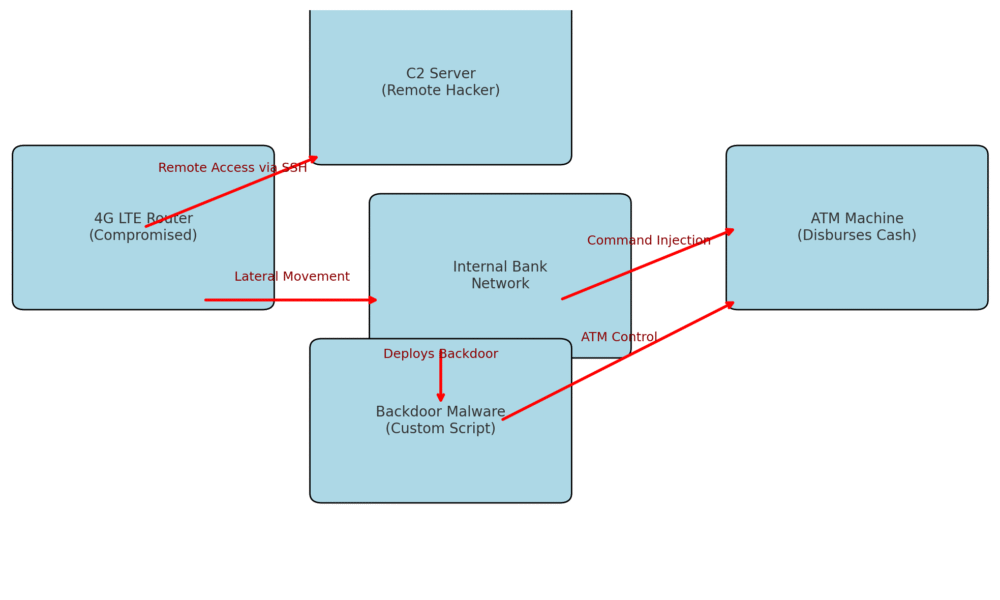

Mandiant links financially motivated hackers to ATM jackpotting campaign by exploiting 4G LTE router vulnerabilities at banking institutions. UNC2891 Orchestrates Sophisticated ATM Breach via Mobile Routers...
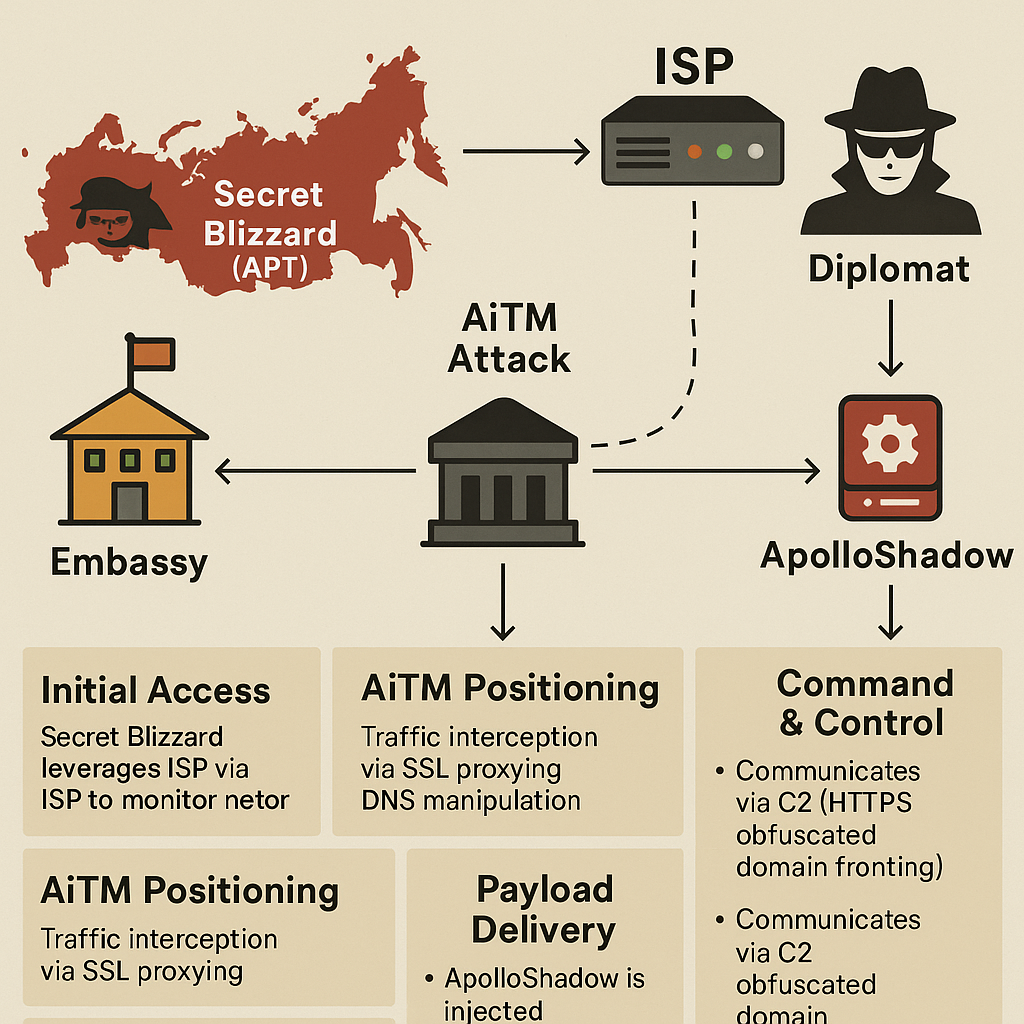


From weaponized telecom networks targeting diplomats in Moscow to AI-generated dev tools and disputed VPN exploits, 2025 is redefining the cyber threat landscape — and trust...



Hackers Exploited IVR System at Georgia’s SNAP Contractor, Threatening Sensitive EBT Account Data for Thousands of Vulnerable Families ATLANTA, GEORGIA — In a chilling reminder of...
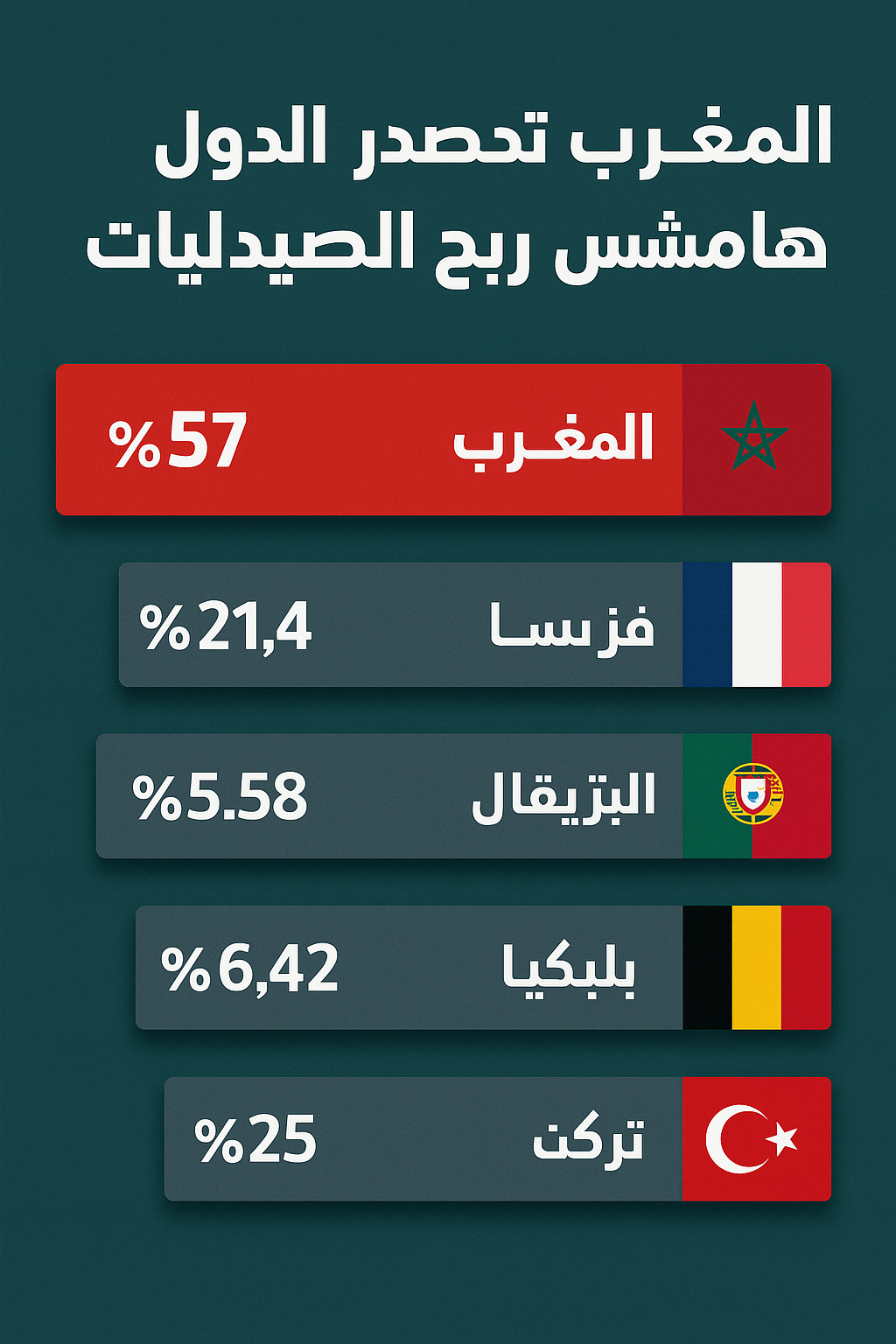


A recent report by Morocco’s Supreme Audit Council reveals that pharmacy profit margins in the Kingdom reach up to 57%—far exceeding those in France, Portugal, Belgium,...
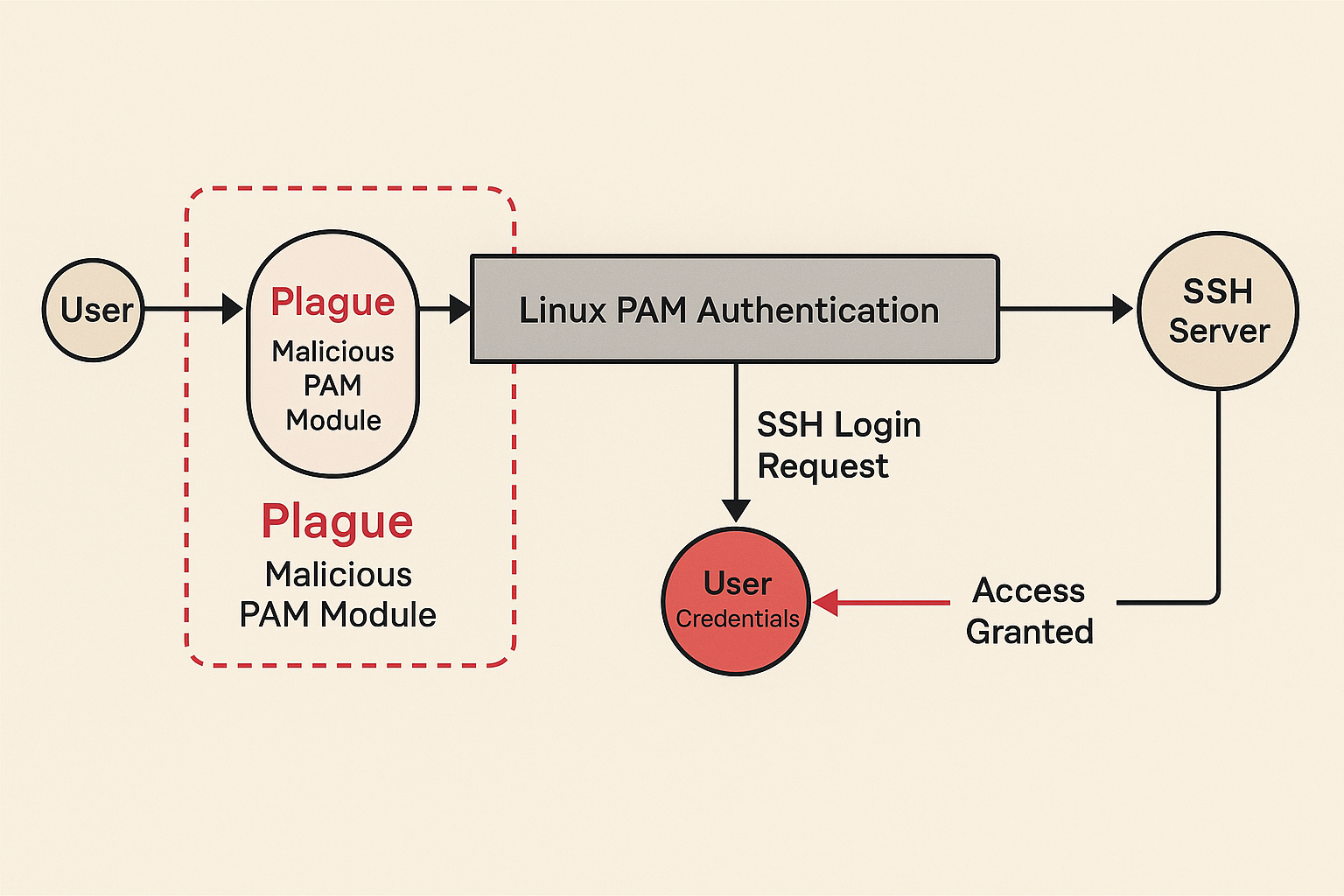


A newly discovered malicious PAM module named “Plague” stealthily hijacks SSH logins, bypasses Linux authentication, and evades antivirus—threatening enterprise servers worldwide with root-level backdoors. It didn’t...
In a powerful tribute, President Donald Trump reiterates U.S. support for Morocco’s territorial integrity and highlights the kingdom’s role as a cornerstone of regional stability and...
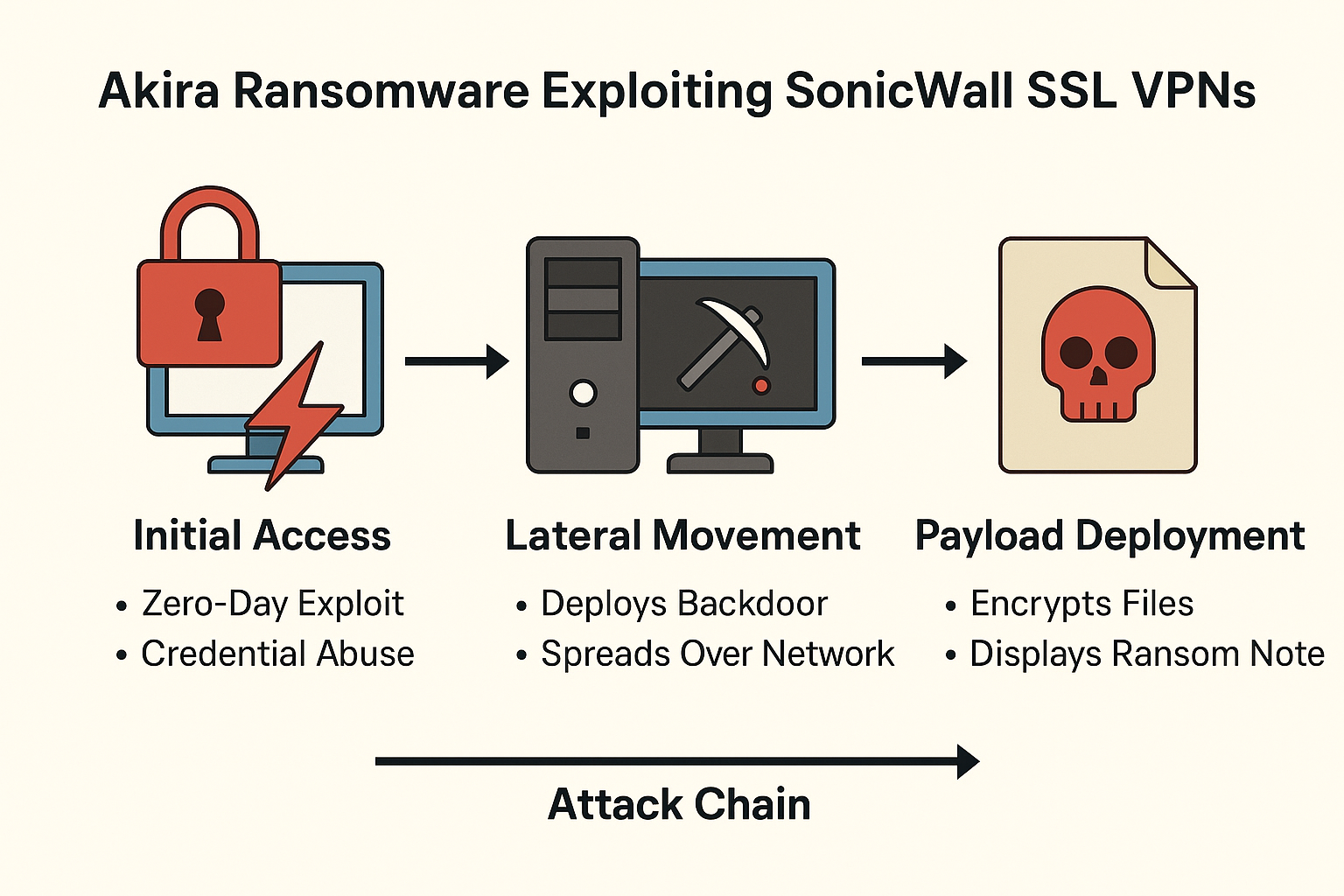


Security researchers urge immediate VPN shutdowns as Akira exploits SonicWall SSL VPN access in a sophisticated attack chain possibly involving zero-day exploits or credential compromise. BRUSSELS...



Hackers claim to have stolen terabytes of sensitive data from Dollar Tree; confusion arises as company links incident to 99 Cents Only Stores’ systems it acquired...
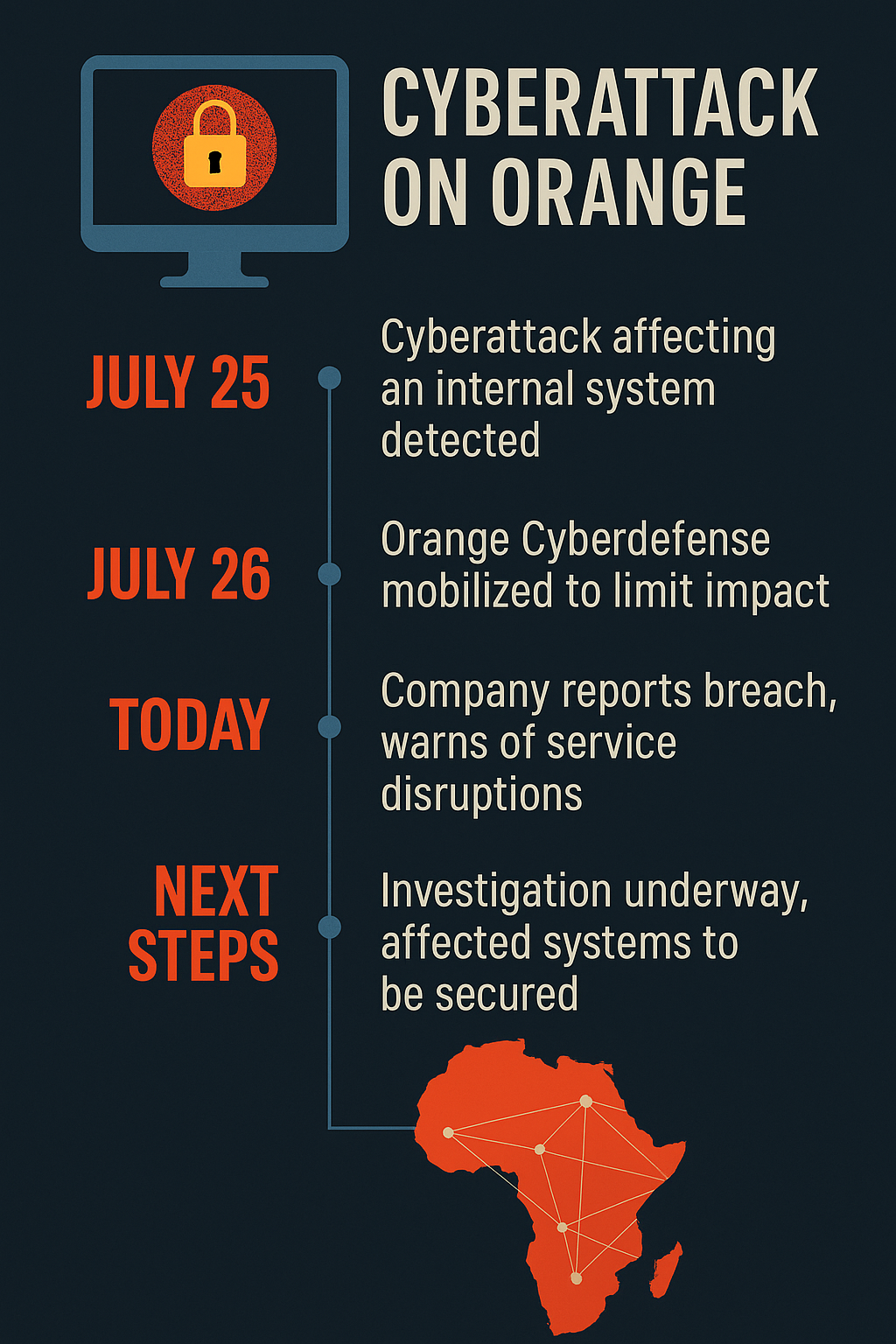


France’s largest telecom provider confirms internal system breach; customers warned of service disruptions as cybersecurity teams race to contain threat Paris — August 1, 2025In a...