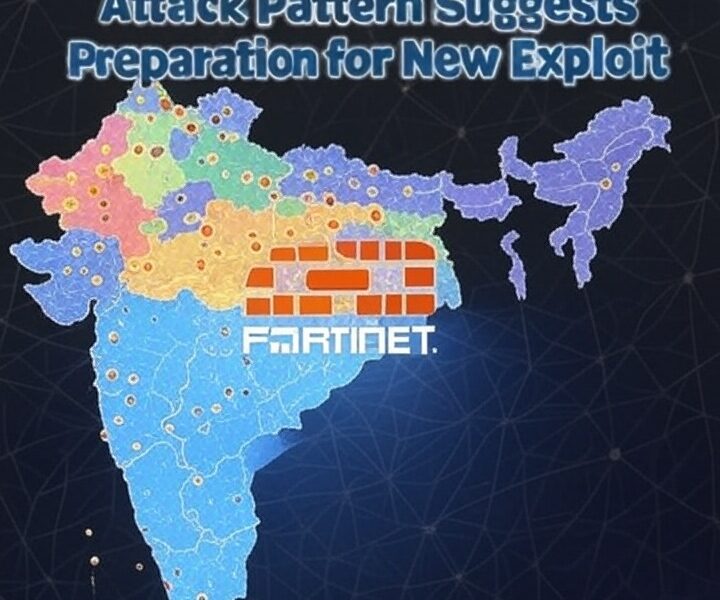

Cyber threat actors orchestrated a massive, two-wave brute-force assault on Fortinet SSL VPNs, shifting mid-campaign to FortiManager—raising alarm as such patterns often precede critical CVE disclosures....



Morocco’s Directorate General of Information Systems Security (DGSSI) issues a dire warning: a zero-day vulnerability in WinRAR is being actively exploited, putting countless users at risk...



New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...



Cybercrime syndicate UNC6040 used spoofed IT helpdesk calls and legitimate remote access tools to infiltrate corporate environments—Google TAG reveals ongoing threat to global organizations. SEO-Optimized Excerpt:Google’s...


System and Qualcomm GPU vulnerabilities allowed silent device compromise. Google’s patch blocks zero-day exploits affecting millions of Android users. Mountain View / Global – August 5,...



Hackers claim to have stolen terabytes of sensitive data from Dollar Tree; confusion arises as company links incident to 99 Cents Only Stores’ systems it acquired...
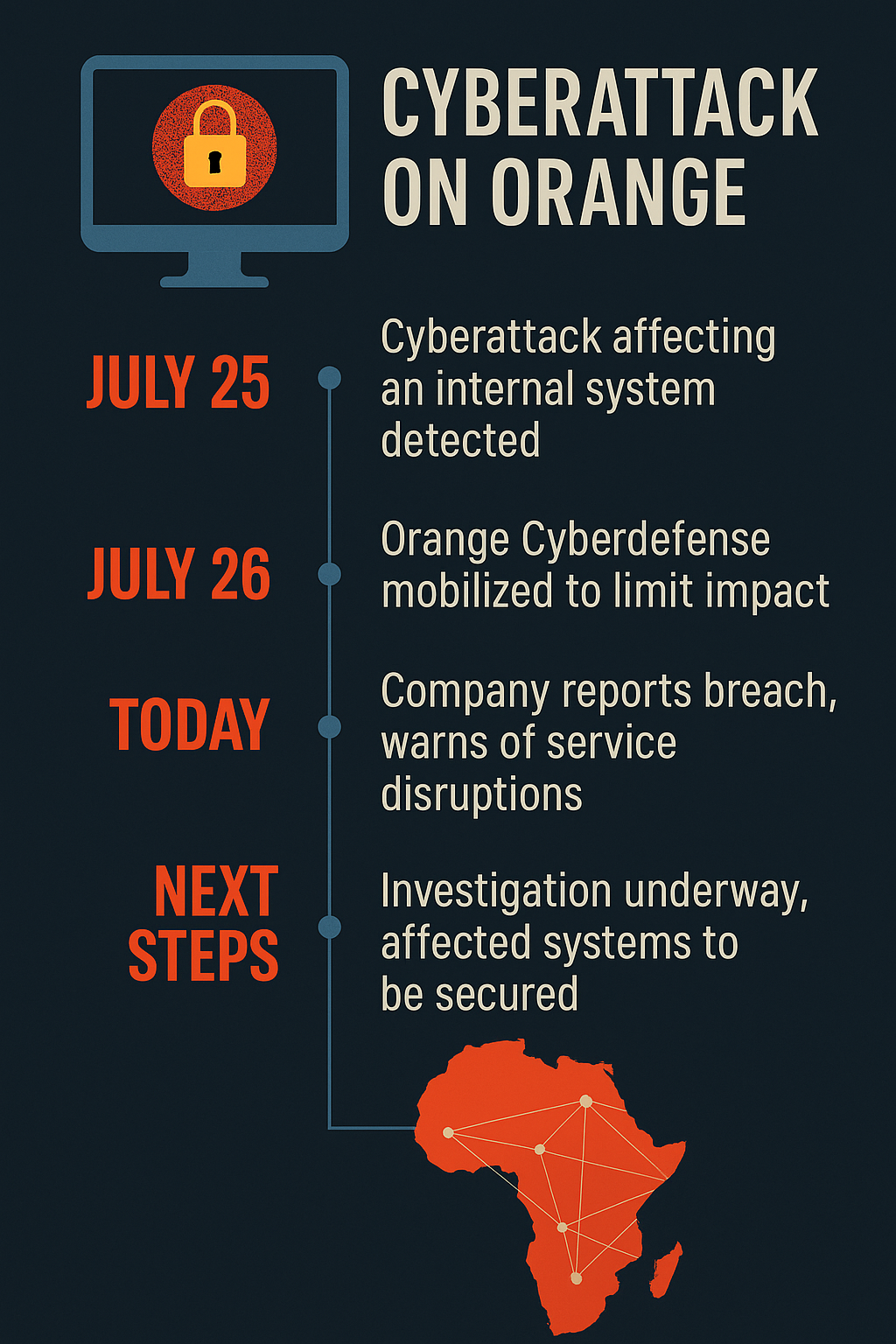


France’s largest telecom provider confirms internal system breach; customers warned of service disruptions as cybersecurity teams race to contain threat Paris — August 1, 2025In a...



A new Chrome security feature, Device Bound Session Credentials (DBSC), links session cookies to specific hardware, blocking malware-driven hijacks. Google’s transparency push via Project Zero further...



Hackers Exploited Cloud Misconfiguration and API Weaknesses to Breach the Viral Red-Flag Dating App Used by Thousands of Women July 28, 2025 | MAG212NEWS In a...


Unpatched firewalls exposed thousands of networks worldwide. Experts warn of growing risk to small businesses and government agencies from remote code execution flaws. 🌐 July 27,...