


Security experts urge a shift from once-a-year audits to continuous 24/7 defense. Organizations are being pushed to build “Offensive SOC” teams that hunt threats proactively, aligning...



CISA and FBI raise red flags about a new ransomware strain crippling essential services while urging critical sectors to adopt robust defense strategies. Washington D.C. |...


Chinese-state hackers allegedly exploited a SharePoint zero-day to breach the U.S. National Nuclear Security Administration (NNSA), prompting urgent calls for patching, segmentation, and zero-trust enforcement. 🔍...



Chinese state-linked hackers reportedly infiltrated the National Nuclear Security Administration via a SharePoint zero-day vulnerability, sparking urgent questions about America’s digital safeguards. 🗓 July 23, 2025...



Dissecting the internals of modern credential theft campaigns with command-line insights, evasion techniques, and real-world behavior. 🧬 Introduction In 2025, cybercriminals are no longer relying on...
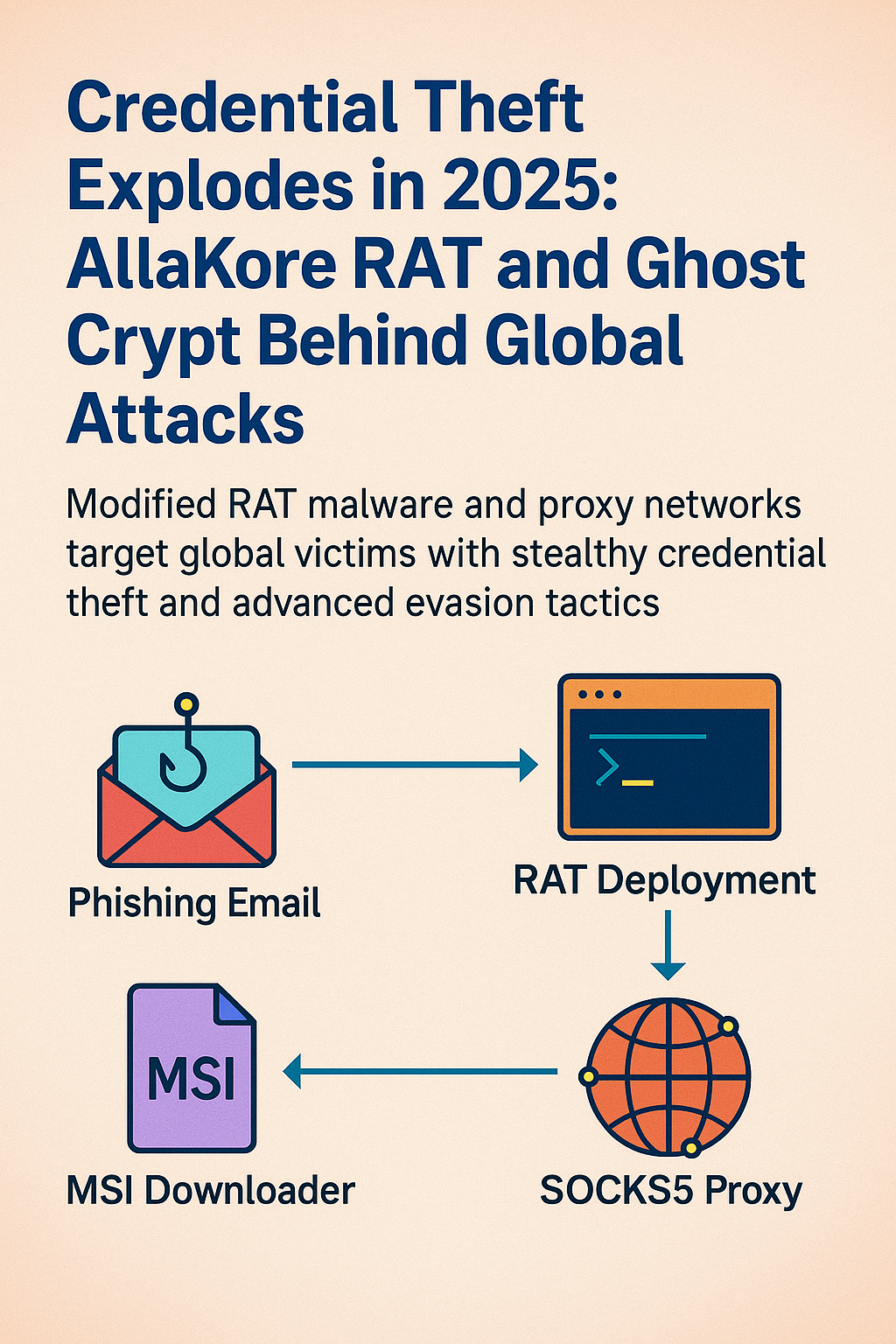


Modified RAT malware and proxy networks target global victims with stealthy credential theft and advanced evasion tactics. When María López clicked to “Update Policy,” she unwittingly...


A coordinated cyberattack led by Moroccan hacker Jokeir 07x and groups Dark Hell 07x and Dr. Shell 08x compromises key Tunisian institutions, exposing government systems, banking...



Newly discovered DCHSpy malware exploits system accessibility to spy on Android users, with links to Iran’s cyber apparatus raising regional and global surveillance concerns. Iran-Linked DCHSpy...



TADTS under scrutiny for delayed breach notification as ransomware group leaks trove of sensitive personal data, igniting legal backlash and public outrage. Texas Alcohol & Drug...



As cyberattacks grow in scale and complexity, leading cybersecurity firms are turning to cutting-edge attack simulation tools like SafeBreach, XM Cyber, and CALDERA to preempt threats,...