


Minnesota’s capital city shuts down all IT systems after a “sophisticated, coordinated” cyberattack overwhelms local defenses. FBI, DHS, and National Guard step in. MAG212NEWS St. Paul,...


Unpatched firewalls exposed thousands of networks worldwide. Experts warn of growing risk to small businesses and government agencies from remote code execution flaws. 🌐 July 27,...


Newly discovered CrushFTP flaw enables threat actors to bypass authentication and access sensitive files, prompting urgent calls for immediate patching and global security reviews. Hackers Exploit...
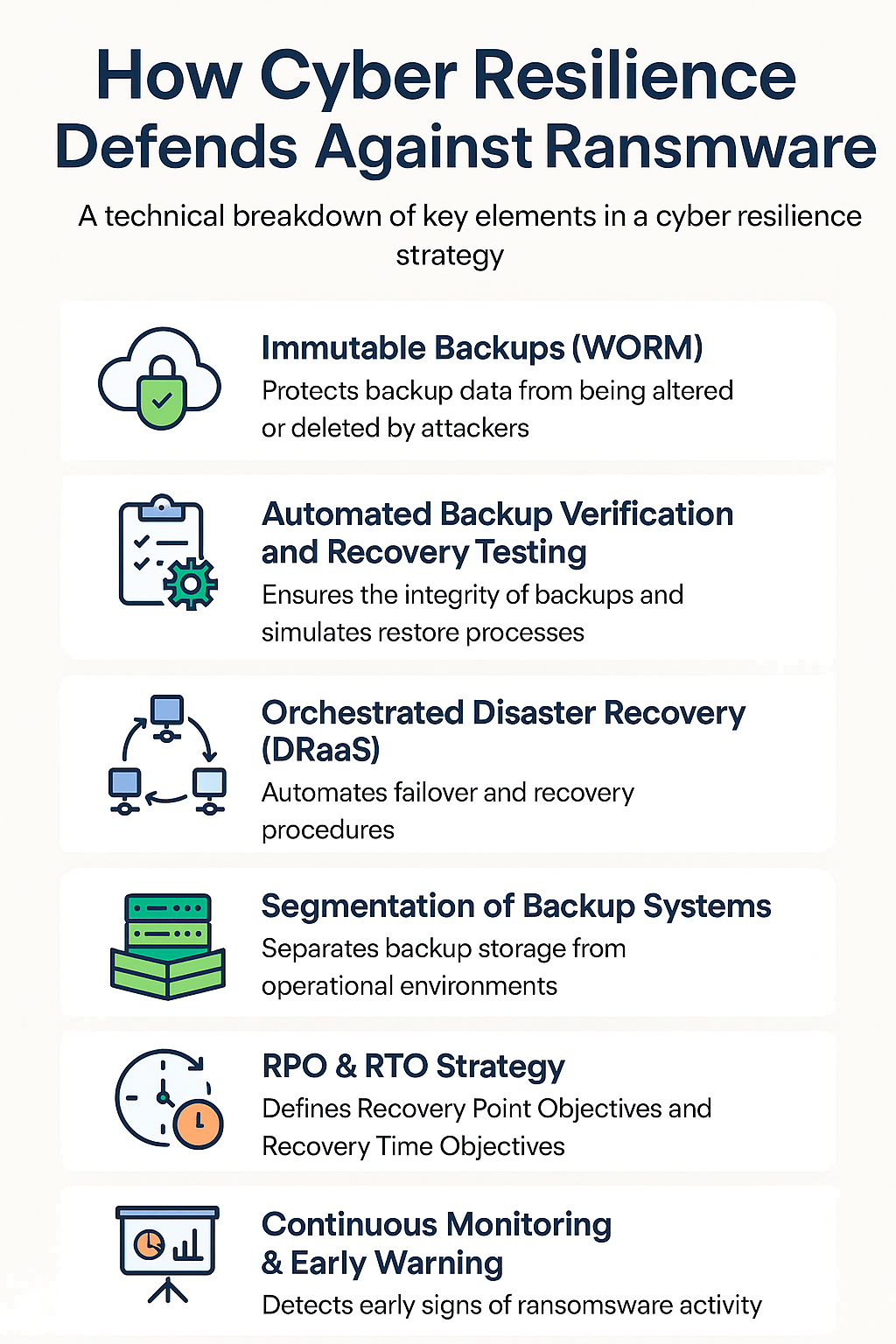


As ransomware actors escalate attacks on backups and recovery systems, IT leaders worldwide are pivoting from traditional backup strategies to holistic cyber resilience frameworks to safeguard...


Cybercriminals exploit popular communication tools to distribute sophisticated malware, prompting urgent calls for reinforced digital hygiene and international cooperation. A Silent Threat Delivered with a Click:...

From smart cities to hospitals and energy grids, the integration of digital and physical systems brings efficiency—and unprecedented vulnerabilities. Experts warn Morocco and other nations must...



Two critical VMware vCenter vulnerabilities, CVE-2024-38812 and CVE-2024-38813, are actively being exploited after Broadcom’s initial patch efforts fell short. These flaws, impacting a vital tool for...