


Strategic Project to Boost Trade and Land Connectivity Across West Africa with Chinese Financing Ouagadougou – From Our International CorrespondentIn what is being hailed as a...
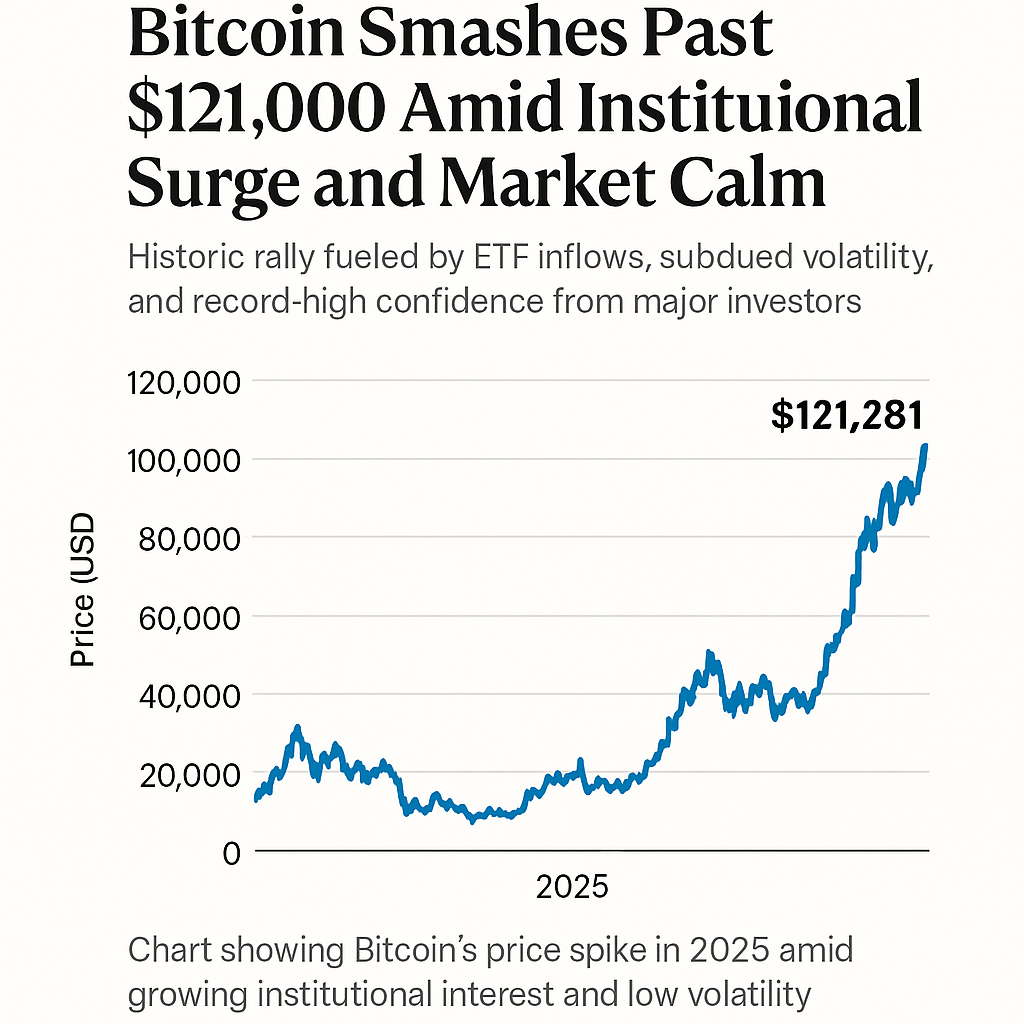


Historic rally fueled by ETF inflows, subdued volatility, and record-high confidence from major investors. In a landmark moment for the cryptocurrency market, Bitcoin has shattered the...



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...



A declassified French intelligence telegram reveals covert cooperation between Algiers and Madrid in the tense months following Algerian independence—raising new questions about Cold War geopolitics in...



From cryptographic signing to hardened base images, a new security webinar unpacks the real-world tactics to stop supply-chain breaches targeting Python’s vast open-source ecosystem. The command...


A coordinated supply‑chain campaign dating from March 2023 has unleashed 60 rogue Ruby gems—and unknown Python packages—disguised as benign tools, siphoning credentials and crypto data, triggering...



OpenAI’s chief, Sam Altman, warns that artificial intelligence could soon unleash an era of “information chaos,” threatening trust, truth, and global cybersecurity stability. Society Is Not...



OpenAI’s GPT-5 launch marks a turning point in artificial intelligence, promising unprecedented power and igniting fierce competition in the AI industry. GPT-5’s Game-Changing Debut “We are...



International defense contractor SOSi warns of a wave of fraudulent job offers targeting job seekers online; urges vigilance and outlines how to verify authentic recruitment communications....



Washington now offers one of the largest rewards in history for information leading to the capture of the embattled Venezuelan leader, accused of major cocaine trafficking...