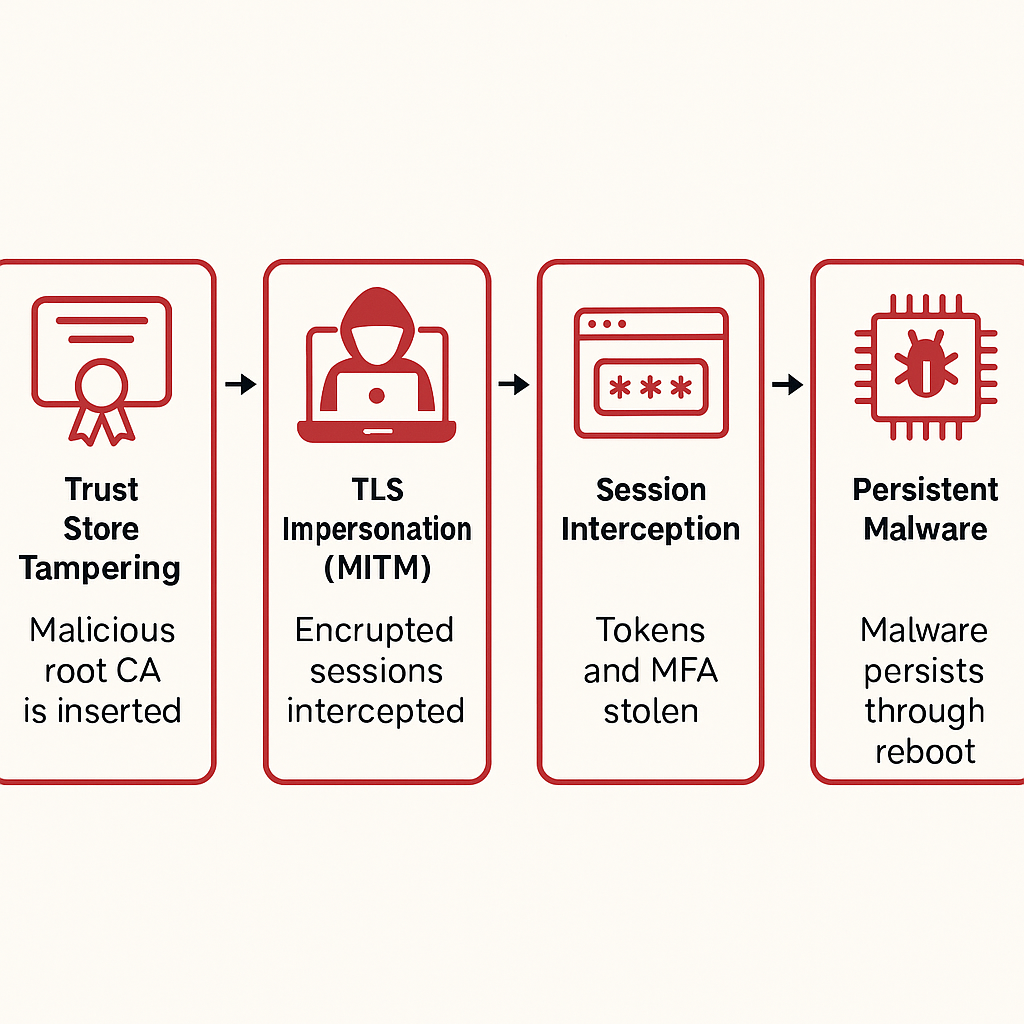


Secret Blizzard’s embassy campaign shows why device trust beats TLS trust alone—and how to harden firmware, keys, and boot chains A new expert analysis warns that...



From cryptographic signing to hardened base images, a new security webinar unpacks the real-world tactics to stop supply-chain breaches targeting Python’s vast open-source ecosystem. The command...