
Dassault Systèmes patches severe vulnerability in Apriso manufacturing software that could let attackers bypass authentication and compromise factories worldwide. A newly disclosed flaw, tracked as CVE-2025-5086,...
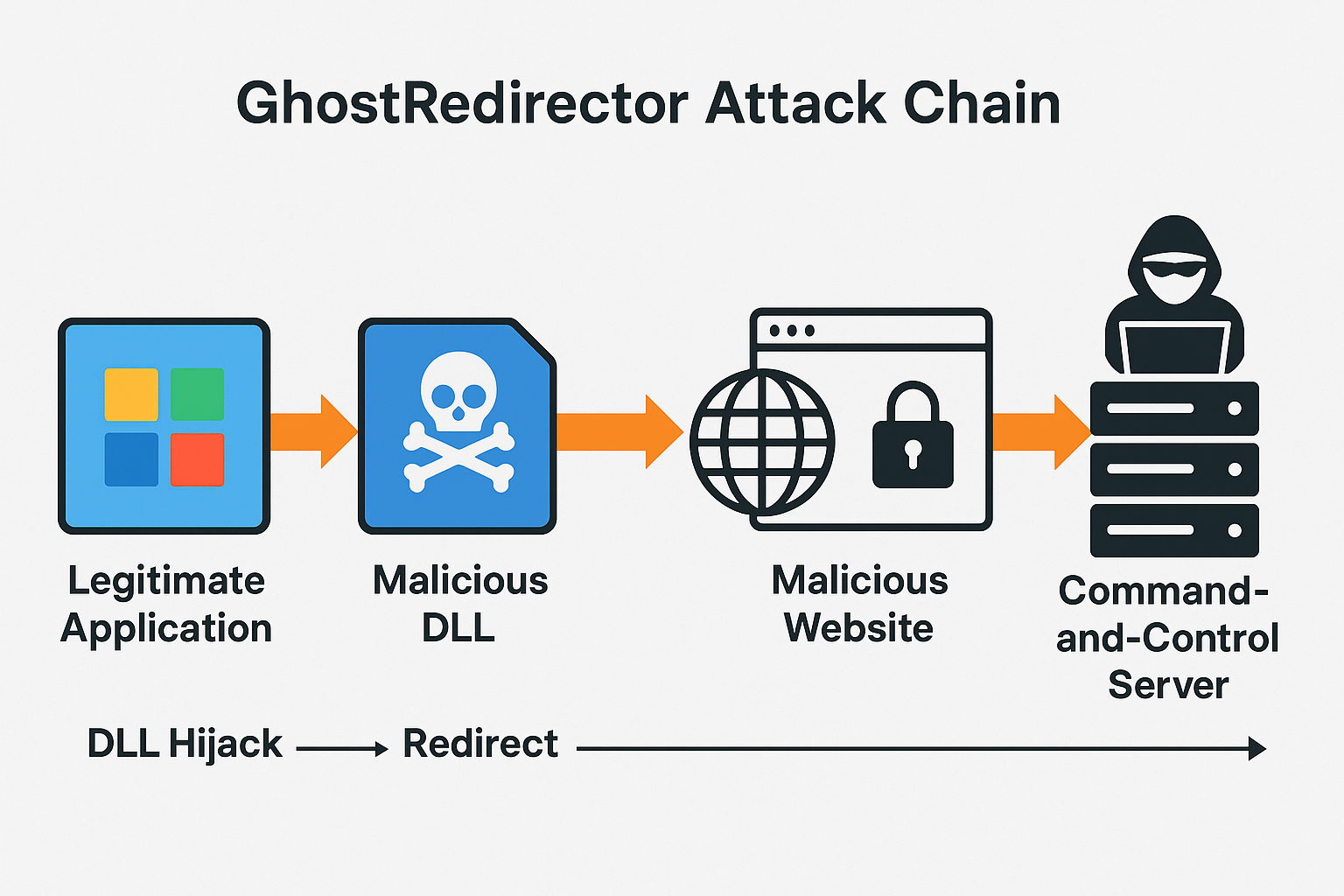


Cybercriminals abuse trusted Windows executables to redirect users, spread malware, and harvest sensitive data. A new malware campaign dubbed GhostRedirector has compromised more than 65 legitimate...
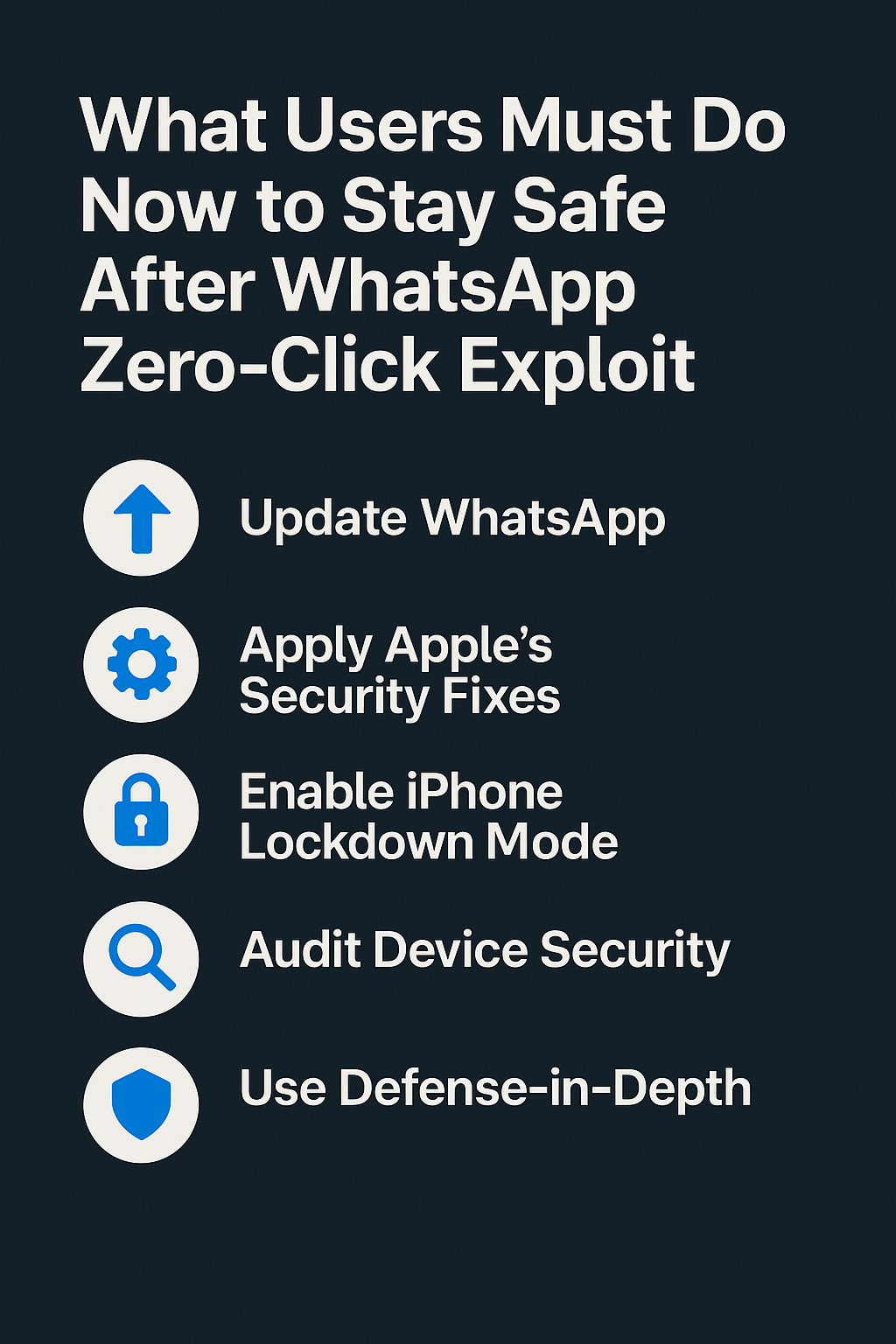


Update Immediately to Block CVE-2025-55177 WhatsApp has released patched versions for iOS and macOS (2.25.21.73 and later for iOS, 2.25.21.78 for Mac). Users should update immediately...



Meta fixes actively exploited flaw chained with recent Apple bug; high-risk users urged to update immediately Meta has shipped an emergency WhatsApp update to fix CVE-2025-55177,...
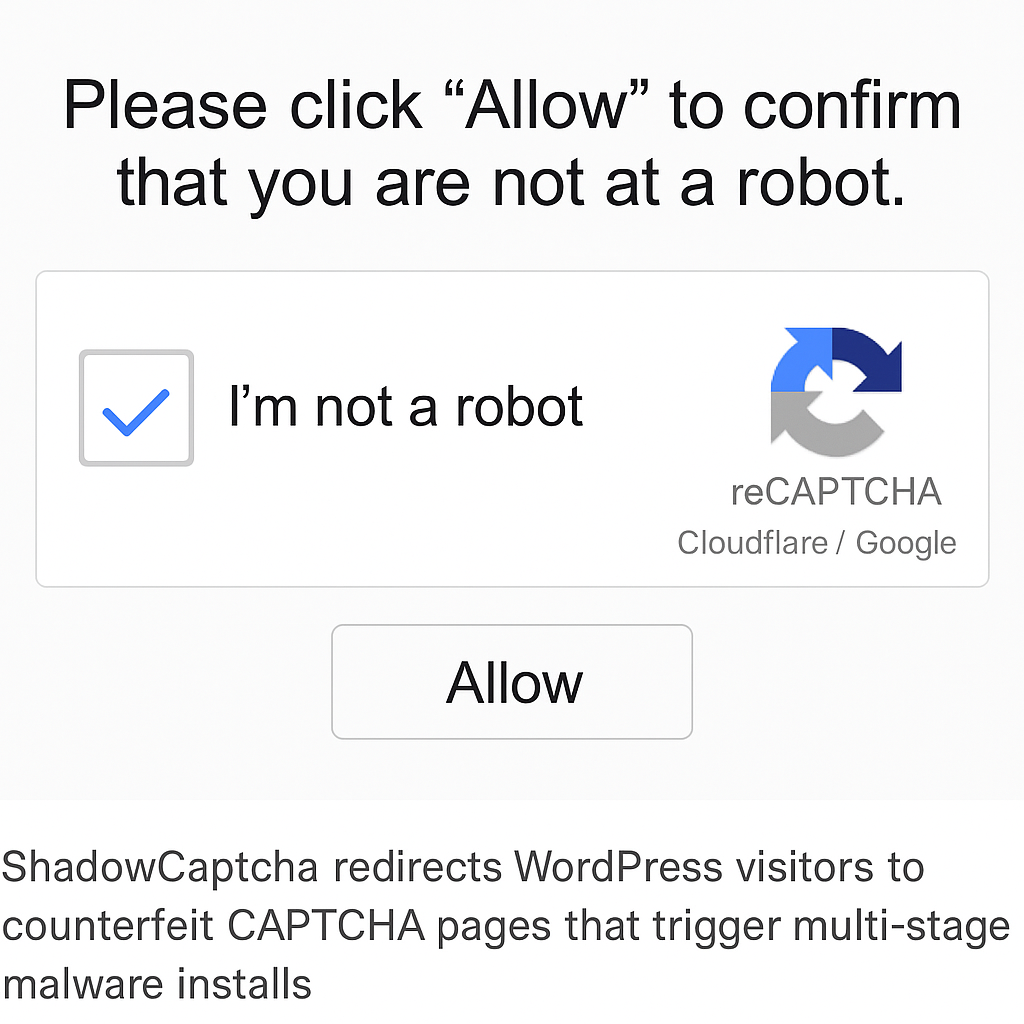


Over 100 hacked WordPress sites redirect visitors to fake Cloudflare/Google CAPTCHA pages using “ClickFix” to execute Lumma, Rhadamanthys, Epsilon Red, and XMRig payloads, researchers say. A...
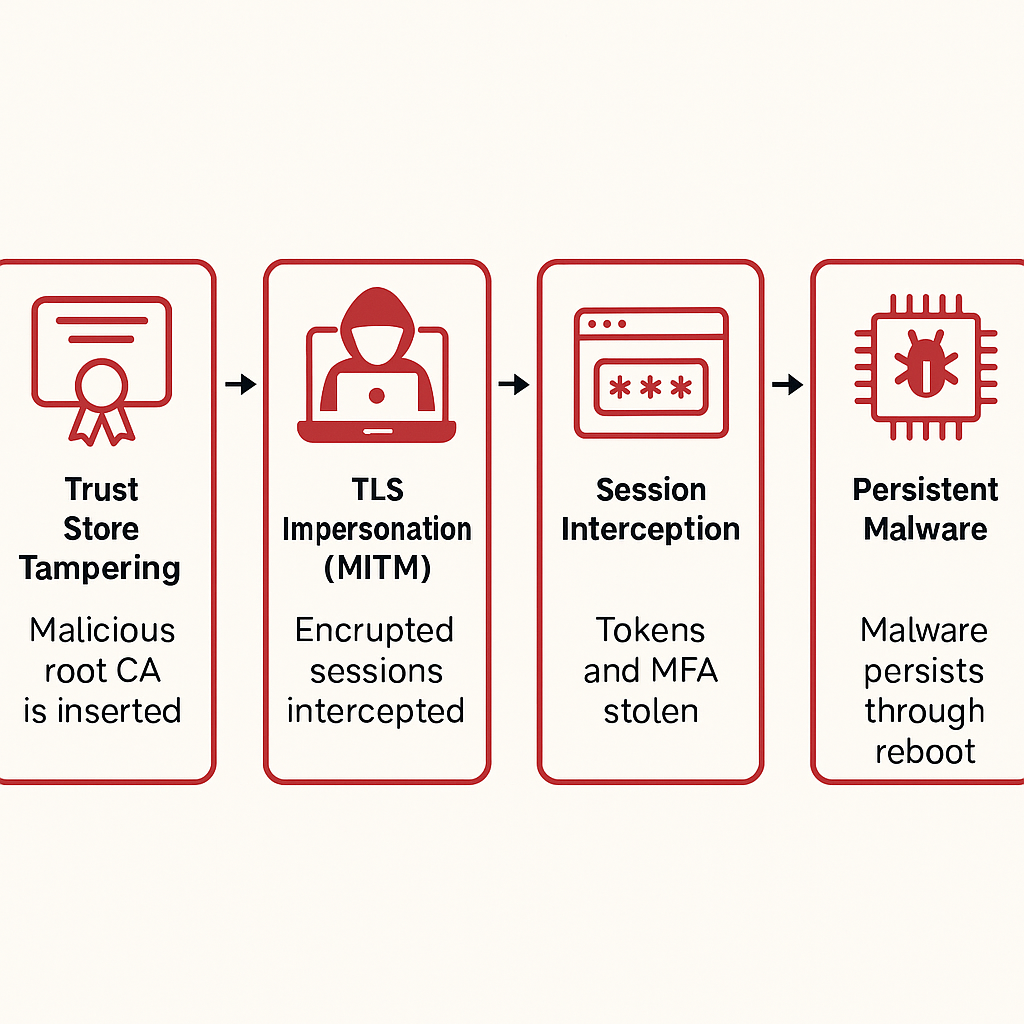


Secret Blizzard’s embassy campaign shows why device trust beats TLS trust alone—and how to harden firmware, keys, and boot chains A new expert analysis warns that...
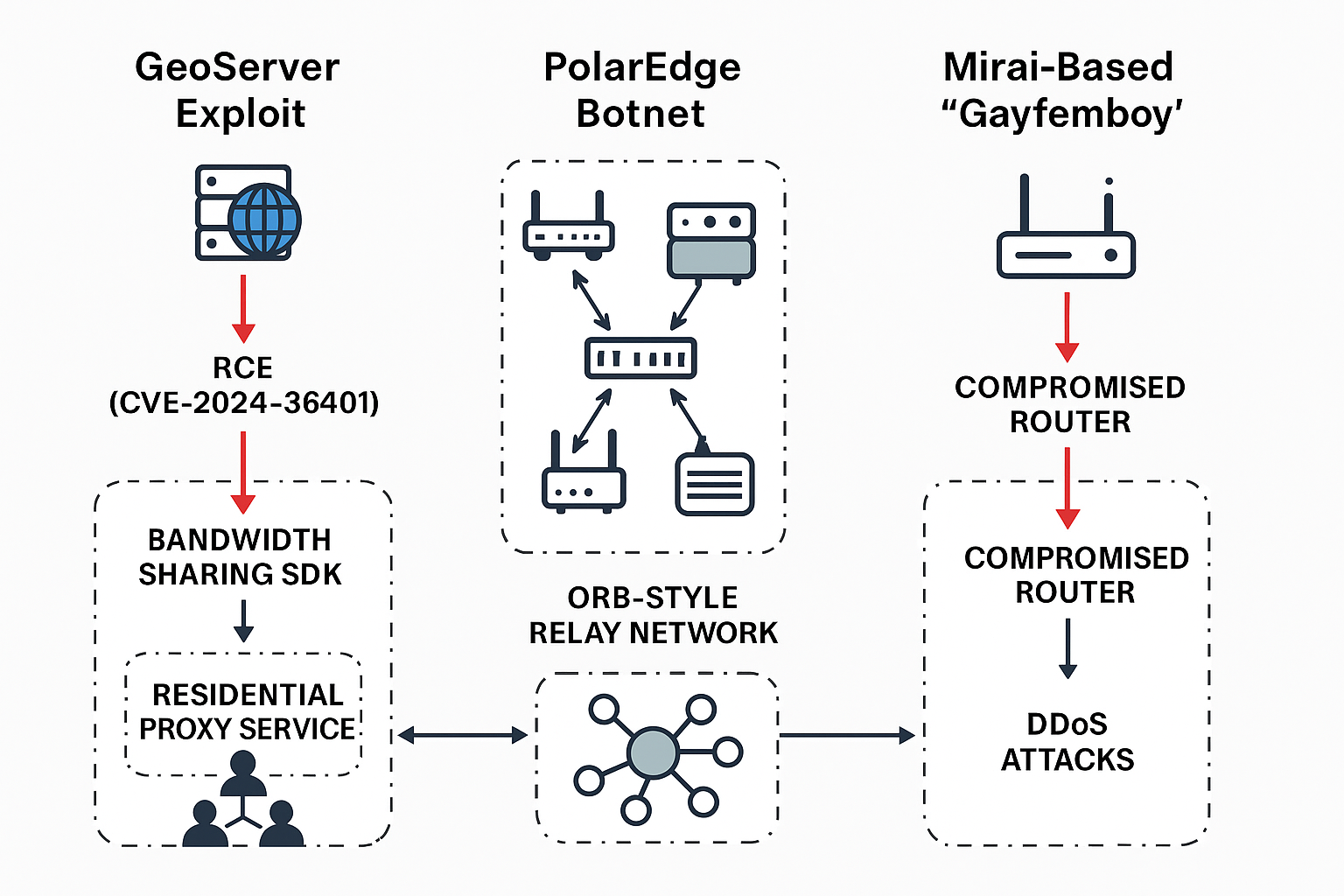


ORB-style relay networks, SDK-based bandwidth theft, and Mirai spin-offs fuel a new wave of silent monetization and stealthy ops Excerpt (40–60 words)Attackers are chaining a critical...
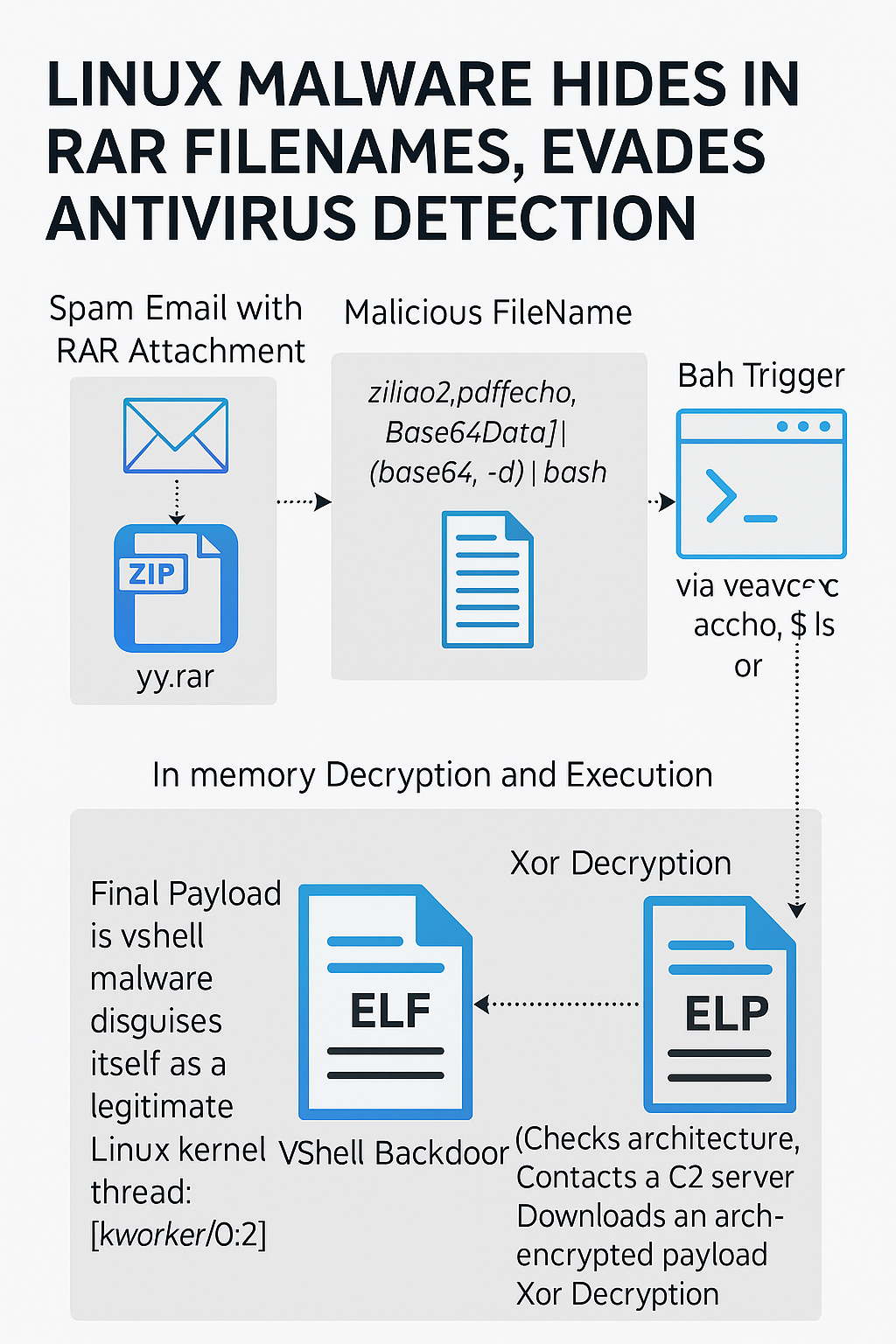


Trellix says a phishing campaign weaponizes RAR archive filenames to auto-trigger Bash, fetch a multi-arch loader, and execute the VShell backdoor entirely in memory. A new...



Threat actors abuse misconfigurations and living-off-the-land tools—using fake 404 pages and panda JPEG “polyglot” files—to drop miners on Linux and Windows at scale. Twin campaigns dubbed...



Two-day February intrusion leaked financial and medical details; group begins notifications and offers credit monitoring as regulators are alerted. The Business Council of New York State...