


Fresh vulnerabilities in the TETRA standard allow attackers to replay calls, brute-force encryption, and inject fake voice/data—even on “secure” networks. No universal fixes exist, leaving critical...


A zero-day flaw (CVE-2025-8088) is under active attack by Russian-linked groups Paper Werewolf and RomCom. Booby-trapped archives can plant malware in Windows startup folders—silently hijacking your...



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...



Cybercrime syndicate UNC6040 used spoofed IT helpdesk calls and legitimate remote access tools to infiltrate corporate environments—Google TAG reveals ongoing threat to global organizations. SEO-Optimized Excerpt:Google’s...
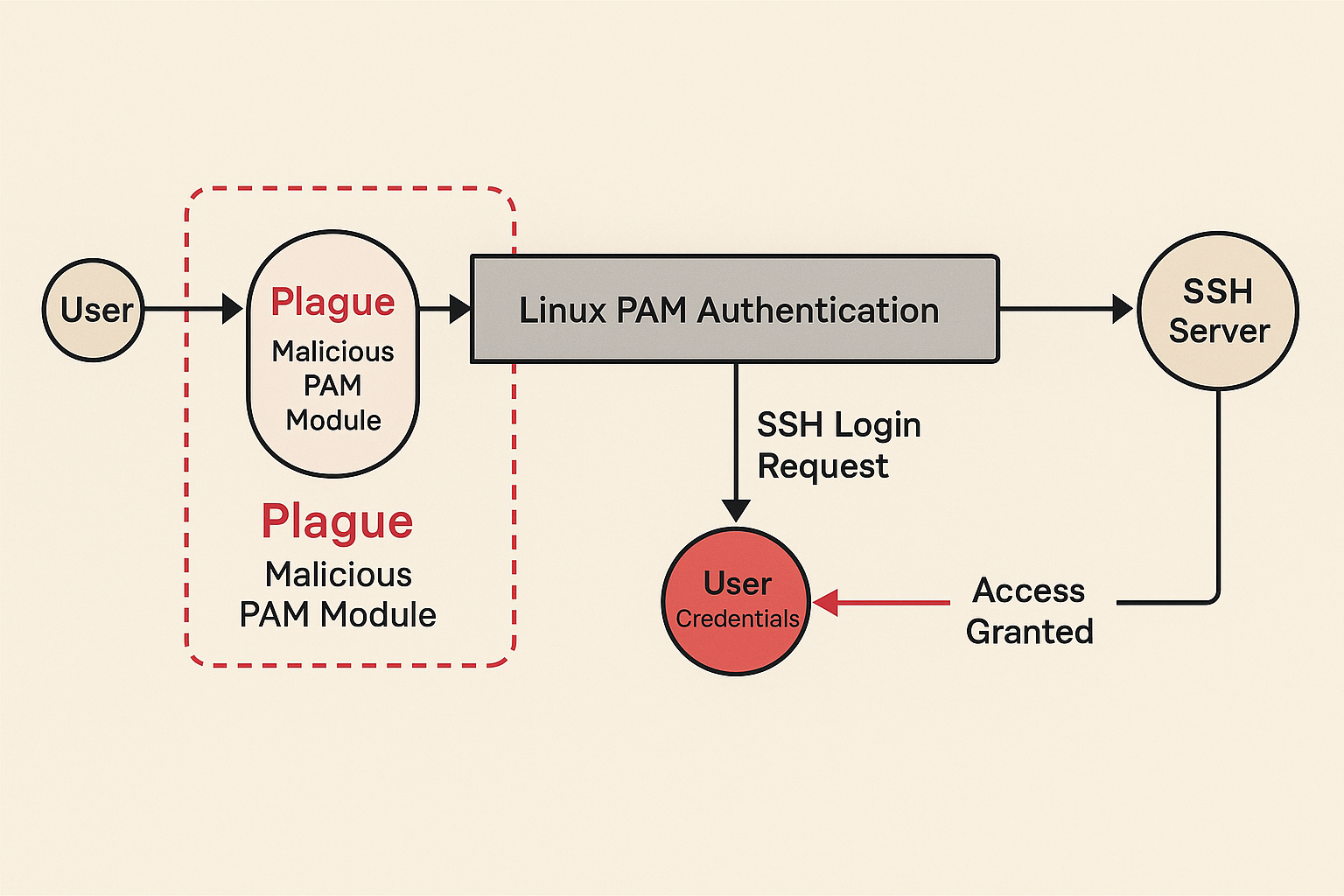


A newly discovered malicious PAM module named “Plague” stealthily hijacks SSH logins, bypasses Linux authentication, and evades antivirus—threatening enterprise servers worldwide with root-level backdoors. It didn’t...


Unpatched firewalls exposed thousands of networks worldwide. Experts warn of growing risk to small businesses and government agencies from remote code execution flaws. 🌐 July 27,...



New cross-platform malware strains abuse PostgreSQL, Tomcat, JupyterLab, and Confluence to hijack compute power for cryptocurrency mining—leaving cloud workloads vulnerable and detection difficult. 🧨 Introduction: Clouds...



CISA and FBI raise red flags about a new ransomware strain crippling essential services while urging critical sectors to adopt robust defense strategies. Washington D.C. |...
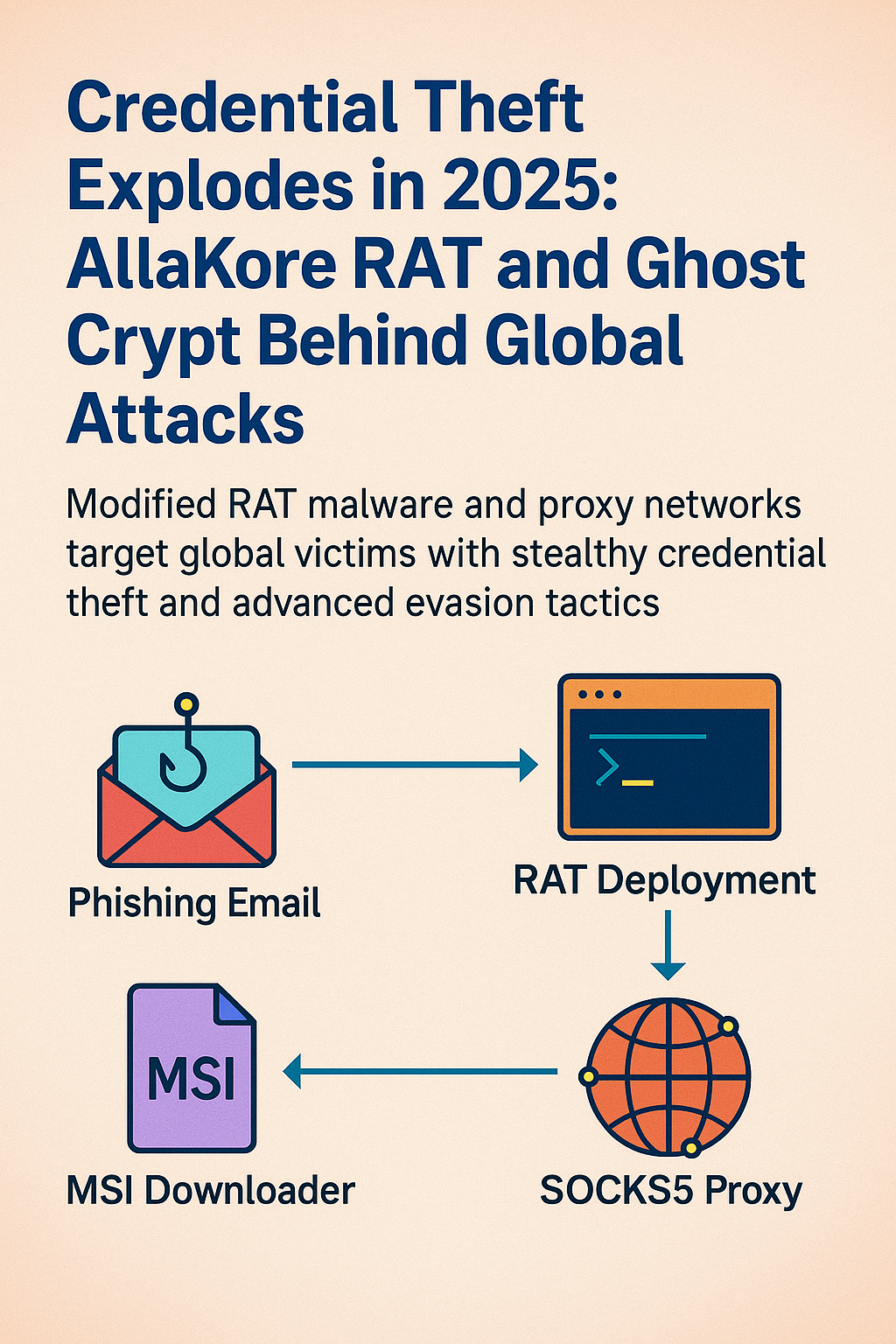


Modified RAT malware and proxy networks target global victims with stealthy credential theft and advanced evasion tactics. When María López clicked to “Update Policy,” she unwittingly...
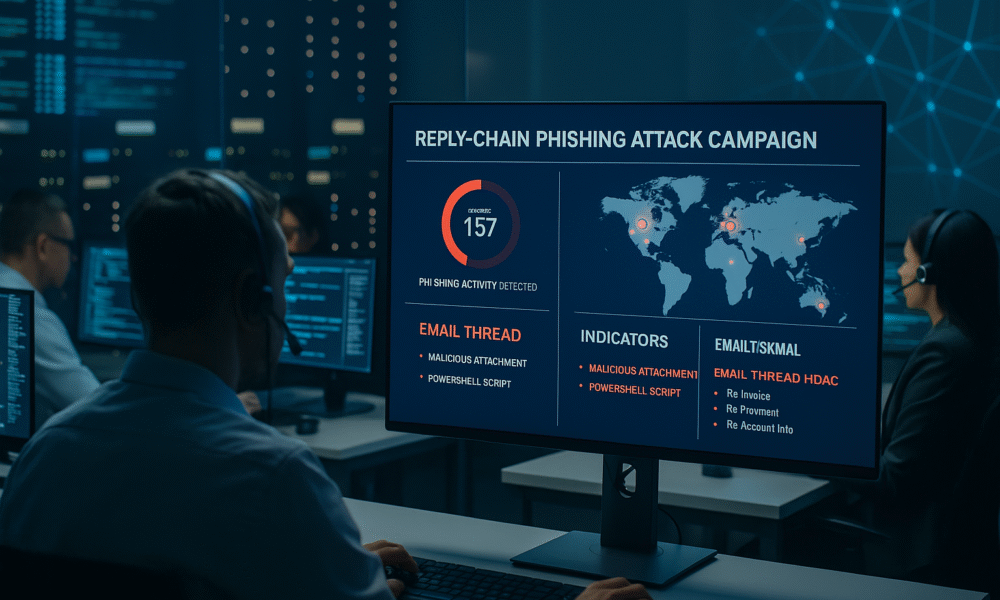


Cybercriminals are using fileless malware embedded in email chains to bypass security systems, compromising businesses and individuals across multiple sectors. “Reply Chain” Malware Attacks Infiltrate Email...