
Dassault Systèmes patches severe vulnerability in Apriso manufacturing software that could let attackers bypass authentication and compromise factories worldwide. A newly disclosed flaw, tracked as CVE-2025-5086,...
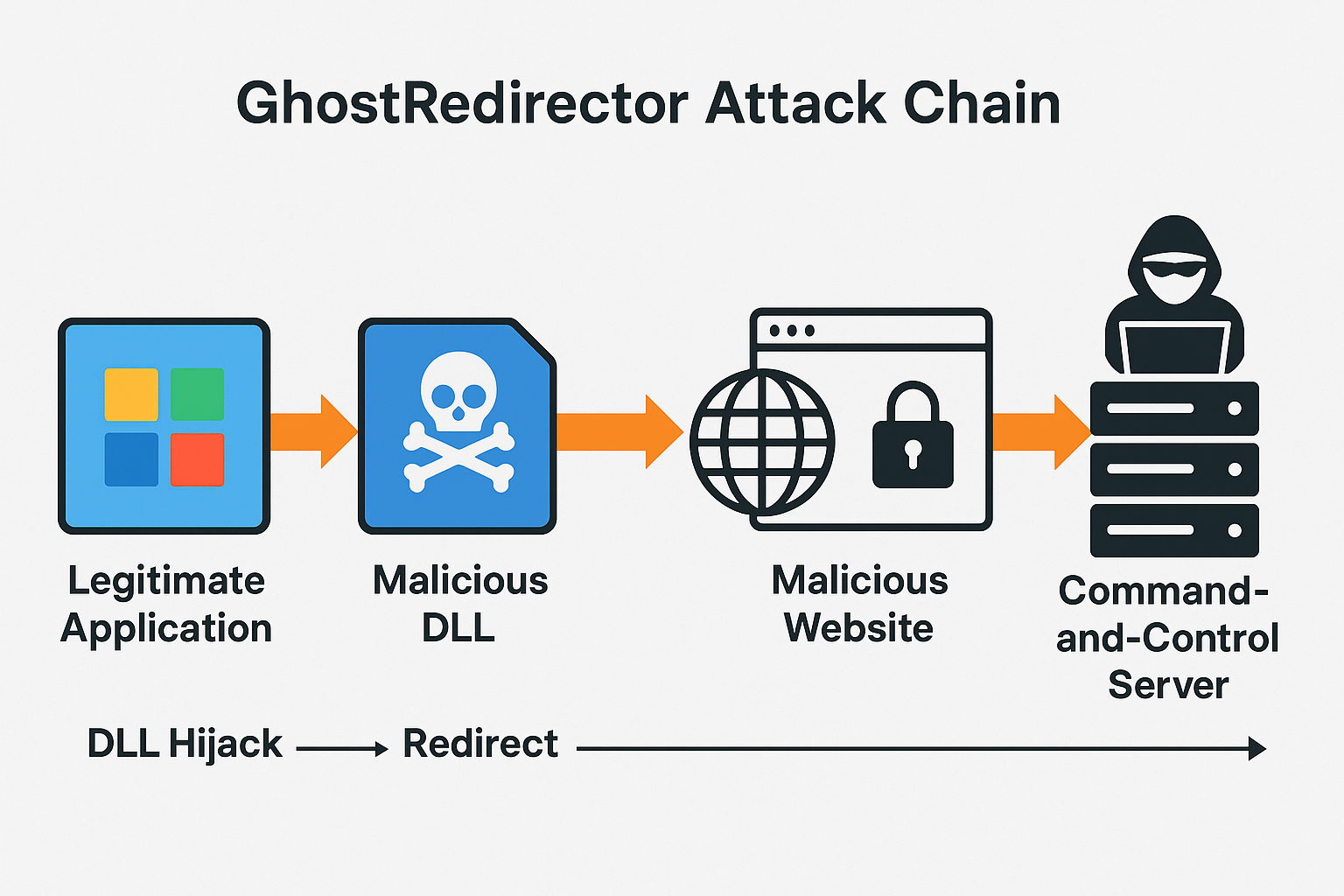


Cybercriminals abuse trusted Windows executables to redirect users, spread malware, and harvest sensitive data. A new malware campaign dubbed GhostRedirector has compromised more than 65 legitimate...



Wiz Research finds an exposed ClickHouse database with 1M+ log lines, including chat histories and secrets—spotlighting human error, weak access controls, and the need for DLP....
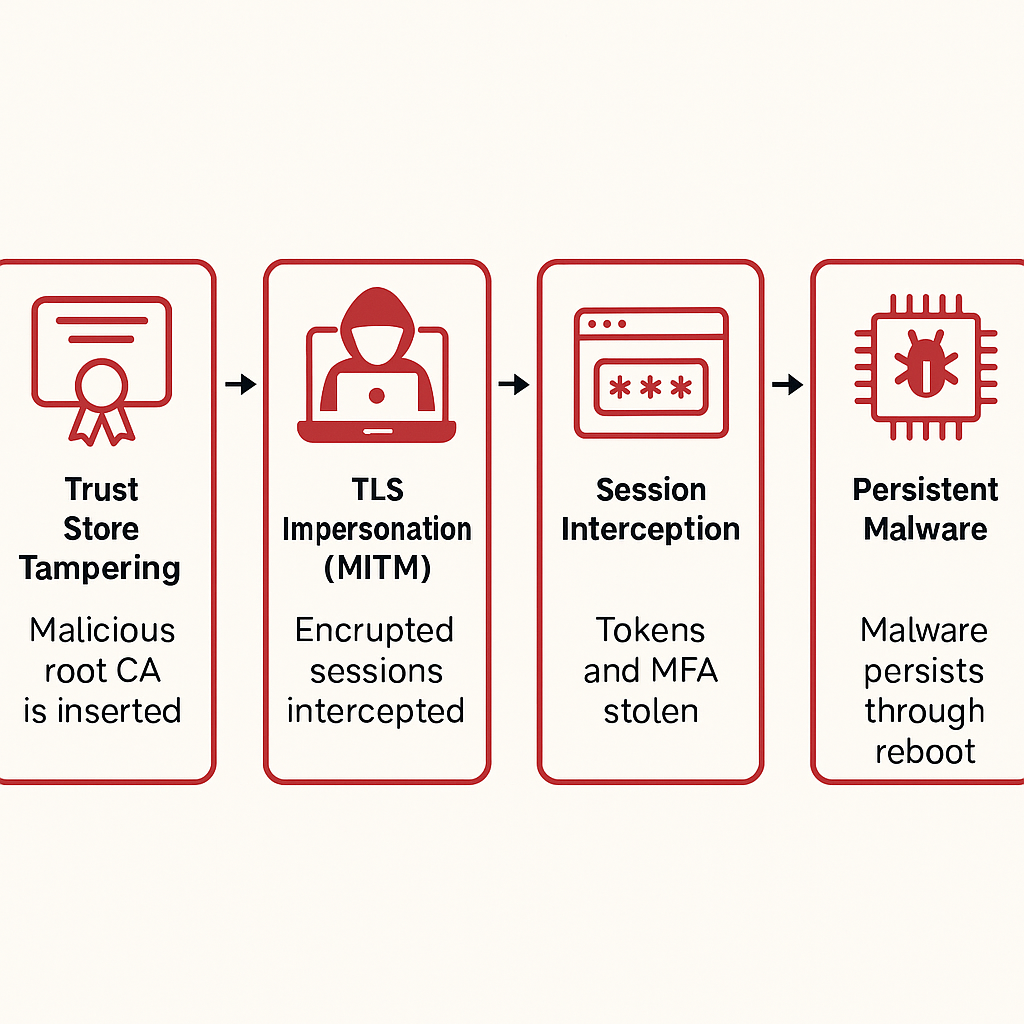


Secret Blizzard’s embassy campaign shows why device trust beats TLS trust alone—and how to harden firmware, keys, and boot chains A new expert analysis warns that...
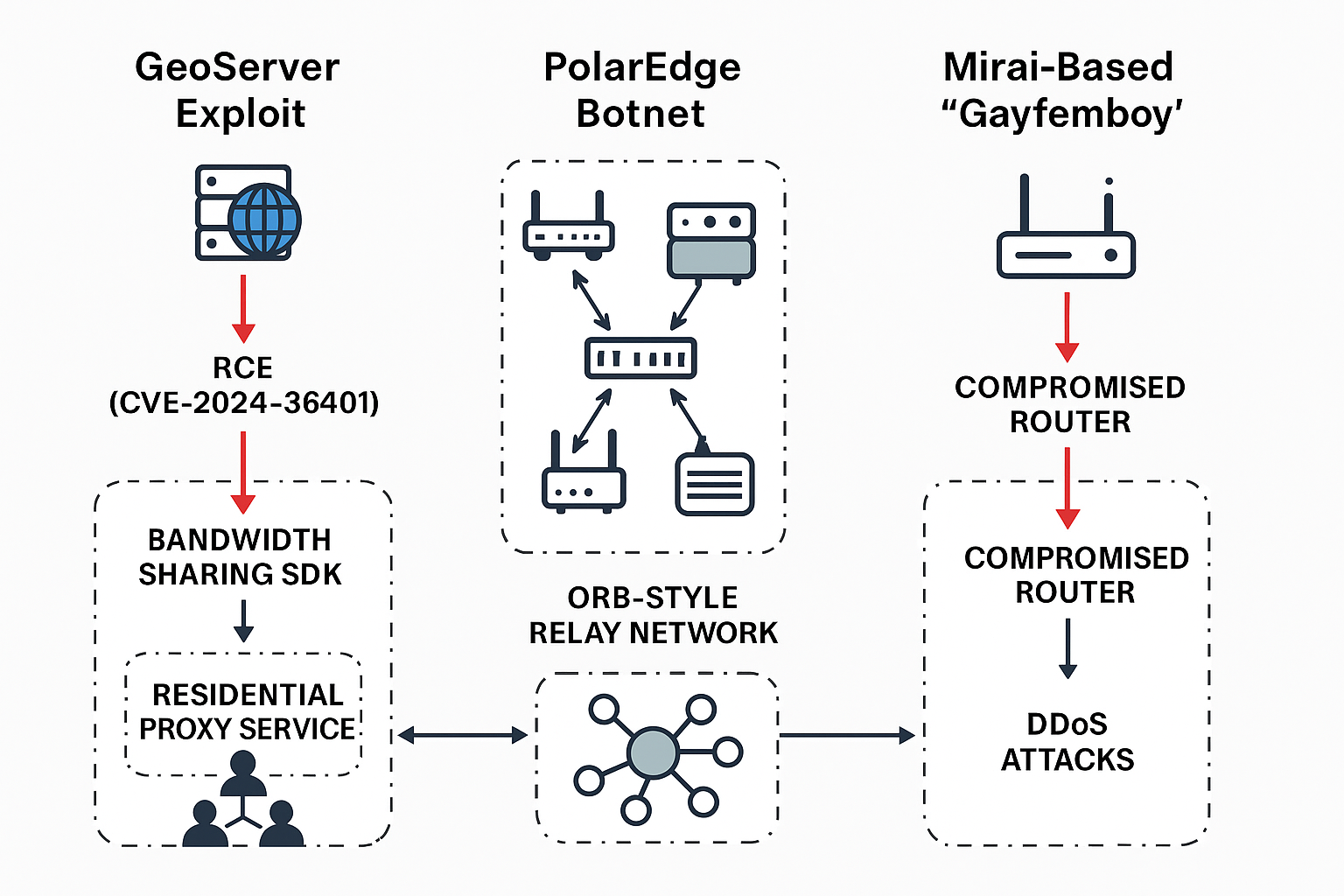


ORB-style relay networks, SDK-based bandwidth theft, and Mirai spin-offs fuel a new wave of silent monetization and stealthy ops Excerpt (40–60 words)Attackers are chaining a critical...



Threat actors abuse misconfigurations and living-off-the-land tools—using fake 404 pages and panda JPEG “polyglot” files—to drop miners on Linux and Windows at scale. Twin campaigns dubbed...



Two-day February intrusion leaked financial and medical details; group begins notifications and offers credit monitoring as regulators are alerted. The Business Council of New York State...



Leaked SIM and PUK data heighten SIM-swapping risks as critics fault Orange’s response; company says no passwords, emails or banking data were taken. Orange Belgium disclosed...



Attackers use CVE-2023-46604 to breach Linux cloud hosts, drop “DripDropper” malware, and quietly fix the flaw to lock in access, researchers say. Threat actors are abusing...


Colt Technology Services’ internal systems remain down after a suspected ransomware attack; WarLock gang claims to have stolen 1 million documents, demanding $200K ransom Colt Technology...