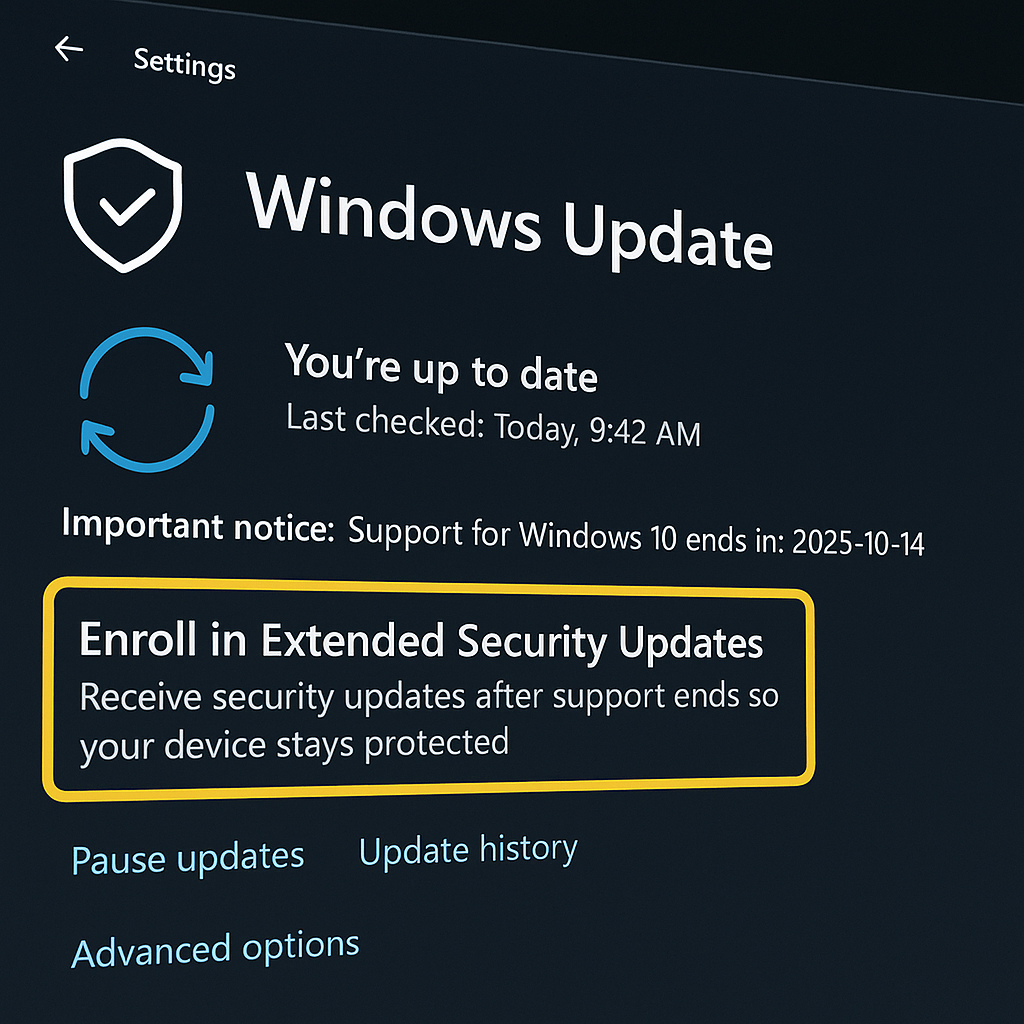


Free support ends October 14, 2025; new KB5063709 unlocks Extended Security Updates enrollment to keep critical patches flowing through October 2026. Microsoft is warning Windows 10...



Russian-linked group EncryptHub is impersonating IT staff on Microsoft Teams, walking victims into remote sessions, then abusing CVE-2025-26633 (“MSC EvilTwin”) to execute rogue .msc consoles and...

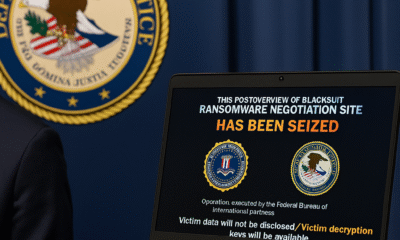

Law enforcement seized four servers, nine domains, and about $1.09M in crypto linked to the Royal/BlackSuit operation, following a July 24 takedown coordinated with eight countries....
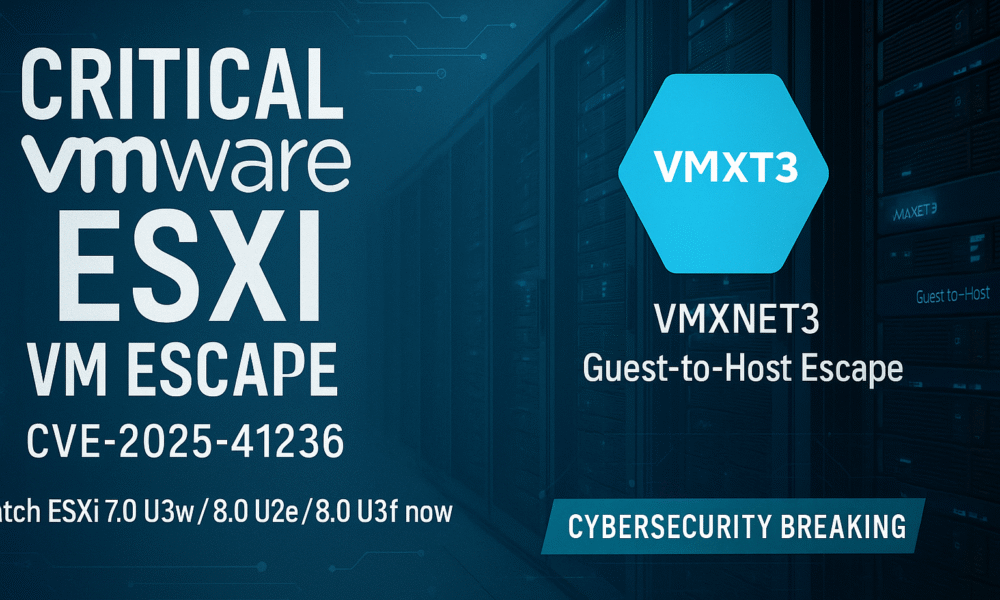

Broadcom/VMware patches CVE-2025-41236 in ESXi 7.x/8.x, but Shadowserver counts show slow remediation as thousands of internet-reachable hosts remain on vulnerable builds. A critical integer-overflow flaw (CVE-2025-41236)...



Phone, email, and website went dark as investigators probe links to widely exploited Citrix NetScaler flaws. The Pennsylvania Attorney General’s Office says a cyberattack disabled its...

Hackers claim “full system compromise,” say all servers were encrypted and backups wiped; company has not confirmed the incident as investigators assess potential operational impact Royal...



The sharp rise in stolen login data is driven by infostealer-as-a-service, AI-powered phishing, and automated credential stuffing—making compromised accounts the fastest-growing breach vector of 2025. The...



From cryptographic signing to hardened base images, a new security webinar unpacks the real-world tactics to stop supply-chain breaches targeting Python’s vast open-source ecosystem. The command...



New report reveals ransomware actors are evolving from simple encryption to layered attacks—leveraging artificial intelligence, physical intimidation, and operational shutdowns to break victims faster than ever...



Cybercrime syndicate UNC6040 used spoofed IT helpdesk calls and legitimate remote access tools to infiltrate corporate environments—Google TAG reveals ongoing threat to global organizations. SEO-Optimized Excerpt:Google’s...